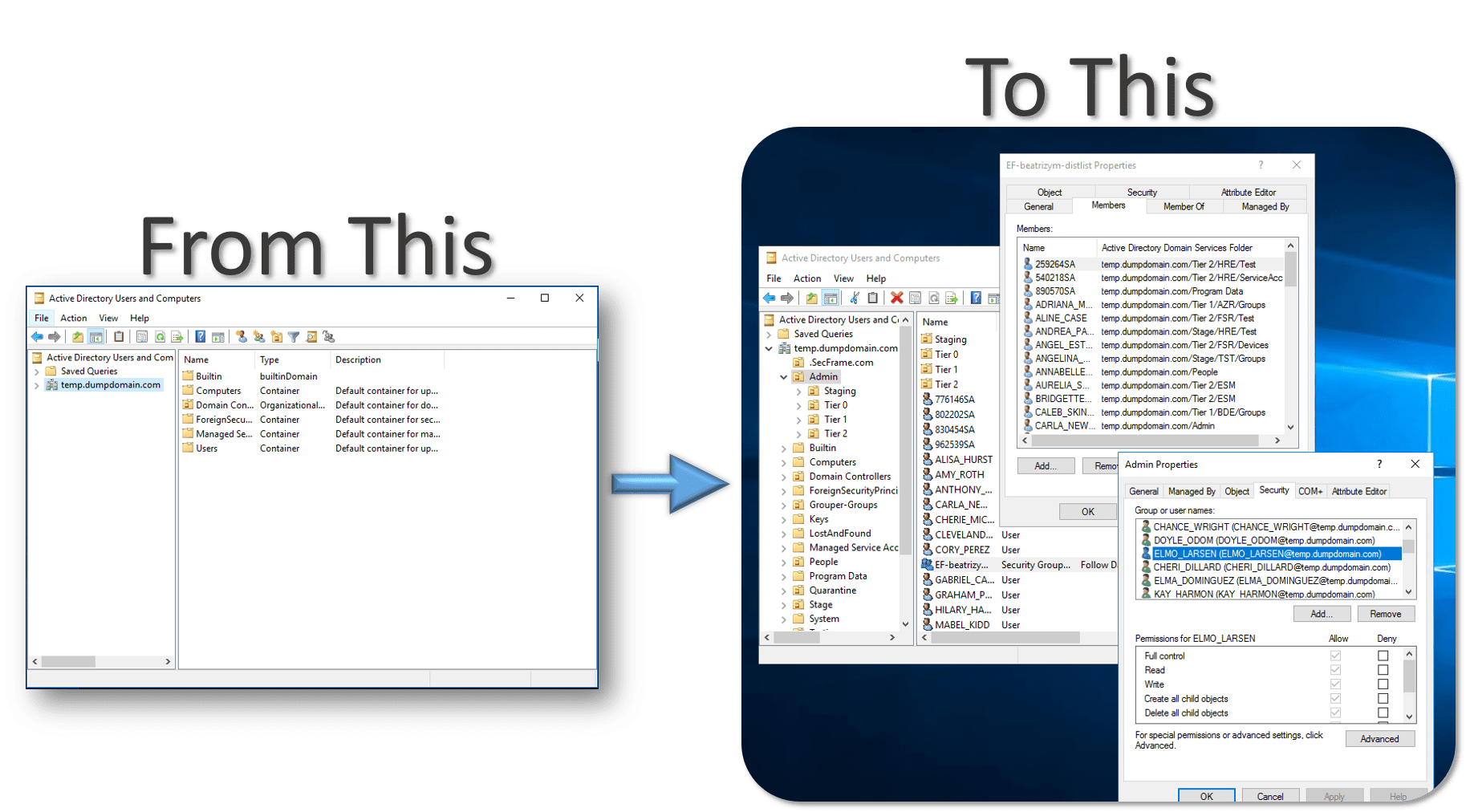
BadBlood
BadBlood by Secframe fills a Microsoft Active Directory Domain with a structure and thousands of objects. The output of the tool is a domain similar to a domain in the real world. After BadBlood is ran on a domain, security analysts and engineers can practice using tools to gain an understanding and prescribe to securing Active Directory. Each time this tool runs, it produces different results. The domain, users, groups, computers, and permissions are different. Every. Single. Time.
BadBlood is designed to be run with a user who is a Domain Admin and Schema Admin. Following the prompts, the tool begins by expanding the current domain’s schema by installing LAPS AD_Laps_install\InstallLAPSSchema.ps1
- LAPS is Microsoft’s free tool designed to remediated lateral movement across a domain by randomly generating passwords for the admin user on computer objects.
Installation
Requirements:
- Domain Admin and Schema Admin permissions
- Active Directory Powershell Installed
Running On Windows:
# clone the repo git clone https://github.com/davidprowe/badblood.git #Run Invoke-badblood.ps1 ./badblood/invoke-badblood.ps1
Use
Copyright (C) 2020 davidprowe