Apollo v2.3.13 releases: Windows agent written in C#
Apollo
Apollo is a Windows agent written in C# using the 4.0 .NET Framework designed to be used in SpecterOps training offerings. Apollo lacks some evasive tradecraft provided by other commercial and open-source tools, such as more evasive network communications, PE manipulation, AMSI evasion, and otherwise; however, this project (in tandem with Mythic) is designed to introduce several quality of life improvements for an operator.
Notable Features
- Lateral Movement
- UAC Bypass
- Credential Tracking and Manipulation
- .NET Assembly and PowerShell Script Execution
- User Exploitation Suite
- SOCKSv5 Support
Supported C2 Profiles
Currently, only two C2 profiles are available to use when creating a new Apollo agent: HTTP and SMB.
HTTP Profile
The HTTP profile calls back to the Mythic server over the basic, non-dynamic profile. When selecting options to be stamped into Apollo at compile time, all options are respected with the exception of those parameters relating to GET requests.
SMB (Currently Defunct)
The SMB profile only takes a pipe name on the compilation. This pipe name can be randomly generated when creating the agent and can be generated based on a provided regex (e.g.[0-9a-z]{4}\-[0-9a-z]{8}\-[0-9a-z]{8}\-[0-9a-z]{4}). Currently, there’s an open issue with SMB messages, so SMB linking is non-functional.
SOCKSv5 Support
SOCKS support is built-in to the agent and dispatched through the SocksManager file. To start the socks server, issue socks start [port], and to stop it issue socks stop. You can view active SOCKS proxies by clicking on the dropdown of a callback and clicking “Socks Proxies.”
Quality of Life Improvements
File Triage
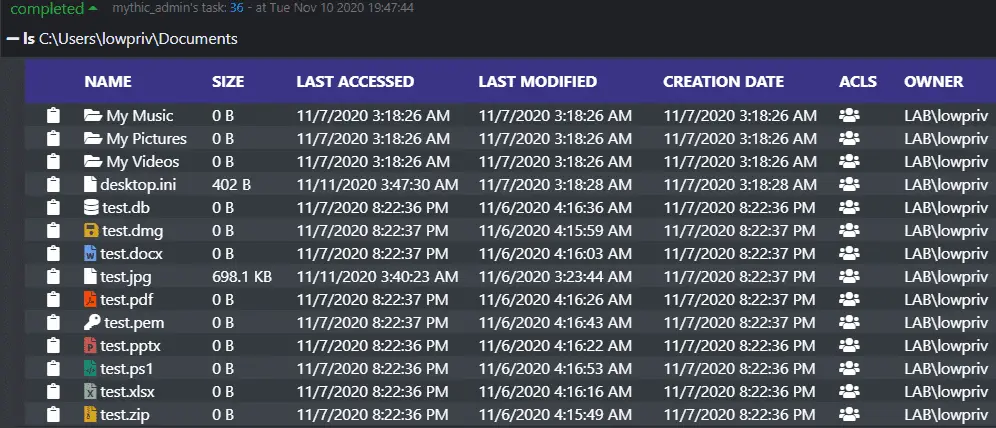
The ls command reports back a wealth of information and allows operators to easily copy file paths and examine permissions of files, in addition to being able to sort and filter files. Clicking the icon under the ACLs column will show all the permissions of a file. Additionally, this hooks into Mythic’s native file browser.
