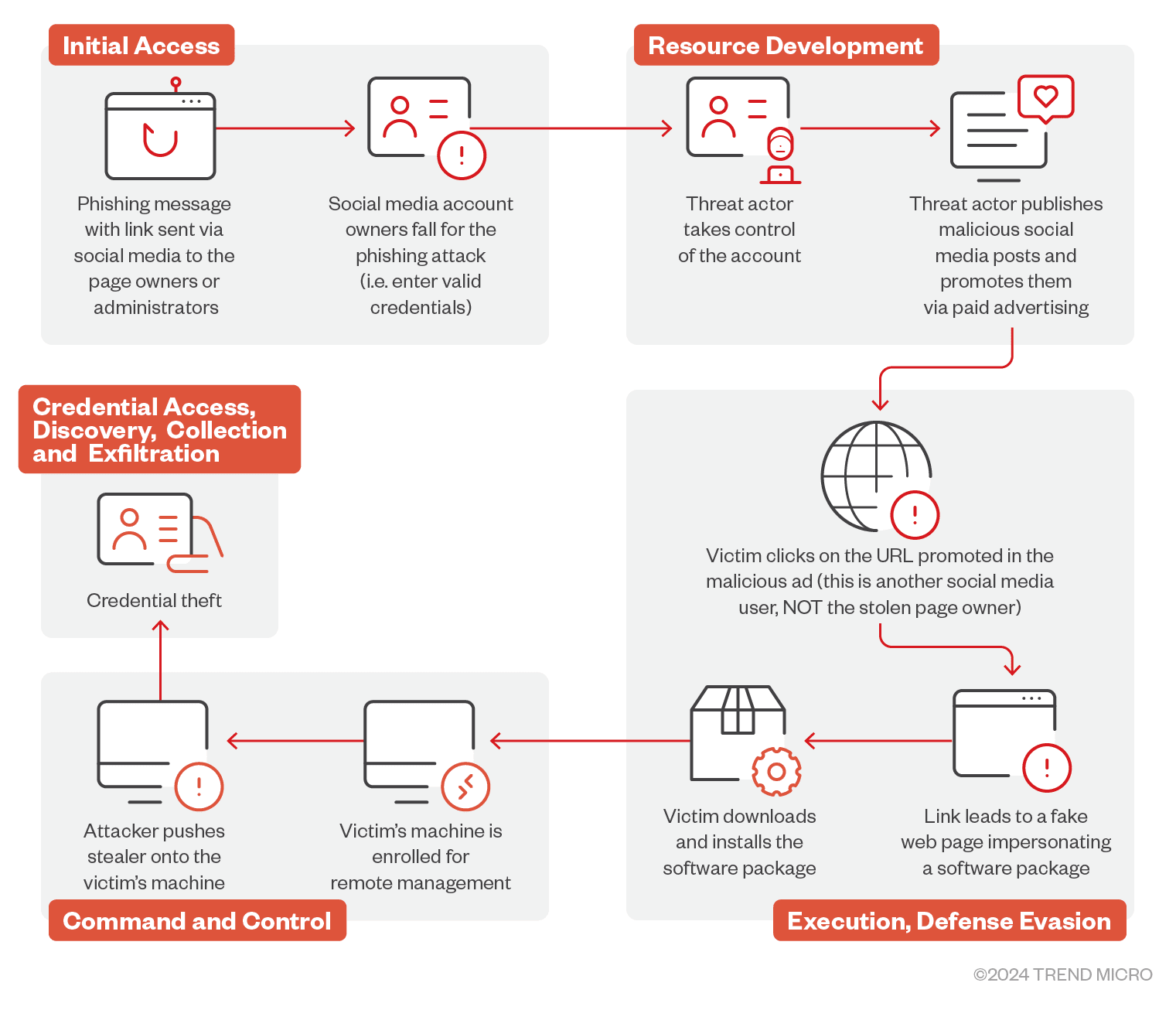
A new malvertising campaign has been uncovered by TrendMicro, targeting social media pages to promote a fraudulent AI photo editor website. This sophisticated scam involves credential theft and remote device management, compromising victims’ sensitive information.
The campaign begins with threat actors hijacking social media pages, primarily those related to photography. They rename these pages to appear connected to popular AI photo editors. To lure unsuspecting users, they create posts with links to fake websites designed to mimic legitimate photo editor sites. These malicious posts are then boosted via paid Facebook advertisements, increasing their reach and effectiveness.
