Azure Outlook C2
Azure Outlook Command & Control that uses Microsoft Graph API for C2 communications & data exfiltration.
Remotely Control a compromised Windows Device from your Outlook Mailbox.
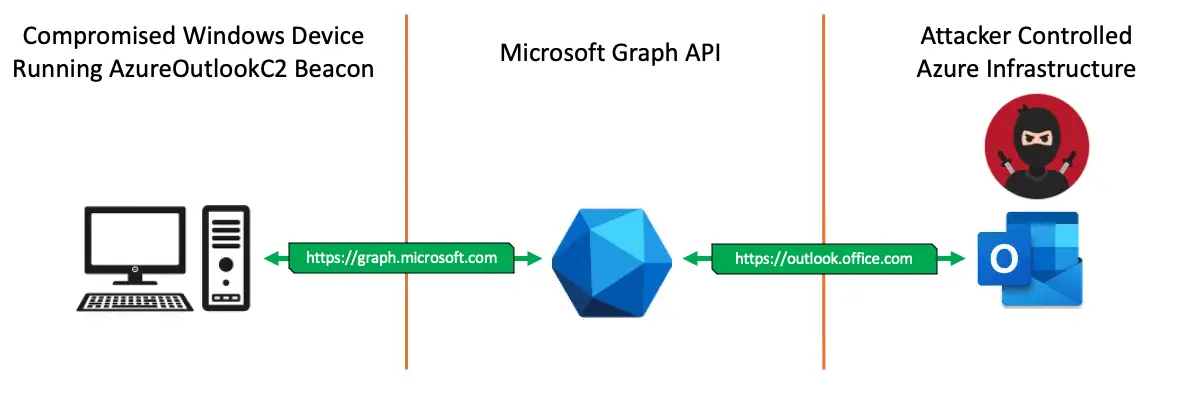
This project consists of an implant that beacons out to an Attacker-Controlled Azure Outlook mailbox, which acts as the Command & Control (C2); remotely controlling the compromised device. An Azure Refresh Token for the Attackers C2 mailbox is hard-coded into the implant during compilation. When executed on a Windows device, the implant accesses the Attackers Draft mailbox via the Microsoft Graph API. The implant reads command instructions from the Attackers Draft mailbox, executes the instructions locally on the compromised windows device, and returns the command output to the Attacker via the creation of new Draft messages. The implant repeats this behavior of being remotely controlled from the Attackers mailbox until the implant host process is exited.

Implant Execution Flow
- Get an Access Token to the MS Graph API using the hard-coded Refresh Token of the Attacker.
- This is done via HTTPS TCP communications to the host
graph.microsoft.com. - This traffic is encrypted using the TLS Certificate returned from the legitimate Microsoft web server.
- The implant uses the
WinInetDynamic-link library for HTTPS communications. - The hard-coded Attacker Refresh Token should be good for 90 days.
- If the implant is compromised, the Attacker can revoke the hard-coded Refresh Token to restrict access from Malware Reverse Engineers.
- After the implant receives an Access Token for the Attackers MS Graph API, the implant enters an infinite loop.
- If there is no internet connection or internet connection is disrupted during the loop, the implant will sleep for 3 minutes and try again.
- The implant keeps track of time, and if 15 minutes has passed, it will get a new Access Token to continue communications.
- The first task in the loop is to use the MS Graph API Access Token to access the Attackers Draft mailbox and read the most recent message for commands to execute on the compromised Windows device.
- The Draft mailbox was chosen because this way there are no emails being sent via SMTP.
- Once the command is received, it is parsed to determine which meta command it will execute. Currently there are 3 meta commands:
cmd,sleep,exit
cmd: Takes the following string after the meta command and executes it by spawning a child process.sleep: Takes the following word after the meta command and will change the implants sleep to the value supplied (in milliseconds).exit: Exits/kills the host process.
- If the meta command is
cmdthe implant will create a child process to execute the command, the child process will write its standard output to a pipe, the child process exits after command execution, and the host implant process will read the output of the child process via the pipe. - After the implant gets the output from the executed command, the implant will use the MS Graph API to create a new draft email which contains the command output.
- The implant will then create a second draft email with a blank body.
- This allows logging of the command output within the Attackers Draft mailbox.
- This queues the Attacker with a fresh draft message to enter the next command the implant will execute.
- After the command has been executed and the output returned to the Attacker, the implant will sleep for a time controlled by the attacker, and then repeat this loop.