Beware Fake Angry IP Scanner Ads: SharpRhino RAT Used by Hunters Group Lurks Within
The ransomware group Hunters International has begun utilizing a new C#-based remote access trojan (RAT) named SharpRhino to infiltrate corporate networks. This malicious software aids hackers in achieving initial infection, elevating privileges on compromised systems, executing specific PowerShell commands, and ultimately deploying ransomware.
Researchers at Quorum Cyber, who discovered the new trojan, report that it spreads via a sponsored Google Ads site impersonating Angry IP Scanner—a legitimate network scanning tool used by IT professionals.
Hunters International, launched in late 2023, is suspected of being a rebranded version of the Hive group due to similarities in their code. Among the group’s known victims are the US Navy contractor Austal USA, the Japanese optics company Hoya, Integris Health, and the Fred Hutch Cancer Center. Even medical institutions are considered fair targets for Hunters International.
Since the beginning of this year, the group has claimed responsibility for 134 ransomware attacks against various organizations worldwide, ranking it tenth among the most active groups in this domain.
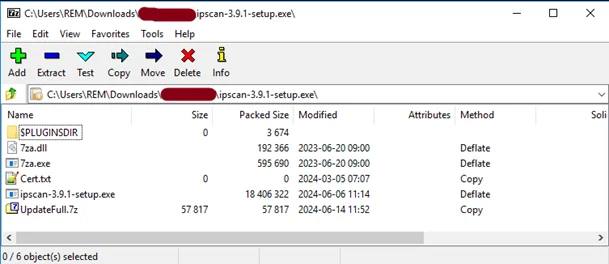
Contents of the malicious installer | Image: Quorum Cyber
The malicious SharpRhino spreads as a signed 32-bit installer (“ipscan-3.9.1-setup.exe”), containing a self-extracting 7z archive with additional files for executing the infection. Potential victims download and run this malware, believing it to be a legitimate installer. However, EXEInfo has detected signs indicating that the installer was an executable file packaged in NSIS (Nullsoft Scriptable Installer System).
Upon execution, the malicious installer modifies the Windows registry to ensure persistence and creates a shortcut to “Microsoft.AnyKey.exe,” typically a binary file from Microsoft Visual Studio but in this instance used by the attackers. Additionally, the installer creates a “LogUpdate.bat” file that executes PowerShell scripts on the device for the covert operation of the malware.
To ensure reliable exploitation, the installer creates two directories:
- C:\ProgramData\Microsoft\WindowsUpdater24 — contains files to be executed during the initial launch of the NSIS installer.
- C:\ProgramData\Microsoft\LogUpdateWindows — contains files necessary for establishing persistence.
The malware contains two hardcoded commands: “delay”—to set the timer for the next POST request to receive commands, and “exit”—to terminate communication.
Analysis reveals that the malware can execute PowerShell commands on the infected device, enabling various malicious activities. Quorum Cyber experts tested this mechanism, successfully launching the Windows calculator through SharpRhino.
Hunters International’s new tactic of creating sites mimicking legitimate network tools indicates their focus on targeting IT professionals to compromise accounts with elevated privileges.
To avoid accidental downloads of malware, users are advised to be cautious with sponsored search results, activate ad blockers, and bookmark official sites of frequently used projects to download only safe installers.
To mitigate the impact of attacks, it is recommended to establish backup plans, segment the network, and keep all software up to date to minimize hackers’ ability to escalate privileges and move laterally.