Clicking the ACL icon shows permissions: 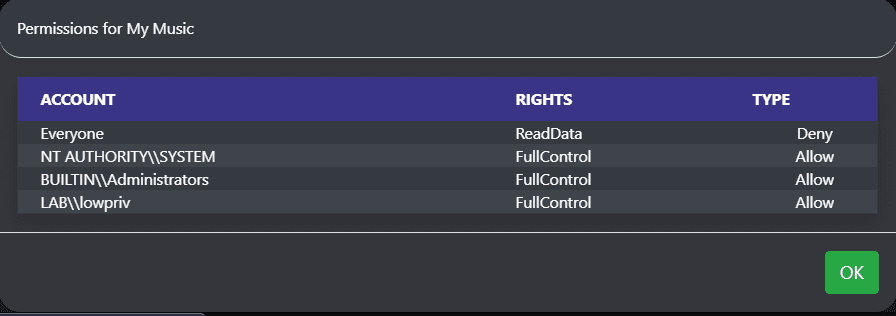
Interfaces with Mythic’s filebrowser and caches data server-side: 
Process Listings
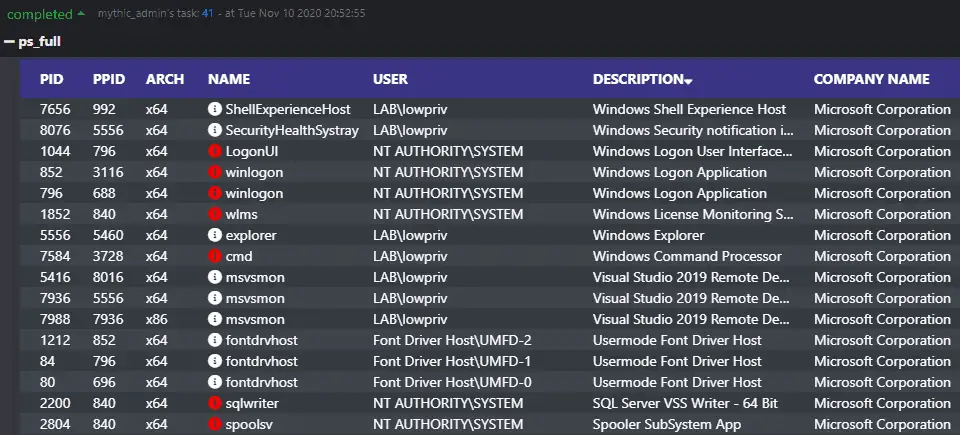
When issuing ps_full, additional details are retrieved such as:
- Company name of the process executable
- Description of the process executable
- The full path of the process
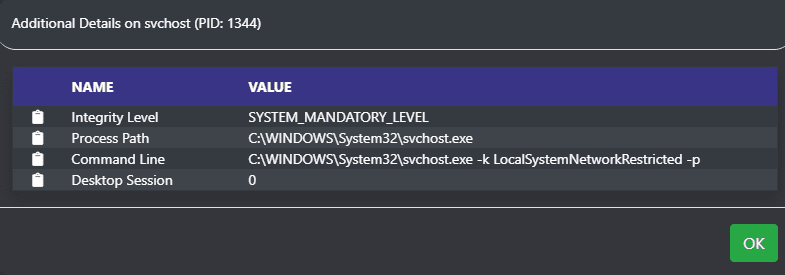
- Integrity level of the process
- Desktop session
- Process command-line arguments
This process listing also interfaces with Mythic’s built-in process browser, which allows you to see process trees more easily.
Clicking the informational icon next to the name displays a popup window with more information.
Assembly and PowerShell Script Caching
Apollo can cache one or more .NET assemblies as well as one or more PowerShell Scripts with no size limitation on imported files.
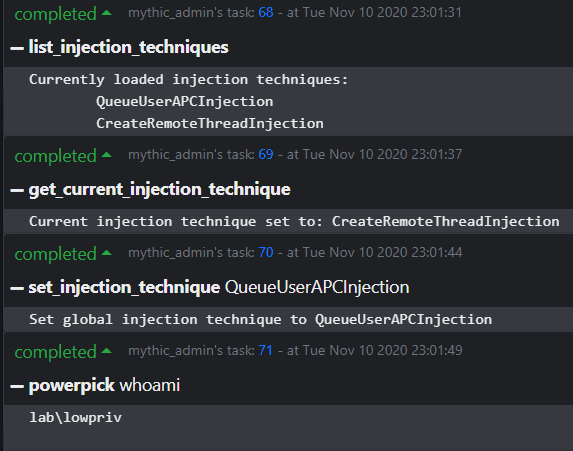
Dynamic Injection Techniques
The agent can change what code injection technique is in use by post-exploitation jobs that require injection through a suite of injection commands. Currently, injection techniques that are supported:
- CreateRemoteThread
- QueueUserAPC (Early Bird)
Token Manipulation Tracking
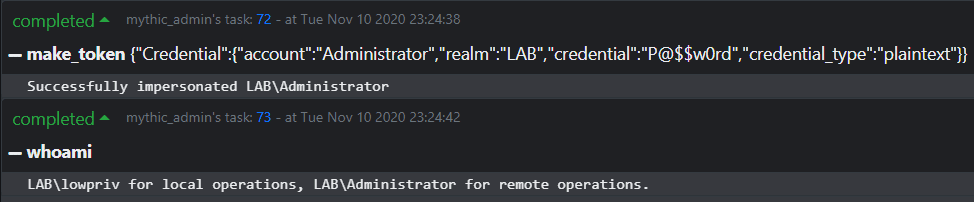
Apollo attempts to track the current access token in use by the agent through its own whoami command, which will track the impersonated user for local and remote operations.
