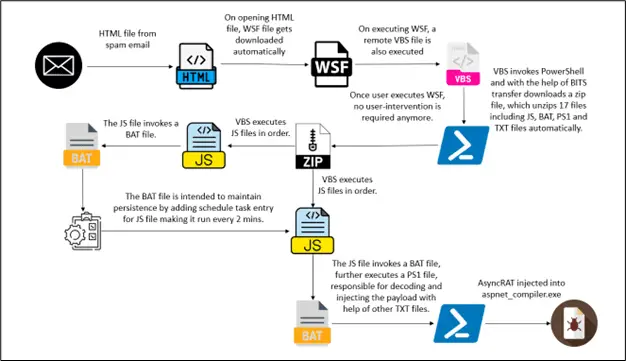
Infection Chain
McAfee Labs exposes the intricate mechanisms of AsyncRAT, a formidable malware designed to infiltrate computer systems and pilfer sensitive information discreetly. The detailed analysis by McAfee Labs unravels an alarming trend of using non-traditional file types to bypass antivirus solutions and execute malicious campaigns efficiently.
What is AsyncRAT?
AsyncRAT, which stands for Asynchronous Remote Access Trojan, is a sophisticated malware variant meticulously engineered to compromise system security and steal confidential data. Unlike other malware that often uses predictable file types, AsyncRAT leverages a blend of PowerShell, Windows Script File (WSF), VBScript (VBS), and other scripts within a malicious HTML file to enhance its stealth and evasion capabilities.
Infection Chain Unveiled

The infection begins innocuously with a spam email disguised as a legitimate communication, often containing an HTML attachment. When the recipient opens the HTML page, it triggers an automatic download of a WSF file, cleverly named to appear like an order confirmation or receipt, adding an air of legitimacy. This WSF file acts as a gateway for further malicious activities, downloading additional scripts like VBS, JS, BAT, TXT, and PS1, culminating in a sophisticated attack without further user interaction.
The downloaded scripts perform a series of actions:
- They decrypt configuration settings.
- Verify and create a mutex to prevent duplicate instances.
- Exit if a virtualized or analysis environment is detected to avoid detection.
- Establish persistent presence on the infected system.
- Gather data from the system.
- Establish a connection with the attacker’s server.
Technical Analysis and System Penetration
The primary vector for AsyncRAT involves the deployment of a multistage script that executes sequentially to avoid detection. After initial execution, the scripts download a disguised file, “r.jpg,” which is a ZIP archive named “ty.zip.” This archive is unpacked in the public folder, releasing its malicious payload, which eventually leads to the injection of the final payload into aspnet_compiler.exe, a common process used to compile ASP.NET applications.
Rise in Non-PE Threats
This type of attack vector has become increasingly popular as cybercriminals adapt to new security measures, such as those implemented by Microsoft against malicious Office macros. By shifting to HTML and WSF files, attackers can sidestep many traditional security protocols, catching both users and automated systems off guard.
Prevention and Mitigation
McAfee Labs strongly advises individuals and organizations to exercise heightened vigilance. Recommended practices include:
- Verifying sender information to confirm email authenticity.
- Being skeptical of unexpected links and attachments.
- Checking for spelling and grammar errors that often characterize phishing attempts.
- Using robust email spam filters and secure web gateways that provide advanced threat protection.