BeRoot: Windows Privilege Escalation Tool
BeRoot Project is a post exploitation tool to check common misconfigurations to find a way to escalate our privilege.
It has been added to the pupy project as a post exploitation module (so it will be executed in memory without touching the disk).
This tool does not realize any exploitation. It mains goal is not to realize a configuration assessment of the host (listing all services, all processes, all network connection, etc.) but to print only information that has been found as a potential way to escalate our privilege.
This project works on Windows, Linux and Mac OS.
Download
git clone https://github.com/AlessandroZ/BeRoot.git
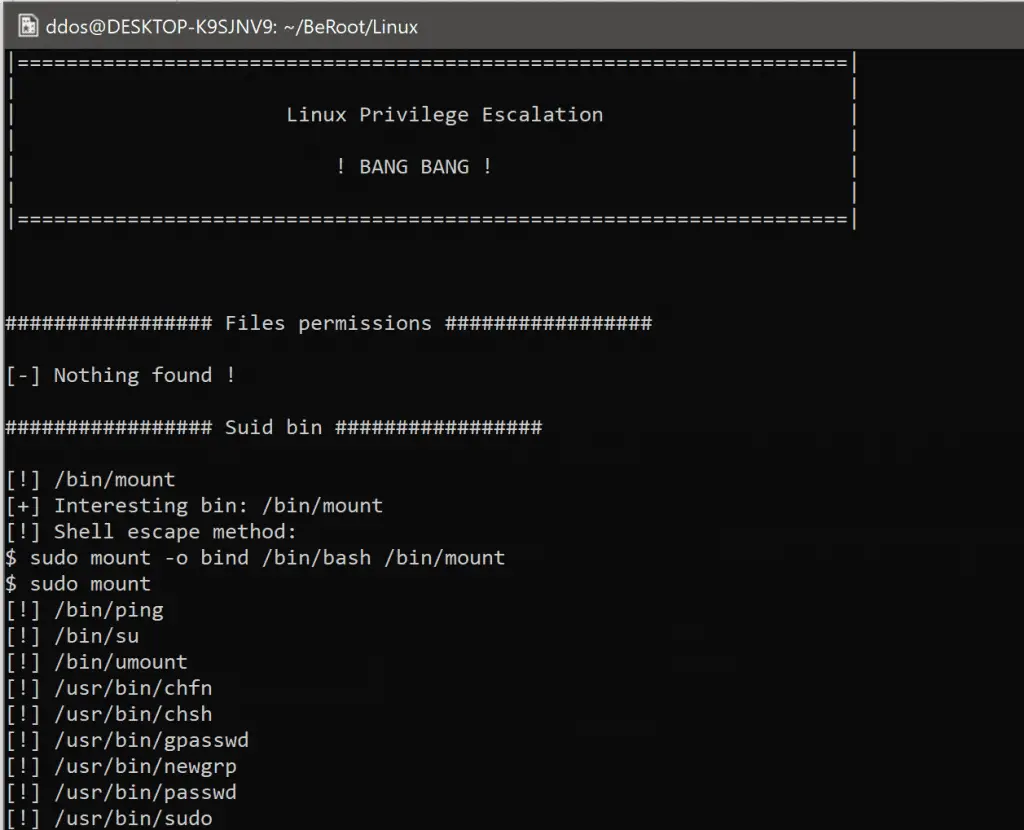
Use
- Linux
To understand privilege escalation on these systems, you should understand at least two main notions: LOLBins (this name has been given for Windows binaries but it should be correct to use it for Linux as well) and Wildcards.
- Windows
It will be added to the pupy project as a post exploitation module (so it will be executed in memory without touching the disk). Except for one method, this tool is only used to detect and not to exploit. If something is found, templates could be used to exploit it. To use it, just create a test.bat file located next to the service / DLL used. It should execute it once called. Depending on the Redistributable Packages installed on the target host, these binaries may not work.
Source: https://github.com/AlessandroZ/





