Source: Forcepoint X-Labs
Forcepoint X-Labs exposes a new campaign utilizing Python, TryCloudflare, and Dropbox to spread the notorious AsyncRAT.
The Forcepoint X-Labs research team has discovered a renewed AsyncRAT malware campaign exploiting legitimate online services to deliver its malicious payload. This campaign, which shares similarities with a previous attack identified in August, highlights the ongoing trend of cybercriminals leveraging trusted infrastructure to evade detection and trick unsuspecting users.
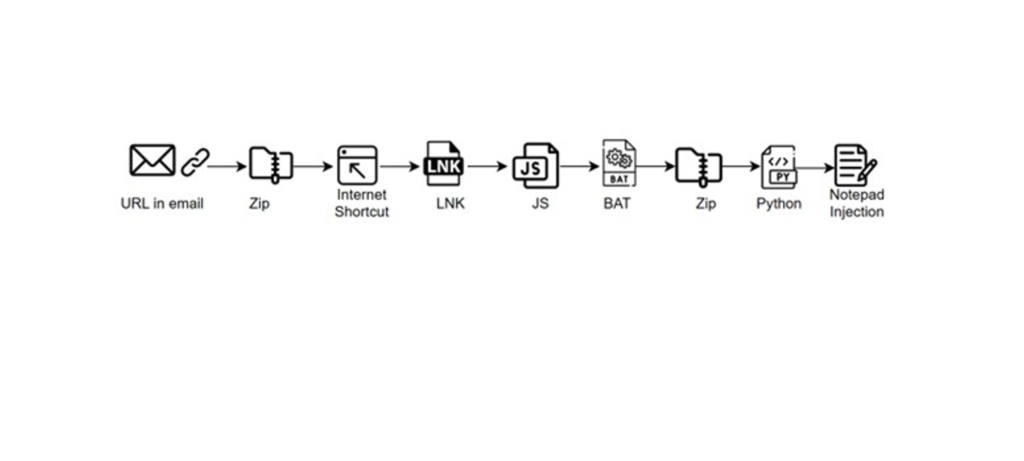
The attack begins with a phishing email containing a Dropbox URL. Clicking the link downloads a ZIP file containing an internet shortcut file, which, when opened, sets off a chain reaction. This chain involves downloading and executing several files in the background, including a JavaScript file, a BAT file, and finally, a Python script that deploys AsyncRAT.
“This AsyncRAT campaign has again showed how hackers can use legitimate infrastructures like Dropbox URLs and TryCloudflare to their advantage,” the report states.
The attackers cleverly disguise their malicious activity by simultaneously opening a legitimate-looking PDF file, leading users to believe they have simply downloaded an invoice. Meanwhile, the malware establishes a foothold on their system.
The use of TryCloudflare, a service that provides quick and easy tunnels to web applications, is a particularly noteworthy aspect of this campaign. By hosting their malicious files on a TryCloudflare subdomain, the attackers add a layer of legitimacy to their operation, making it more difficult for security solutions to flag the activity as suspicious.
The final payload delivery relies on Python scripts, designed to execute shellcode and inject malicious processes into legitimate applications. The attackers use DLL injection, process hollowing, and APC queue techniques to stealthily launch their malware.
“The load.py file is base 64 encoded but after deobfuscating we get the full code. The python file’s main objective is to go through each of the bin file which stores Shell code, and each consist of different malware types,” Forcepoint explains.
Key techniques include:
- Process Injection via Early Bird APC Queue → Executing shellcode before security tools detect it.
- Shellcode Deployment in Legitimate Processes → Infecting notepad.exe and explorer.exe.
- Memory Allocation & Thread Execution → Using VirtualAlloc(), CreateThread(), and RtlMoveMemory() for stealthy execution.
Notably, different payloads are injected into different system processes, with payload.bin delivering VenomRAT, while xr.bin executes XWorm, and other .bin files drop AsyncRAT.
“Payload.bin file injects VenomRAT shellcode into legitimate notepad.exe process and xr.bin injects XWorm shellcode, but all others inject AsyncRAT shell code into legitimate process explorer.exe,” the report states.
Once deployed, AsyncRAT connects to C2 servers using dynamic ports. The malware can:
- Drop additional payloads (DLLs, executables, or scripts).
- Execute arbitrary code remotely.
- Modify system registry settings for persistence.
- Exfiltrate sensitive user data.
Forcepoint X-Labs warns that this campaign is likely a harbinger of a broader trend. As attackers continue to seek new ways to bypass security measures, the abuse of legitimate infrastructure is expected to rise.
Related Posts:
- Beware of Fake Downloads: AsyncRAT Spreads via Popular Software Cracks
- AsyncRAT Malware Campaign Exploits Bitbucket to Deliver Multi-Stage Attack
- Evasive Phishing Campaign Delivers AsyncRAT and Infostealer
- Cybercriminals Exploit Ebooks to Spread AsyncRAT Malware
- Beware! AsyncRAT Shapeshifts to Evade Defenses