autoenum v3 releases: Automatic Service Enumeration Script
autoenum
Autoenum is a recon tool which performs automatic enumeration of services discovered. I built this to save some time during CTFs and pen testing environments (i.e. HTB, VulnHub, OSCP) and draws a bit from a number of existing tools including AutoRecon, Auto-Recon, and nmapautomator. Could also be used in a real-life pentesting engagement. Currently has only been tested in kali. If you notice a bug or have a feature request, not in a to-do, please submit an issue or let know some other way(discord preferred). 
How it Works
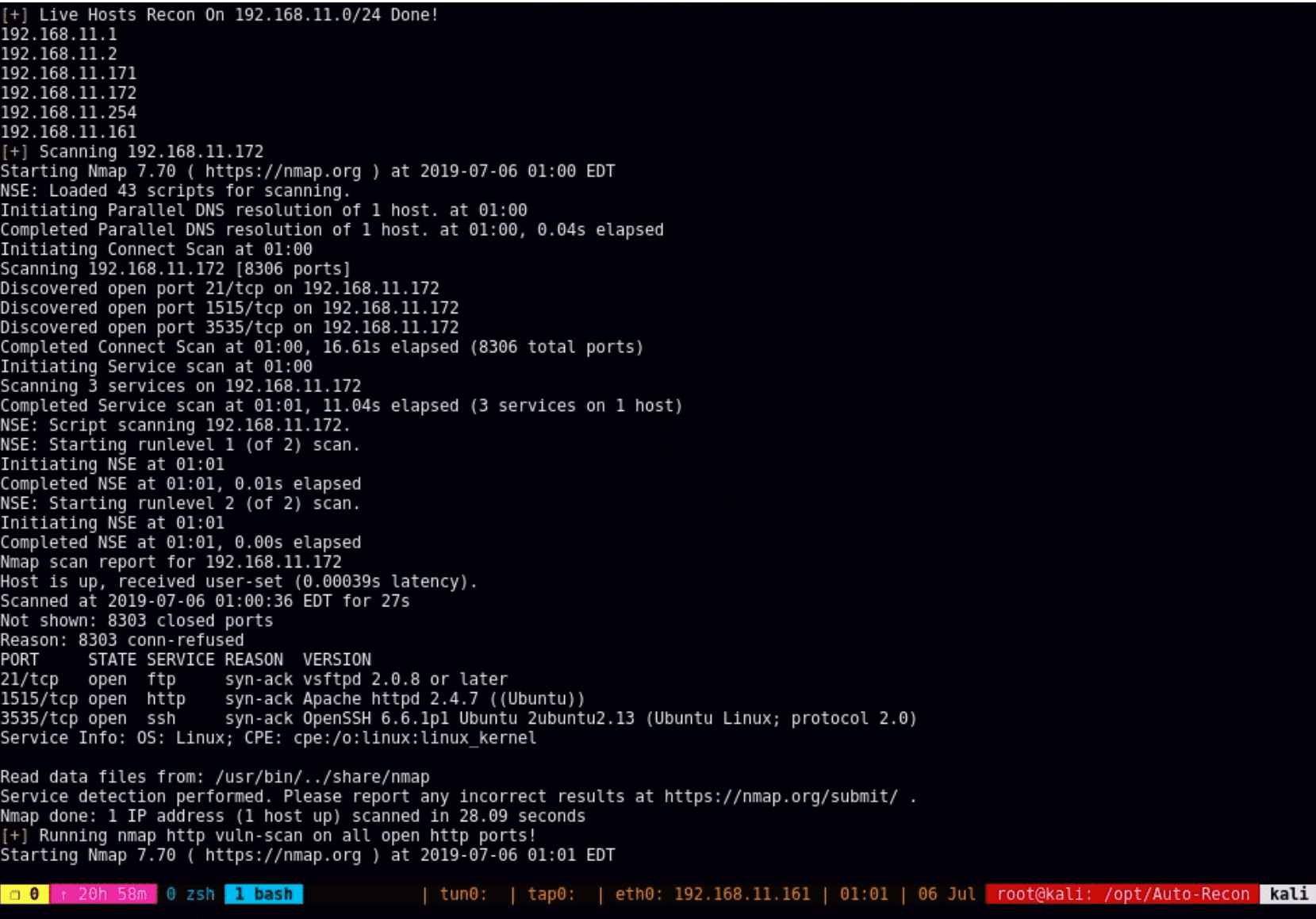
Autoenum first runs 2 nmap scans in tandem, one scan looks specifically for service versions to run against searchsploit and the other is a scan dependent on the argument. Every scan profile checks for services running, the type of scan is the only difference. After the scans are finished, the services/ports open and operating systems along with script output (if available) is extracted and further analyzed. If a certain service is found, Autoenum will begin enumerating by firing off a number of tools and create a dir for that service (i.e detecting http starts up nikto, wafw00f, gobuster, and others). If a dependency required is not detected, that dependency will be auto-installed and checked if there is a new update every time the tool is run. Autoenum outputs this information in 2 main sections(scan type and loot dirs) with sub-directories branching off depending on what is found.
Changelog v3
- Polished UI, now works with urls, cleaned up some more bugs, added some more enum and scans
Install
git clone https://github.com/thatonetester/autoenum.git cp ~/autoenum/autoenum.sh /usr/bin/autoenum chmod o+x /usr/bin/autoenum
Use
autoenum
Source: https://github.com/Gr1mmie/