autoRecon: automation Information Gathering tool
autoRecon
autoRecon is an automation tool which works on Phases which automates the manual process and give results in HTML file.
Features
–On the Main domain
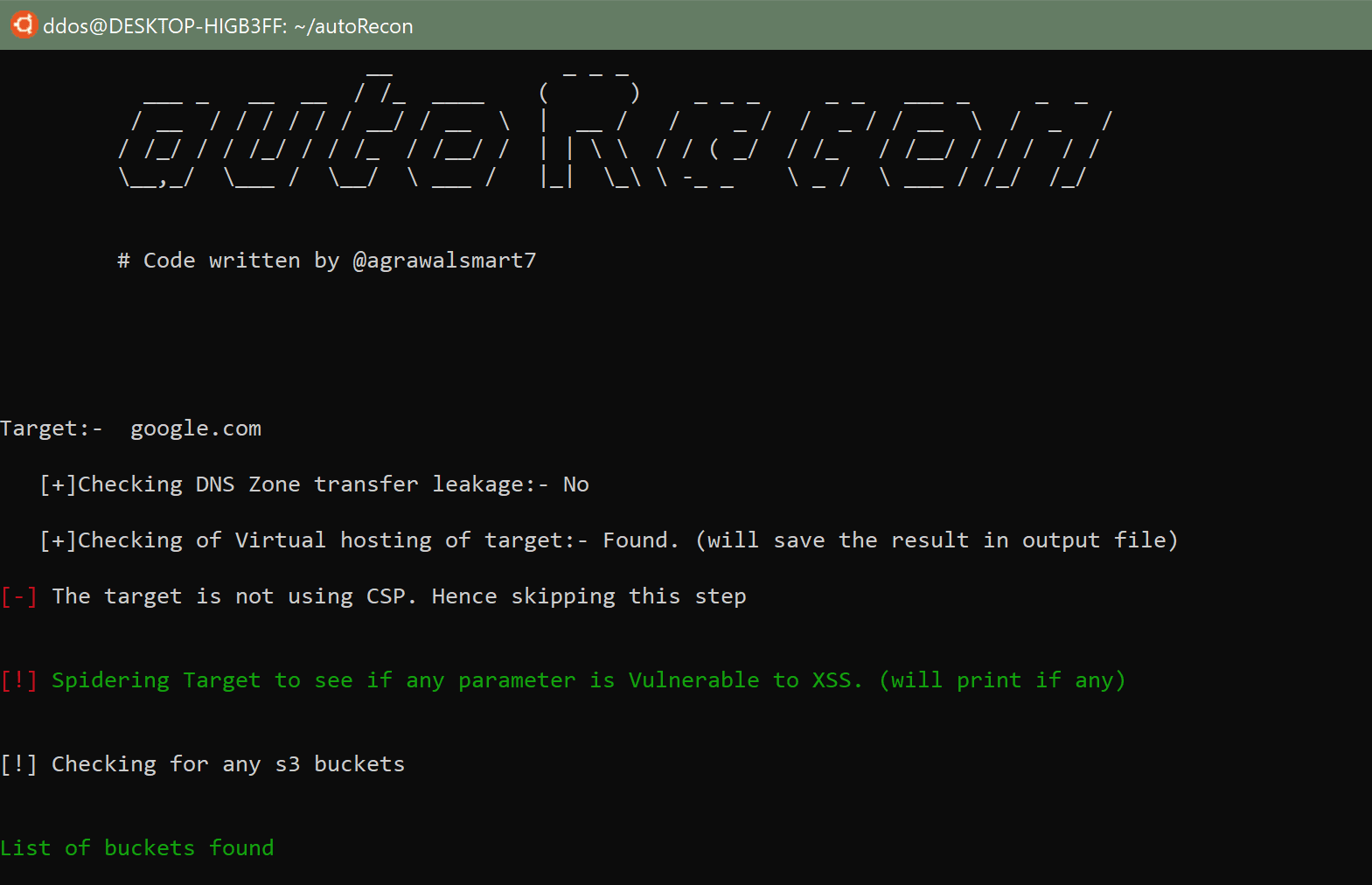
1. It will try to find if the domain NS (name server) leaks some Zone transfer file or not.
2. It will try to find the Virtual host on that domain. So to give out info about “How many web application running on single IP”. Remember please check if that domain is in scope or not.
3. It will try to parse the CSP header (if set). It will store the domains which are set on CS policy.
For ex. CSP:- default-src *.test.com www.test1.com test2.com
then it will parse it and store these domains like test.com, www.test1.com, test2.com then it will try to find the JSONp endpoints on those domains through the use of google.com, ask.com. (Intentionally for bypassing CSP).
4 Then it will try to crawl the target and try to find out the vulnerable URL for xss. (If any). Remember it will take one round to crawl.
5. Try to find S3 buckets.
–On the Sub-domains.
Phase 1: It will find the sub-domains through the use of the sublist3r.
Phase 2: It will find the status code of each sub-domain found by the sublist3r and make a separate list of each sub-domain with their respective status code.
Phase 3: In this phase, the tool will try to find the CNAME’s entries of 404’s sub-domains. NOTE: For this Phase, the main objective is to check for the SUBDOMAIN TAKE-OVER Vuln.
Phase 4: In this phase, through the use of Multi-threading, this tool will find the Port status (with Banner Grabbing) running on each Sub-domains. Note: The defined ports are “21, 22, 80, 8080, 443, 8443, 3306, 445”. And it will make the two seperate list of URL’s which have 21 port open and 80 port open.
Phase 5: In this phase, the tool will find the *What CMS, Server, Frameworks, and versions (if leaks) are using in the domain and Sub-domains.
Phase 6: In this Phase, if there is any FTP open found by “Phase 4”, then it will try to get the Anonymous login.
Phase 7: In that phase, it will find the URLs in the WayBack machine but whose domain status code is 401, 403. And will Capture screen-shots of way-back URLs.
Phase 8:- It will try to find default files for ex. phpinfo.php, htaccess.txt on each and every sub-domain.
Phase 9:- At last if any subdomain is using Cloudflare service then it will go for the DNS history for that subdomain.
Now lastly it will give you the results in HTML file.
Install
git clone https://github.com/agrawalsmart7/autoRecon.git
pip install requirements.txt
Use
Usage: autorecon.py [options]
Options:
-h, –help show this help message and exit
-t HOST, –Host=HOST Please provide the target
-f FILE, –file=FILE Please provide the filename
-o RESULT, –Output=RESULT





