Rogue Assembly Hunter: discovering ‘interesting’ .NET CLR modules in running processes
Rogue Assembly Hunter
Rogue Assembly Hunter is a utility for discovering ‘interesting’ .NET CLR modules in running processes.

Background
.NET is a very powerful and capable development platform and runtime framework for building and running .NET managed applications. Over the last several years, .NET has been adopted by Red Teams (and likes thereof) for instrumenting tradecraft to support offensive operations. In particular, the shift from offensive PowerShell to .NET was a logical leap (for many) due to the increased optics and opportunistic visibility present in PowerShell v5+. As such, .NET offensive tooling and tradecraft have been successfully used to evade host-based defensive capabilities, bypass application control, and build/stage/deliver/execute malicious code (similar to PowerShell).
From a prevention perspective, Microsoft is doing more to combat .NET instrumented threats and to minimize the overall .NET attack surface. For example, Microsoft has added AMSI inspection capabilities in .NET Framework 4.8, and WDAC/WLDP mechanisms are quite effective. From a detection/response perspective, further visibility and introspection into the .NET ecosystem is always advantageous for discovering new ways to combat .NET-focused threats.
In 2017, Joe Desimone (@dez_) wrote a fantastic article called Hunting For In-Memory .NET Attacks. Still relevant today, the article outlines modern .NET attack vectors as well as on-demand and event-based techniques for detection. Accompanying the article, Joe released a tool (Get-ClrReflection) to proactively detect (and retrieve) in-memory .NET CLR modules that lack a proper disk reference. Inspired by Joe’s work and taking advantage of the introspection capabilities of the CLRMD runtime diagnostics library (+ subsequent data access capabilities of mscordacwks.dll), Rogue Assembly Hunter was created to:
- Inspect (all) running .NET (‘managed’) processes for interesting CLR modules (e.g. module(s) that form an ‘assembly’)
- Inspect a single .NET (‘managed’) process (by PID) for interesting CLR modules
- Watch for newly spawned processes and attempt to inspect for interesting CLR modules
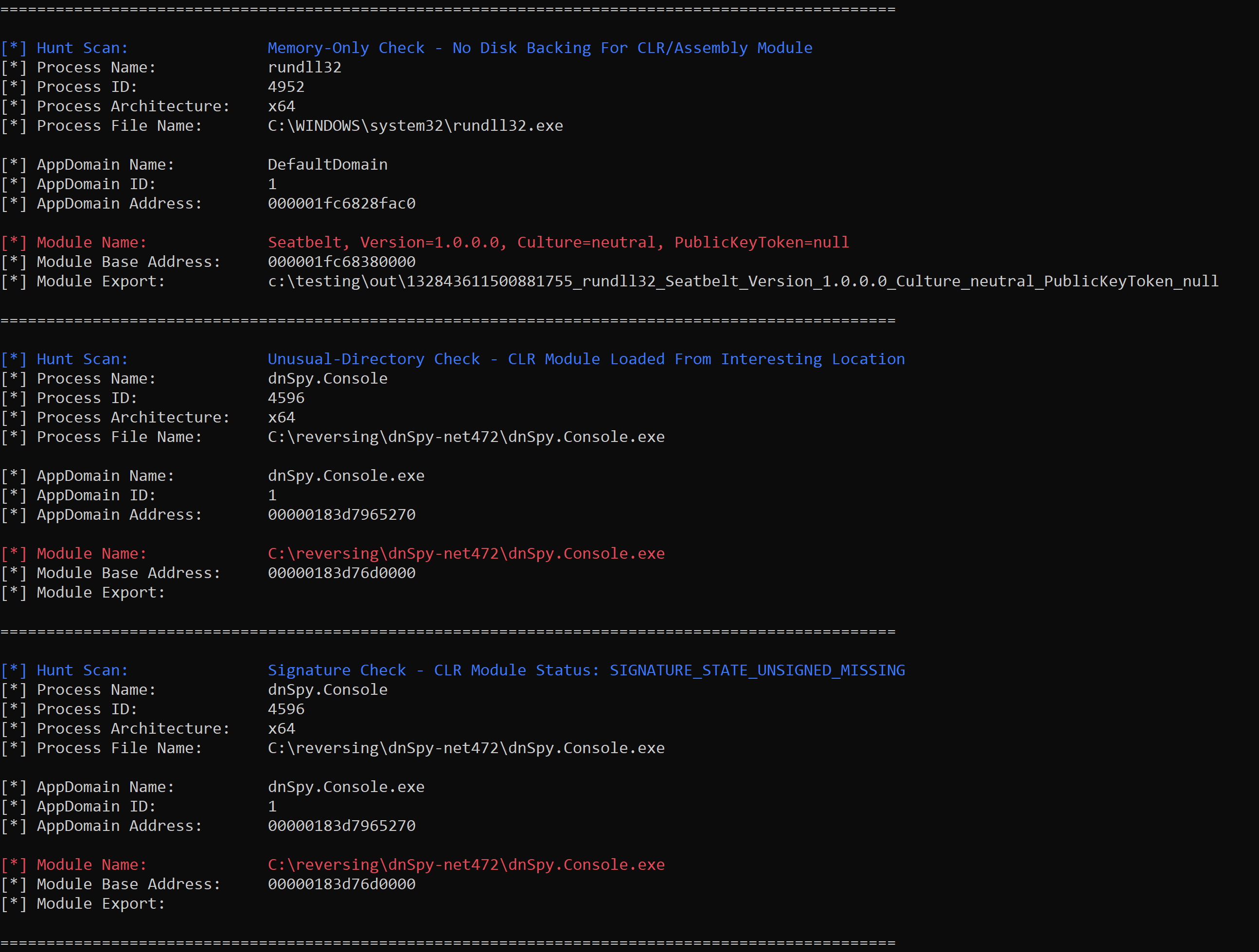
- Support several ‘hunt’ capabilities to discover in-memory loaded modules, the signature status of modules (if loaded from disk), modules loaded from interesting directories, and imposter modules (e.g. fake file references).
- Support CLR module export functionality (a quick port from Get-ClrReflection)
- Inspire more interesting tooling and tradecraft
Notes, Tips, & Caveats
- Run as a privileged user with high/system integrity.
- ‘Hunts’ are experimental and not guaranteed to provide complete/correct results. Beware of false positives (e.g. signed modules) and validate accordingly.
- RogueAssemblyHunter uses the CLRMD to connect to live processes, which could introduce interesting results.
- Due to the scanning nature of RogueAssemblyHunter, there is a possibility of race conditions and missed results. Consider tuning with the –checks and –sleep switches to help (especially in ‘watch’ mode). In some cases, it may be difficult to ‘catch’ a particular assembly load due to speed of execution (such as execute-assembly and sacrificial processes).
- Architecture (‘bitness’) and .NET versions matter (e.g. 4+) for interacting with remote processes with the .NET CLRMD libraries.
- For maximum inspection/coverage, build and run this program for x86 and x64 use cases.
- Process sweep mode will attempt to connect to all running processes regardless of ‘bitness’. It will otherwise fail accordingly for architecture mismatches.
- Tested on Windows 10 Pro 2H1H and Windows Server 2016 Standard 1607. It may run on other versions with the relevant .NET Framework.
- Visual Studio project source with NuGet packages, PowerShell script, and release binaries are included with this project.
- Notice.md includes project disclaimers and license information.
- Run at your own risk (and don’t mind my horrible code 😉 )!
Download & Use
Copyright (c) 2021 bohops