Image: Microsoft
In a recent disclosure, Tenable Research has uncovered a significant vulnerability within Microsoft Azure’s Service Tags functionality. This flaw could enable malicious actors to circumvent firewall protections, potentially gaining unauthorized access to various Azure services.
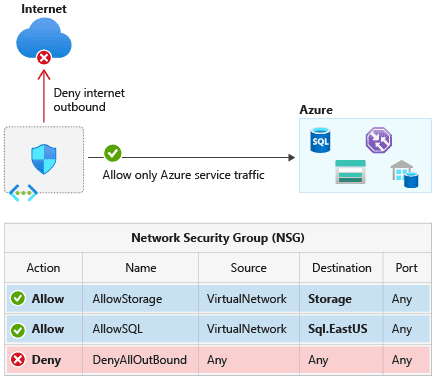
Azure Service Tags are groupings of IP addresses associated with specific Azure services. They are frequently employed to streamline network configuration tasks, such as establishing firewall rules to control traffic flow.

The vulnerability, identified by Tenable Research, stems from the potential for threat actors to manipulate Service Tags to mimic legitimate Azure services. By forging requests from these trusted services, attackers could bypass firewall restrictions designed to protect sensitive resources.
This vulnerability impacts a range of Azure services, including:
- Azure Application Insights
- Azure DevOps
- Azure Machine Learning
- Azure Logic Apps
- Azure Container Registry
- Azure Load Testing
- Azure API Management
- Azure Data Factory
- Azure Action Group
- Azure AI Video Indexer
- Azure Chaos Studio
Microsoft has acknowledged the vulnerability and opted to address it through updated documentation emphasizing the proper use of Service Tags. The company has stressed that Service Tags should not be relied upon as the sole security boundary but should instead be used in conjunction with robust validation controls.
Microsoft strongly recommends that Azure users take proactive measures to safeguard their cloud environments:
- Implement Multi-Layered Security: Employ multiple security mechanisms beyond firewall rules based on Service Tags. This can include network traffic monitoring, authentication, and authorization layers.
- Review Service Tag Usage: Carefully assess your current use of Service Tags and ensure they are not the only line of defense for critical resources.
- Stay Informed: Keep abreast of the latest security advisories and best practices from Microsoft.
While the Azure Service Tags vulnerability raises concerns, Microsoft’s response and the absence of reported exploits offer some reassurance. However, it is crucial for Azure users to take immediate action to fortify their cloud security measures. By doing so, they can minimize the potential impact of this vulnerability and ensure the ongoing protection of their valuable assets.