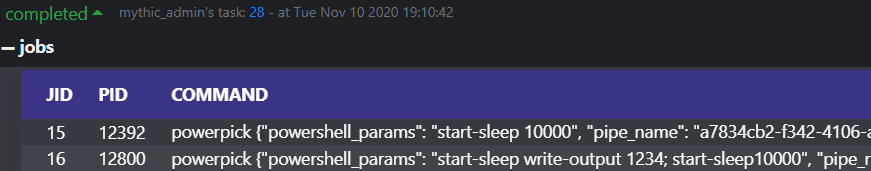
Job Tracking
Agent jobs are tracked by job ID, by command, and by the arguments passed to the command so that you know what job correlates to what tasking.
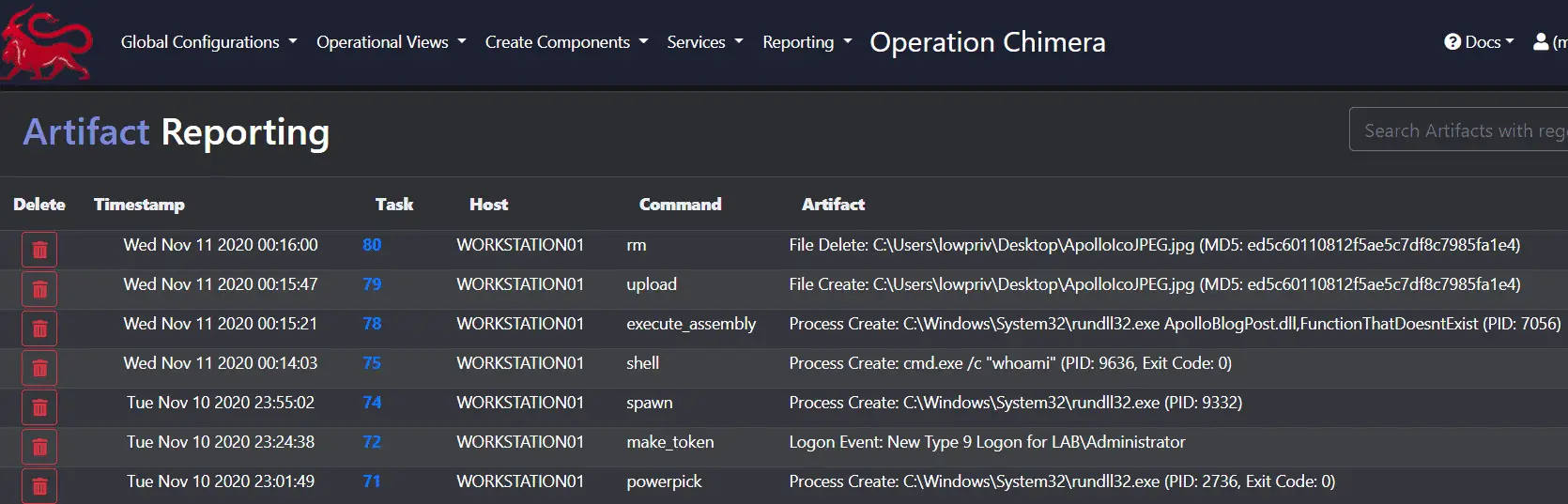
Artifact Tracking
Commands that manipulate the disk, create new logons, or spawn new processes will document those changes in the Artifact Reporting page as shown below.
Changelog v2.3.13
- Last version that supports Mythic 2.3.13. Future versions target Mythic 3.0+
Install
Copyright (c) 2018, Dwight Hohnstein
All rights reserved.