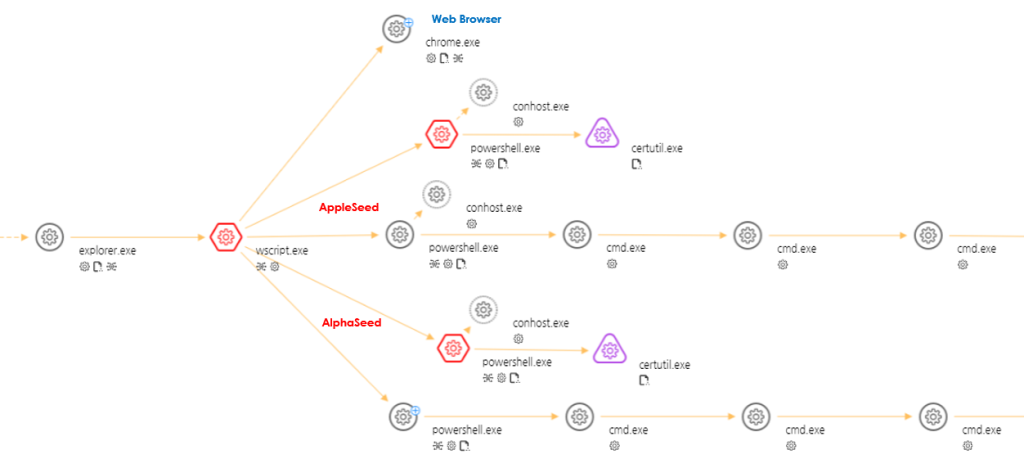
The process tree when JavaScript malware is executed
A formidable entity known as the Kimsuky threat group, purportedly backed by North Korea, has cast a long shadow since its emergence in 2013. Initially setting its sights on South Korea’s research institutes, Kimsuky’s ambitions swiftly escalated, targeting a South Korean energy corporation in 2014, before broadening their nefarious reach internationally in 2017. The group’s primary quarry has been the repositories of national defense, the media, government organizations, and the sanctums of academia, from which they exfiltrate critical data and technologies. AhnLab Security Intelligence Center (ASEC) recently discovered the distribution of two malwares.

Armed with a diverse arsenal of malware, including the notorious AppleSeed and AlphaSeed strains, Kimsuky’s tactics have evolved yet remained insidiously effective over the years. Their modus operandi is spear phishing, a precision strike that delivers malware directly into the heart of their targets, which range from high-level organizations to individual netizens. These attacks cleverly masquerade as innocuous documents, only to unleash AppleSeed upon execution, commandeering the infected system to filch data and await further commands from its concealed masters.
The sophistication of Kimsuky does not end at their initial breach. Their malware, like the chameleonic AppleSeed, is a master of disguise, capable of keylogging, screenshotting, and stealthily perpetuating its presence, ensuring a persistent threat to compromised systems. AlphaSeed malware enhances this digital deceit by employing ChromeDP for command and control communications, illustrating a pivot towards more sophisticated, web-based exploitation techniques.