
A recently patched vulnerability in the popular Apache Camel Java library is under scrutiny by security researchers, with the Akamai Security Intelligence Group providing an in-depth analysis of the flaw, tracked as CVE-2025-27636. While initial reports may have downplayed the severity, Akamai’s analysis highlights the potential for “devastating results, including remote code execution“.
Apache Camel is a widely used open-source integration framework that enables seamless data exchange among different systems, applications, and cloud services. Its ubiquity makes this vulnerability a serious concern for organizations relying on Camel for critical business workflows, API integrations, and microservices orchestration.
The vulnerability lies in Camel’s “incorrect filtering of request headers“. The Apache Camel uses DefaultHeaderFilterStrategy.java to block internal headers from being forwarded externally, a crucial security measure to prevent the leakage of sensitive routing information.
Before the fix, “Apache Camel used a case-sensitive filtering rule“. This meant that headers were only filtered if they matched the exact case of the internal header names. As the Akamai analysis points out, “If an attacker changed the case and used CAmelHttpUri or CAMELHttpResponseCode, for example, the header would not be filtered“.
The case-sensitive flaw allows attackers to inject arbitrary headers into requests, which Camel would then forward to internal components. While Apache notes that the vulnerability doesn’t grant access to all internal methods, attackers can access those “that are in the same bean declared in the bean URI“.
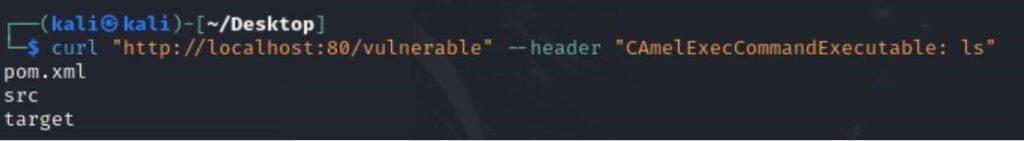
Akamai’s research emphasizes the ease of exploitation: “The vulnerability is trivial to exploit“. To demonstrate this, they created a sample vulnerable application that could be exploited remotely. The application, designed to execute the “whoami” command, could be manipulated to execute arbitrary commands by injecting headers with a different case. A proof-of-concept exploit code for this flaw is available on Github.
Apache has addressed the vulnerability by “forcing letter case uniformity“. The fix involves converting all header names to lowercase before filtering, effectively preventing attackers from bypassing the filter by manipulating the case.
However, identifying vulnerable applications remains a challenge. “Security teams must assess a wide range of assets as Apache Camel is integrated in numerous places,” including applications where the library is an indirect dependency.
To aid in detection, Akamai has developed PowerShell and Bash scripts that recursively scan directories, detect Apache Camel JAR files, and output potentially vulnerable applications.
Akamai strongly recommends that organizations using Apache Camel:
-
Apply the patch immediately: Upgrade to versions 4.10.2, 4.8.5, and 3.22.4, where the vulnerability is fixed.
-
Identify vulnerable applications: Utilize the provided scripts or other methods to scan for and identify vulnerable instances of Apache Camel.
-
Prioritize patching: Given the ease of exploitation and potential impact, prioritize patching vulnerable systems to mitigate the risk of remote code execution.