In light of a severe vulnerability discovered in Apache Struts, Cisco Systems has elucidated the impact on its products. The culprit, a path traversal vulnerability identified as CVE-2023-50164, has sent ripples through the cyber world, raising alarms across sectors.
This flaw is a path traversal vulnerability in Apache Struts. By exploiting this, attackers can manipulate file upload parameters to achieve path traversal, thereby uploading malicious files to execute remote code (RCE).

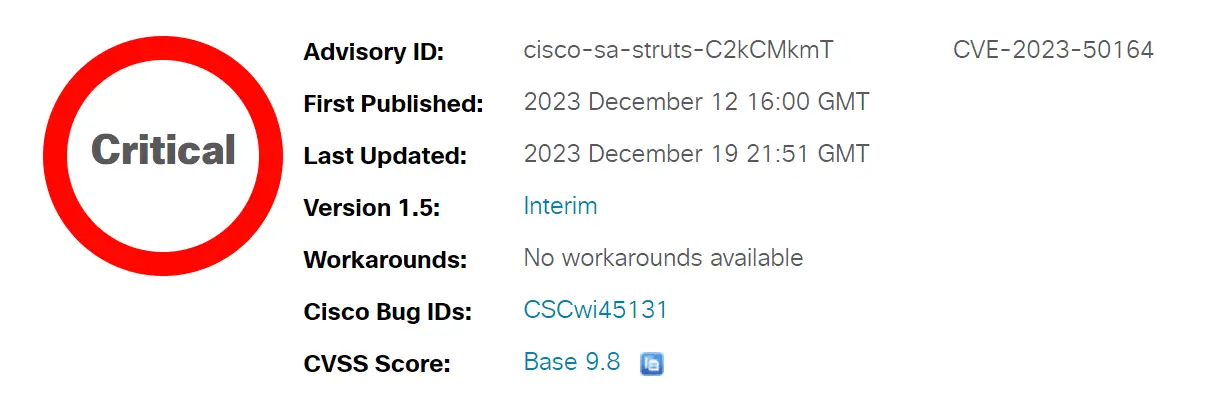
Cisco’s thorough investigation has shed light on the repercussions of the CVE-2023-50164 vulnerability within its products, particularly the Cisco Identity Services Engine (ISE) 3.0. The company’s advisory, classifying the severity as “Critical” and assigning a CVSSv3.1 base score of 9.8, underscores the gravity of the situation. However, Cisco confirmed that versions released after ISE 3.1 in April are not impacted.
As of December 19th, the vulnerability is confined to this product alone, with no other products currently under investigation. Cisco has also provided a list of 26 products confirmed to be unaffected by this vulnerability through their security advisory.
The Imperva Threat Research team has observed thousands of exploitation attempts since the publication of several proofs of concept (POCs) on December 11, 2023. Notably, these attacks, primarily executed by automated hacking tools written in Go, have targeted web applications predominantly in the United States, Australia, the Netherlands, and New Zealand.
During these attempts, attackers cunningly craft special requests to upload malicious web shells, commonly as .JSP or .WAR files, into restricted areas using path traversal techniques. This tactic echoes the notorious Equifax breach of 2017, reminding us of the allure that vulnerabilities in Struts hold for threat actors.
Given its extensive distribution, any weakness in Apache Struts, like CVE-2023-50164, becomes a concern of monumental proportions. The potential for widespread exploitation underscores the need for heightened vigilance and rapid response measures across various sectors.
For organizations using Apache Struts, especially those utilizing vulnerable versions of Cisco ISE, immediate action is imperative. Upgrading systems, applying patches, and continuous monitoring are essential steps in fortifying defenses against such potent cyber threats.