BEE·bot
OSINT automation for hackers.

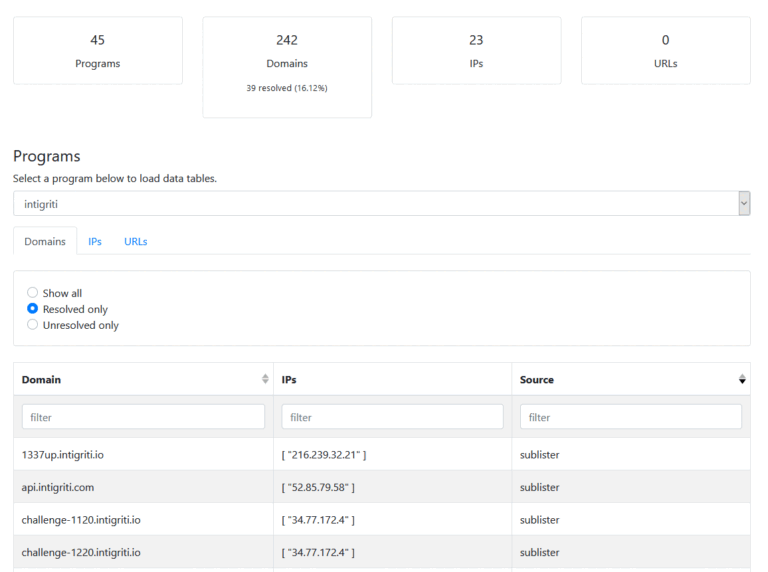
BBOT is a recursive, modular OSINT framework written in Python.
It is capable of executing the entire OSINT process in a single command, including subdomain enumeration, port scanning, web screenshots (with its gowitness module), vulnerability scanning (with nuclei), and much more.
BBOT currently has over 50 modules and counting.
Modules
| Module | Needs API Key | Description | Flags | Produced Events |
|---|---|---|---|---|
| aspnet_viewstate | Parse web pages for viewstates and check them against blacklist3r | active, safe, web |
VULNERABILITY | |
| bypass403 | Check 403 pages for common bypasses | active,aggressive,web | FINDING | |
| cookie_brute | Check for common HTTP cookie parameters | active, aggressive, brute-force, slow, web |
FINDING | |
| dnszonetransfer | Attempt DNS zone transfers | active, safe, subdomain-enum |
DNS_NAME | |
| ffuf | A fast web fuzzer written in Go | active, aggressive, brute-force, deadly, web |
URL | |
| ffuf_shortnames | Use ffuf in combination IIS shortnames | active, aggressive, brute-force, web |
URL | |
| generic_ssrf | Check for generic SSRFs | active,aggressive,web | VULNERABILITY | |
| getparam_brute | Check for common HTTP GET parameters | active, aggressive, brute-force, slow, web |
FINDING | |
| gowitness | Take screenshots of webpages | active, safe, web |
SCREENSHOT | |
| header_brute | Check for common HTTP header parameters | active, aggressive, brute-force, slow, web |
FINDING | |
| host_header | Try common HTTP Host header spoofing techniques | active, aggressive, web |
FINDING | |
| httpx | Visit webpages. Many other modules rely on httpx | active,safe,web | HTTP_RESPONSE, URL |
|
| hunt | Watch for commonly-exploitable HTTP parameters | active,safe,web | FINDING | |
| iis_shortnames | Check for IIS shortname vulnerability | active,safe | URL_HINT | |
| naabu | Execute port scans with naabu | active, aggressive, portscan |
OPEN_TCP_PORT | |
| ntlm | Watch for HTTP endpoints that support NTLM authentication | active, safe, web |
DNS_NAME, FINDING |
|
| nuclei | Fast and customisable vulnerability scanner | active, aggressive, deadly,web |
VULNERABILITY | |
| smuggler | Check for HTTP smuggling | active, aggressive, brute-force, slow, web |
FINDING | |
| sslcert | Visit open ports and retrieve SSL certificates | active, email-enum, safe, subdomain-enum |
DNS_NAME, EMAIL_ADDRESS |
|
| telerik | Scan for critical Telerik vulnerabilities | active,aggressive,web | FINDING, VULNERABILITY |
|
| vhost | Fuzz for virtual hosts | active,aggressive,brute-force,deadly,slow,web | DNS_NAME, VHOST |
|
| wappalyzer | Extract technologies from web responses | active,safe,web | TECHNOLOGY | |
| affiliates | Summarize affiliate domains at the end of a scan | passive,report,safe | ||
| asn | Query bgpview.io for ASNs | passive,report,safe,subdomain-enum | ASN | |
| azure_tenant | Query Azure for tenant sister domains | passive,safe,subdomain-enum | DNS_NAME | |
| binaryedge | X | Query the BinaryEdge API | passive,safe,subdomain-enum | DNS_NAME, EMAIL_ADDRESS, IP_ADDRESS, OPEN_PORT, PROTOCOL |
| c99 | X | Query the C99 API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
| censys | X | Query the Censys API | email-enum,passive,safe,subdomain-enum | DNS_NAME, EMAIL_ADDRESS, IP_ADDRESS, OPEN_PORT, PROTOCOL |
| certspotter | Query Certspotter’s API for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| crobat | Query Project Crobat for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| crt | Query crt.sh (certificate transparency) for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| dnscommonsrv | Check for common SRV records | passive,safe,subdomain-enum | DNS_NAME | |
| dnsdumpster | Query dnsdumpster for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| emailformat | Query email-format.com for email addresses | email-enum,passive,safe | EMAIL_ADDRESS | |
| github | X | Query Github’s API for related repositories | passive,safe,subdomain-enum | URL_UNVERIFIED |
| hackertarget | Query the hackertarget.com API for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| hunterio | X | Query hunter.io for emails | email-enum,passive,safe,subdomain-enum | DNS_NAME, EMAIL_ADDRESS, URL_UNVERIFIED |
| ipneighbor | Look beside IPs in their surrounding subnet | aggressive,passive,subdomain-enum | IP_ADDRESS | |
| leakix | Query leakix.net for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| massdns | Brute-force subdomains with massdns (highly effective) | aggressive,brute-force,passive,slow,subdomain-enum | DNS_NAME | |
| passivetotal | X | Query the PassiveTotal API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
| pgp | Query common PGP servers for email addresses | email-enum,passive,safe | EMAIL_ADDRESS | |
| securitytrails | X | Query the SecurityTrails API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
| shodan_dns | X | Query Shodan for subdomains | passive,safe,subdomain-enum | DNS_NAME |
| skymem | Query skymem.info for email addresses | email-enum,passive,safe | EMAIL_ADDRESS | |
| sublist3r | Query sublist3r’s API for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| threatminer | Query threatminer’s API for subdomains | passive,safe,subdomain-enum | DNS_NAME | |
| urlscan | Query urlscan.io for subdomains | passive,safe,subdomain-enum | DNS_NAME, URL_UNVERIFIED |
|
| viewdns | Query viewdns.info’s reverse whois for related domains | passive,safe,subdomain-enum | DNS_NAME | |
| wayback | Query archive.org’s API for subdomains | passive,safe,subdomain-enum | DNS_NAME, URL_UNVERIFIED |
|
| zoomeye | X | Query ZoomEye’s API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
Install & Usage
Copyright (C) 2022 blacklanternsecurity