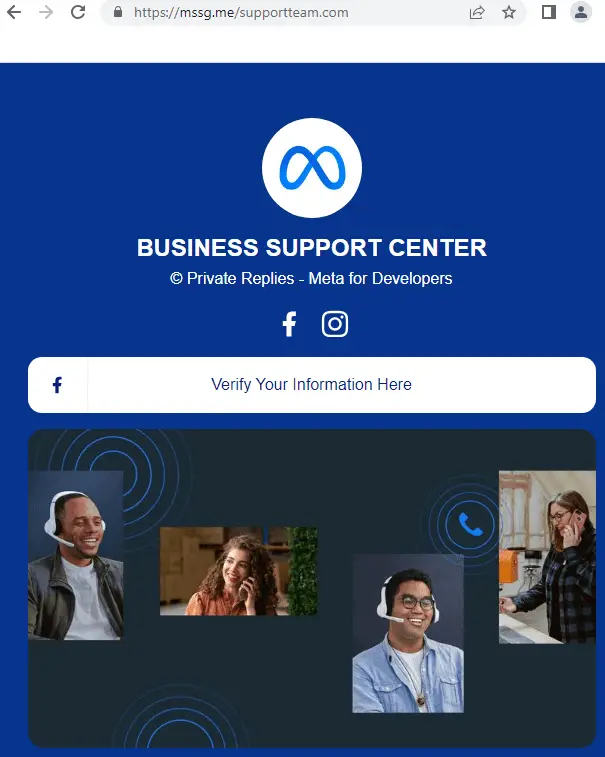
The attackers initiate their takeover by spamming the targeted social media page administrators with messages containing phishing links. These links often appear legitimate, exploiting Facebook’s open redirect URLs and personalized link pages like linkup.top, bio.link, s.id, and linkbio.co. The phishing messages typically come from empty profiles with randomly generated usernames.
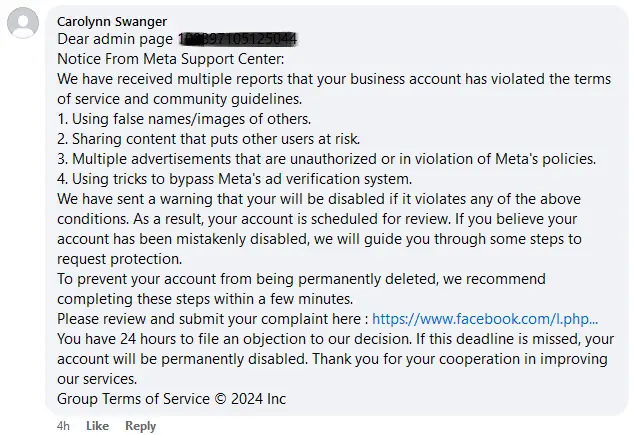
Administrators who fall for the scam and click on the links are directed to fake account protection pages. These pages ask for personal information necessary to log in and take over their accounts, including phone numbers, email addresses, birthdays, and passwords. Once the attackers obtain this information, they hijack the social media profiles and begin posting malicious advertisements.
The fake AI photo editor website is a near-perfect replica of the legitimate site it mimics, such as Evoto. Victims are tricked into downloading what they believe is a photo editor, but in reality, they are installing an endpoint management utility. This utility, configured with malicious intent, allows attackers to remotely control the infected devices.
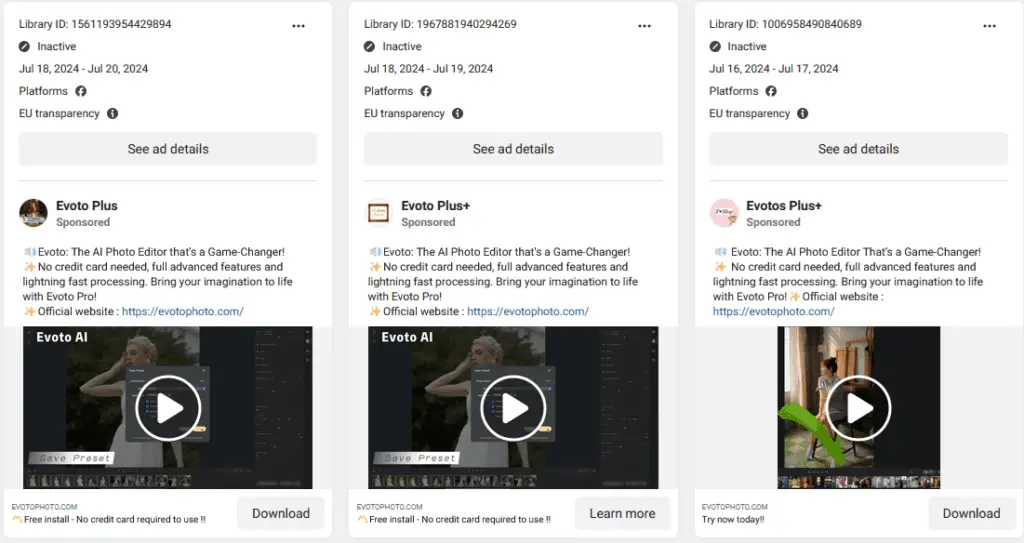
Upon visiting the fake website, victims are directed to download a package that appears to be a photo editor. The package, however, is an installer for ITarian, a legitimate endpoint management software. The attackers enroll the victim’s device for remote management, leveraging ITarian’s features to download and execute additional malicious payloads.
The primary payload delivered is Lumma Stealer, a credential-stealing malware. It employs Python scripts to download and execute further malicious code. The scripts modify Windows Defender settings to exclude certain directories from scans, ensuring the malware remains undetected.
Lumma Stealer initiates its communication with a command and control (C&C) server via POST requests, receiving an encrypted configuration. This configuration outlines the data the stealer is designed to exfiltrate, including credentials and other sensitive information.
Users are advised to exercise caution when clicking on links or downloading software from unfamiliar sources, especially those promoted through social media ads. Sticking to official app stores and reputable websites can significantly reduce the risk of falling victim to such scams.
Related Posts:
- Vulnerable Clicks: PikaBot Hijacks Businesses with Malvertising
- Accidental Malvertising Strikes via Google Dynamic Search Ads