Researchers at security company Imperva said last week that they have detected a new attack technology for PostgreSQL servers. When an attacker logs in to the database, a number of different payloads are created first, and these payloads are embedded in the picture to evade security detection. These payloads will eventually be extracted to the target server’s local hard drive for remote code execution.
The researchers stated that they are the same as the recent attacks they detected. The ultimate goal of the attacker is to deploy an encrypted currency mining program on the target server to use the server’s computing resources to mine the Monroe coins. What is interesting, however, is that the attackers used pictures of American actress Scarlett Johannsson as an attack vector.
PostgreSQL is a commonly used open source database. Like other common databases, it also provides a Metasploit module to simplify the interaction with the operating system. The researchers stated that in this attack, the attacker used a modified Metasploit module to initiate interaction with PostgreSQL to execute shell commands on the server.
The modification in the module is to evade the security detection of the database monitoring and auditing system (DAM). This system is designed to monitor privileged operations such as the lo_export function call. In this attack, the attacker is using the lo_export function to dump the malware’s payload to the target server’s local hard disk.
Once an attacker gains the ability to execute system commands, it can obtain the details of the server’s GPU by executing the lshw -c video command and get the server’s CPU details by running cat /proc/cpuinfo. With this information in hand, what remains is the execution of the Monroe mining plan.
According to the information displayed by the attacker’s wallet address, so far they have collected 312 Monroe coins worth about $90,000. At the same time, it also means that more than one PostgreSQL server has become a victim.
Seeing everyone here may not have much interest, then let’s go back to the beauty of Scarlett Johansson. In this attack, the attacker embeds the payload in the picture and uploads it to the imagehousing[.]com site (a legitimate site for people to host and share pictures for free). Malicious code is located below Scarlett Johansson’s left elbow. Nothing unusual is found at all from the image itself. Of course, the picture shown in this article is definitely a “safe and non-toxic”beautiful photo.

Why do attackers choose to use celebrity photos to embed malware? Imperva researchers believe that the main purpose of doing so is to make it easier to cheat security products. Because attaching binary code to a real image file or document not only changes the file itself but also bypasses most anti-virus software.
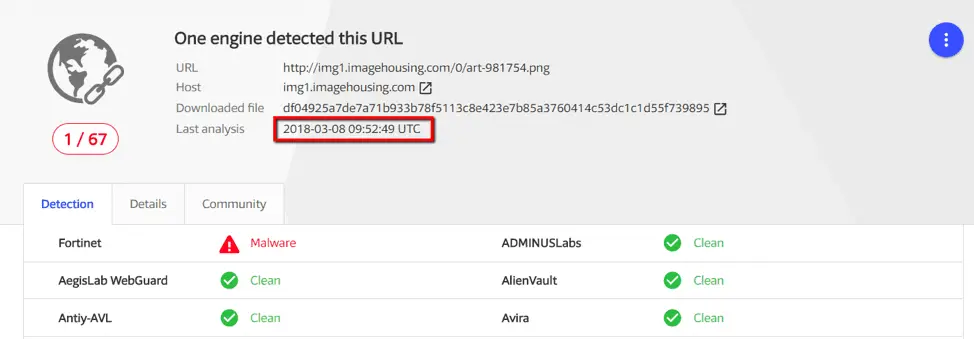
In order to prove his claim, Imperva researchers conducted a security check on the three different forms of the mining code (image link, the image itself and mining code) through the Google VirusTotal engine. The results are as follows:
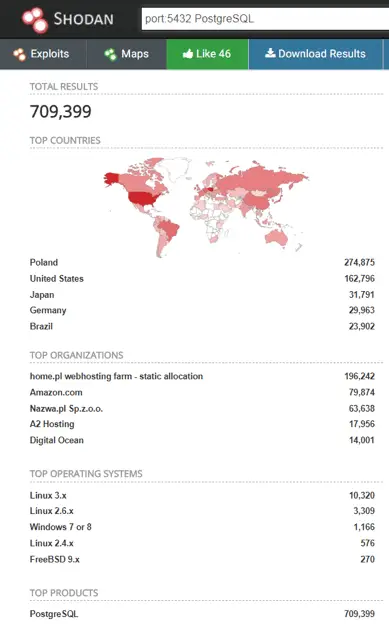
In addition, in order to prove the seriousness of the situation, the researchers also decided to let the search results of the Shodan engine tell us exactly how many PostgreSQL servers are easily targeted by the attacker. Search results show that at least 710,000 PostgreSQL servers that meet the attack requirements are exposed online, mostly in Poland and the United States.

Imperva stated that PostgreSQL server users can avoid becoming victims by:
- Watch out of direct calls to lo_export or indirect calls through entries in pg_proc
- Beware of functions calling to C-language binaries
- Use a firewall to block outgoing network traffic from your database to the internet
- Make sure your database is not assigned with public IP address. If it is, restrict access only to the hosts that interact with it (application server or clients owned by DBAs)
Source, Image: Imperva