APKiD v2.1.5 releases: Android Application Identifier for Packers, Protectors, Obfuscators and Oddities
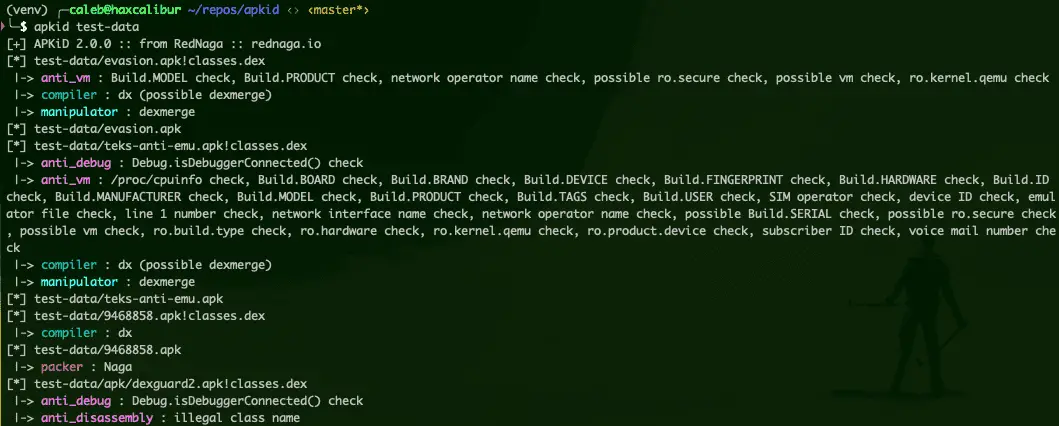
APKiD gives you information about how an APK was made. It identifies many compilers, packers, obfuscators, and other weird stuff. It’s PEiD for Android.
For more information on what this tool can be used for, check out:
Changelog v2.1.5
- Packers:
- AppSealing
- BlackMod (modder)
- 5Play.ru (modder)
- Aegis – AndroidRepublic (modder)
- KangaPack
- LIAPP
- Protectors:
- DexGuard v9.x (Aarch64)
- DexProtector telemetry (Alice)
- Verimatrix / InsideSecure
- Protectt.ai
- Google Play Integrity protection
- Secucen AppIron
- Ahope AppShield
- AppCamo
- EverSafe
- VGuard
- DxShield
- Obfuscators:
- LSPosed (seen in Momo, Shamiko and so on)
- Android Republic VIP (modder)
Installing
pip install apkid
Docker install
In an attempt to reduce the support ticket we receive from the above instructions being hard to follow, there is a docker file and script which can be used for processing files quickly. This also serves as proof that the above instructions do work! This usage, of course, requires that you have docker correctly installed on your machine. However, the following instructions should “just work” if you have docker and git install on a machine:
git clone https://github.com/rednaga/APKiD
cd APKiD/
docker build . -t rednaga:apkid
docker/apkid.sh ~/reverse/targets/android/example/example.apk
[+] APKiD 2.1.0 :: from RedNaga :: rednaga.io
[*] example.apk!classes.dex
|-> compiler : dx
Usage
usage: apkid [-h] [-j] [-t TIMEOUT] [-o DIR] [FILE [FILE …]]
APKiD – Android Application Identifier v1.0.0
positional arguments:
FILE apk, dex, or directoryoptional arguments:
-h, –help show this help message and exit
-j, –json output results in JSON format
-t TIMEOUT, –timeout TIMEOUT
Yara scan timeout (in seconds)
-o DIR, –output-dir DIR
write individual JSON results to this directory

Submitting New Packers / Compilers / Obfuscators
If you come across an APK or DEX which APKiD does not recognize, please open a GitHub issue and tell us:
- what you think it is
- the file hash (either MD5, SHA1, SHA256)
We are open to any type of concept you might have for “something interesting” to detect, so do not limit yourself solely to packers, compilers or obfuscators. If there is an interesting anti disassembler, anti vm, anti* trick, please make an issue.
You’re also welcome to submit pull requests. Just be sure to include a file hash so we can check the rule.
Hacking
First, you will need to install the specific version of yara-python the project depends on (more information about this in the Installing section):
git clone –recursive https://github.com/rednaga/yara-python
cd yara-python
python setup.py install
Then, clone this repo, compile the rules, and install the package in editable mode:
git clone https://github.com/rednaga/APKiD
cd APKiD
./prep-release.py
pip install -e .[dev]
If the above doesn’t work, due to permission errors dependent on your local machine and where Python has been installed, try specifying the –user flag. This is likely needed if you are working on OSX:
pip install –e .[dev] –user
Copyright (C) 2019 RedNaga. https://rednaga.io
Source: https://github.com/rednaga/





