Attach chain | Image: Trend Micro
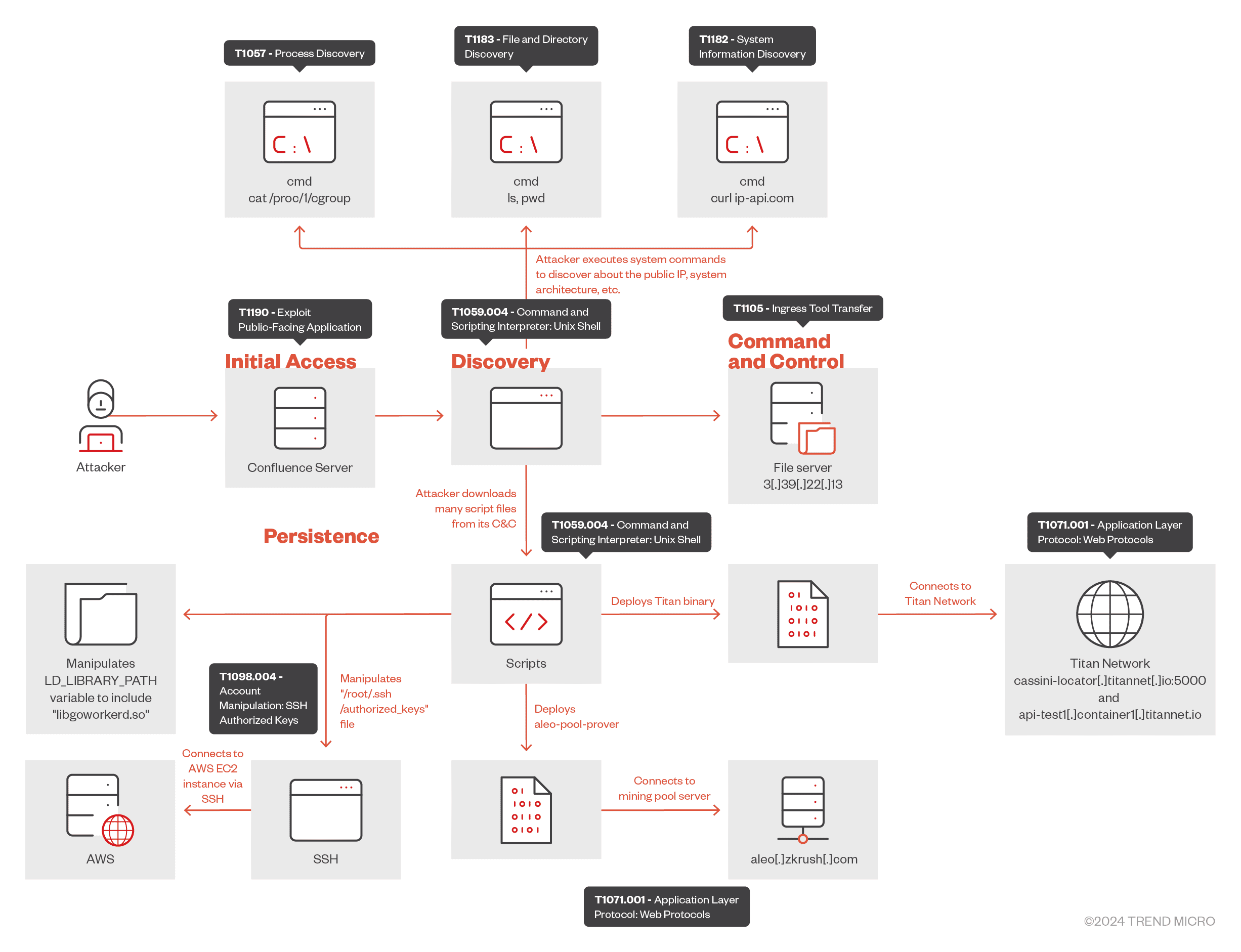
In a recently disclosed report by Trend Micro, attackers were observed exploiting a vulnerability in Atlassian’s Confluence servers (CVE-2023-22527) to hijack victim resources and harvest rewards from the Titan Network—a decentralized, open-source platform that transforms hardware into valuable digital assets.
The attack sequence begins with exploiting an unauthenticated template injection vulnerability in Confluence servers, allowing attackers to execute remote commands on compromised systems. “This allowed unauthenticated attackers to achieve remote code execution (RCE) and leverage the Titan Network for cryptomining activity,” explained Trend Micro researchers.
Once gaining initial access, attackers deploy a series of shell scripts to the victim’s machine, meticulously executing commands to assess the server’s environment. These commands include identifying IP addresses and operating system details. By remotely running commands like ls and cat /etc/os-release, attackers enumerate critical system information, further setting the stage for payload deployment.
The Titan Network, based on a decentralized physical infrastructure network (DePIN), enables users to share computing power, storage, and bandwidth for economic rewards. With this model, compromised machines, dubbed “Titan edge nodes,” can earn rewards on behalf of attackers. By deploying Titan’s software on victims’ systems, attackers successfully integrate these machines into the Titan ecosystem, profiting from their compute power.
According to Trend Micro, “its economic incentives and network design ensure that contributors are rewarded for their resources, while end-users enjoy high-quality, reliable results comparable to modern cloud services”.
The deployment involves multiple shell scripts strategically placed in the /tmp directory. Each script performs a specific task, from uploading the Titan binaries (titan.tar.gz) to modifying environment variables and executing the Titan edge process. An oversight in the script, noted as “LD_LIZBRARY_PATH” instead of “LD_LIBRARY_PATH,” hints at possible obfuscation to evade detection mechanisms.
In one instance, attackers used commands to establish communication with the “Cassini Testnet” in the Titan Network, which, as Trend Micro highlights, consists of a “Delegated Proof of Stake (DPOS) consensus mechanism, where users earn rewards by staking TTNT test tokens”. The entire process is automated to ensure continued exploitation, while attackers remotely control these scripts, modifying system configurations and resources for optimized cryptomining.
Trend Micro’s report underscores the importance of “maintaining up-to-date security patches, rigorous network and file monitoring, and robust access controls” as key defenses against such sophisticated intrusions. The Titan Network exploitation adds a novel dimension to cryptojacking, where decentralized infrastructure networks like Titan serve as lucrative targets.
Related Posts:
- Cryptojacking Campaign Exploits Atlassian Confluence CVE-2023-22527 Vulnerability
- Researchers Published Technical Details for Atlassian Confluence RCE (CVE-2023-22527)
- CVE-2023-22527 (CVSS 10): Critical RCE Flaw in Confluence Data Center and Server