Image Credit: Naor Hodorov
Security researcher Naor Hodorov has recently published an analysis of a vulnerability discovered in AnyDesk, a popular remote administration software. This vulnerability, identified as CVE-2024-12754, could allow a low-privileged user to gain elevated access and potentially take complete control of a system.
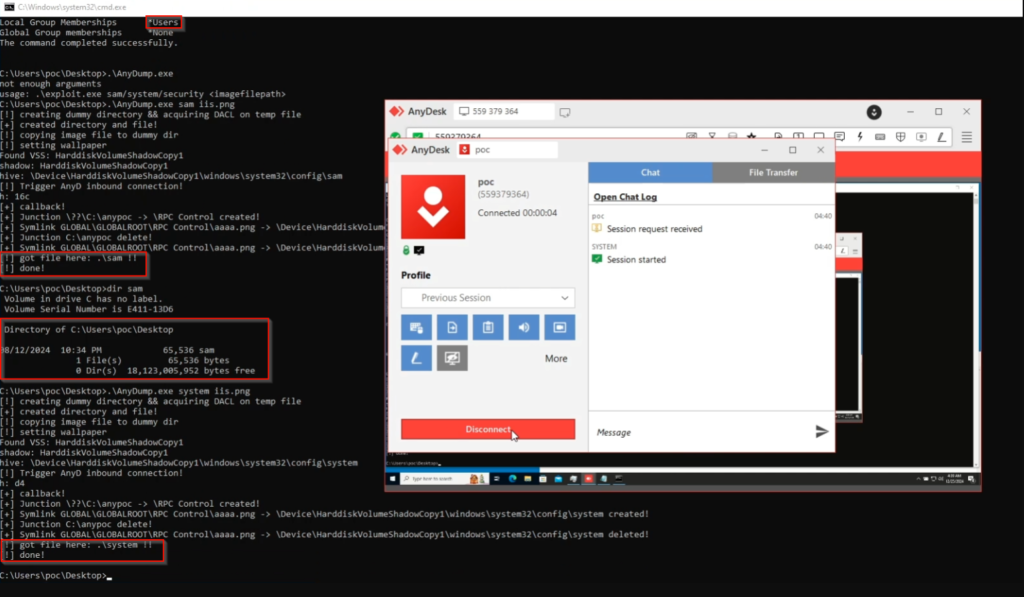
The vulnerability stems from an elevated arbitrary file read/copy operation performed by the AnyDesk service as NT AUTHORITY\SYSTEM. In simpler terms, the service, running with the highest system privileges, can copy any file to a location accessible by low-privileged users, potentially overwriting existing files and retaining the original ownership and permissions.
Hodorov explains that a low-privileged user can set their background image, which is then copied by the AnyDesk service to the C:\Windows\Temp directory. The copied file retains the original file name and is owned by NT AUTHORITY\SYSTEM. By default, low-privileged users have limited access to C:\Windows\Temp, but they can create and write files in this directory.
This combination of factors allows an attacker to pre-create a file with the same name as the target file in C:\Windows\Temp. When the AnyDesk service copies the background image, it overwrites the pre-created file, effectively granting the attacker ownership of the file with NT AUTHORITY\SYSTEM privileges.
Hodorov demonstrates how this vulnerability can be exploited to gain local privilege escalation by targeting sensitive system files like SAM, SYSTEM, and SECURITY, which are typically only accessible by the system and administrators. By leveraging the vulnerability to gain control of these files, an attacker could potentially extract user credentials and gain complete control of the system.
The CVE-2024-12754 vulnerability was patched in AnyDesk version v9.0.1. Users are strongly encouraged to update to the latest version to protect themselves from potential attacks.
This vulnerability highlights the importance of understanding and mitigating security risks associated with software used for remote administration. As Hodorov notes, “A low privileged user on Windows can set its own background image, therefore we control the source of the file to be copied on demand.” This seemingly innocuous feature, when combined with other system mechanics, can be exploited to gain unauthorized access.
For those interested in the technical details, a Proof-of-Concept (PoC) exploit is available on GitHub. Users and administrators should take this vulnerability seriously and apply the necessary patches as soon as possible.
Related Posts:
- Oracle VirtualBox Elevation of Privilege Vulnerability (CVE-2024-21111): PoC Published
- AnyDesk’s Cybersecurity Breach: Unveiling the Recent Attack
- AnyDesk Breach 2024: Dark Web Sale of 18,317 Credentials
- Cybercriminals Exploit AnyDesk to Impersonate CERT-UA in Sophisticated Phishing Campaign
- Beware of Fake Downloads: AsyncRAT Spreads via Popular Software Cracks