Atomic Threat Coverage: combat threats based on MITRE’s ATT&CK
Atomic Threat Coverage
Actionable analytics designed to combat threats based on MITRE’s ATT&CK.
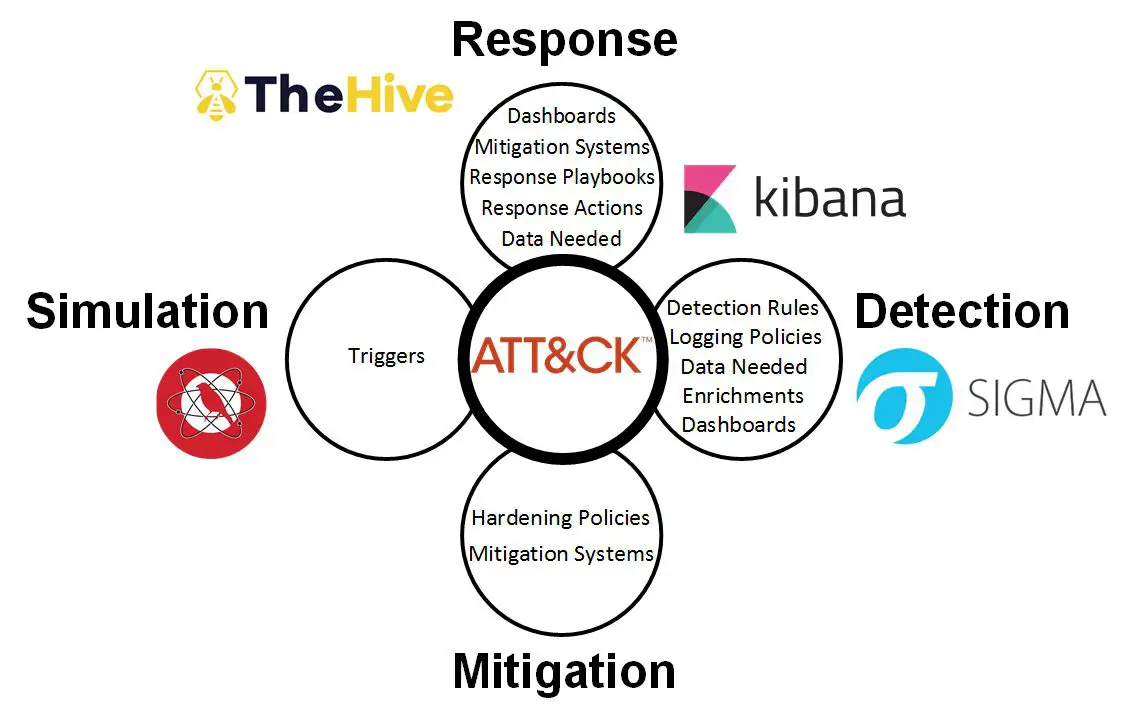
Atomic Threat Coverage is a tool which allows you to automatically generate actionable analytics, designed to combat threats (based on the MITRE ATT&CK adversary model) from Detection, Response, Mitigation, and Simulation perspectives:
- Detection Rules based on Sigma — Generic Signature Format for SIEM Systems
- Data Needed to be collected to produce detection of specific Threat
- Logging Policies need to be configured on the data source to be able to collect Data Needed
- Enrichments for specific Data Needed which required for some Detection Rules
- Triggers based on Atomic Red Team — detection tests based on MITRE’s ATT&CK
- Response Playbooks based on atc-react — Security Incident Response Playbooks for reacting on specific Threat
- Mitigation Policies based on atc-mitigation need to be deployed and/or configured to mitigate specific Threat
- Visualisations for creating Threat Hunting / Triage Dashboards
- Customers of the analytics — could be internal or external. This entity needed to tracking the implementation
Atomic Threat Coverage is a highly automatable framework for accumulation, development, and sharing actionable analytics.
How it works
Everything starts from the Sigma rule and ends up with human-readable wiki-style pages and other valuable analytics. Atomic Threat Coverage parses it and:
- Maps Detection Rule to ATT&CK Tactic and Technique using
tagsfrom Sigma rule - Maps Detection Rule to Data Needed using
logsourceanddetectionsections from Sigma rule - Maps Detection Rule to Triggers (Atomic Red Team tests) using
tagsfrom Sigma rule - Maps Detection Rule to Enrichments using references inside Detection Rule
- Maps Response Playbooks to ATT&CK Tactic and Technique using references inside Response Playbooks
- Maps Response Actions to Response Playbooks using references inside Response Playbooks
- Maps Logging Policies to Data Needed using references inside Data Needed
- Maps Detection Rules, Data Needed and Logging Policies into Customers using references inside Customers entity
- Converts everything into Confluence and Markdown wiki-style pages using jinja templates (
scripts/templates) - Pushes all pages to a local repo and Confluence server (according to the configuration provided in
config.yml) - Creates Elasticsearch index for visualisation and analysis of existing data in Kibana
- Creates ATT&CK Navigator profile for visualisation of current detection abilities per Customer
- Creates TheHive Case Templates, build on top of Response Playbooks
- Creates
analytics.csvandpivoting.csvfiles for simple analysis of existing data - Creates Dashboards json files for uploading to Kibana
Download & Use
Copyright (C) 2021 atc-project





