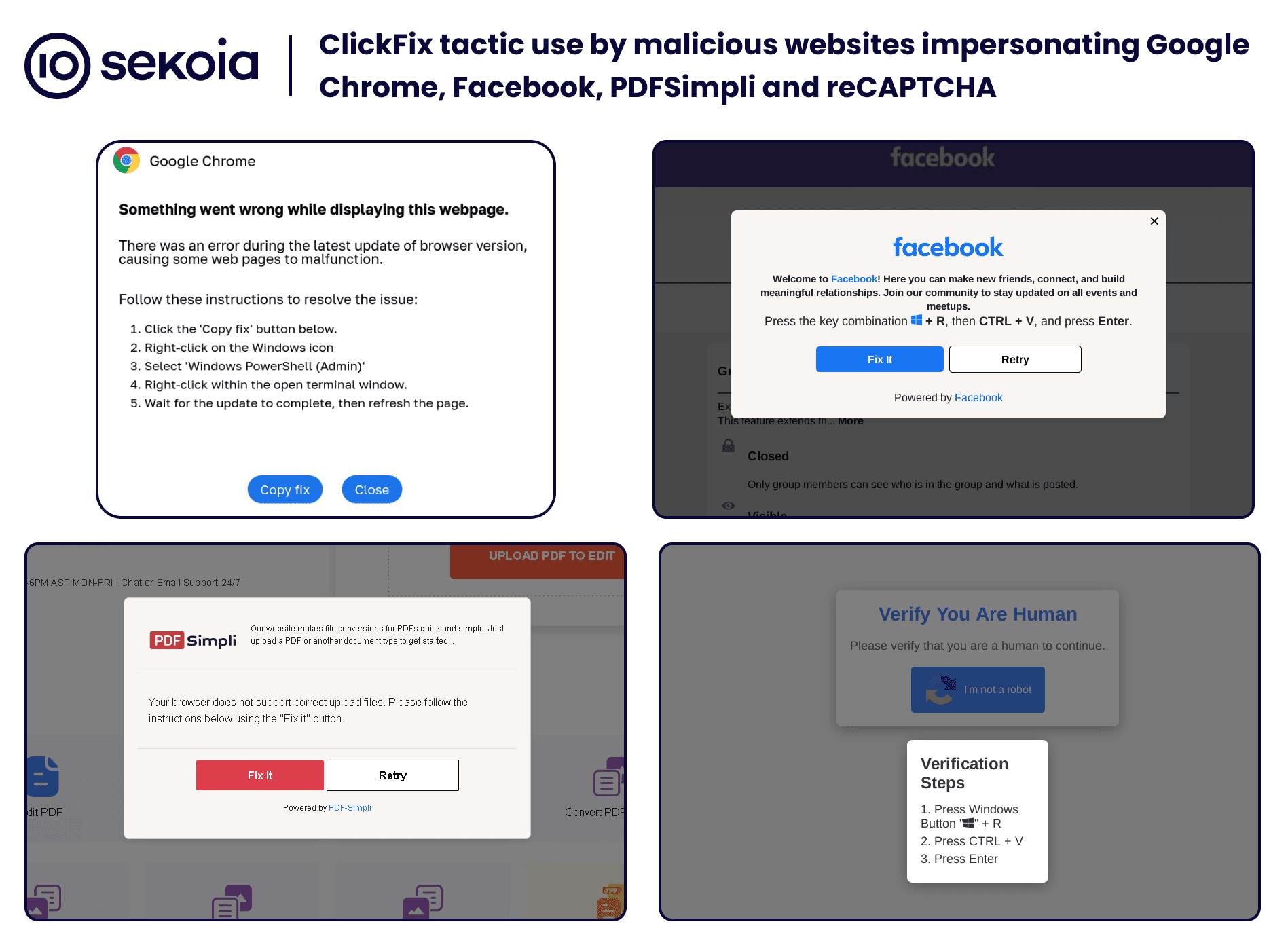
Examples of malicious websites impersonating Google Chrome, Facebook, PDFSimpli, and reCAPTCHA, using the ClickFix tactic | Image: Sekoia
A new and dangerous social engineering tactic, dubbed ClickFix, has emerged as a significant cybersecurity threat in 2024, according to a recent report from the Sekoia Threat Detection & Research (TDR) team. First observed in phishing campaigns and malware distribution efforts, ClickFix is rapidly becoming a favorite tool among cybercriminals. The tactic leverages fake error messages to deceive users into executing malicious PowerShell scripts, leading to the infection of their systems.
One of the most concerning aspects of ClickFix is its use of fake Google Meet video conference pages to distribute malware. This approach, known as The Phantom Meet, creates a convincing decoy designed to target users who rely on video conferencing for business or personal use. The Sekoia team discovered that “several websites masquerading as the homepage of a Google Meet video conference” were distributing infostealers that target both Windows and macOS users. These fake sites trigger pop-ups that falsely indicate technical issues with the user’s microphone or headset, ultimately convincing them to click on a malicious “Try Fix” button.
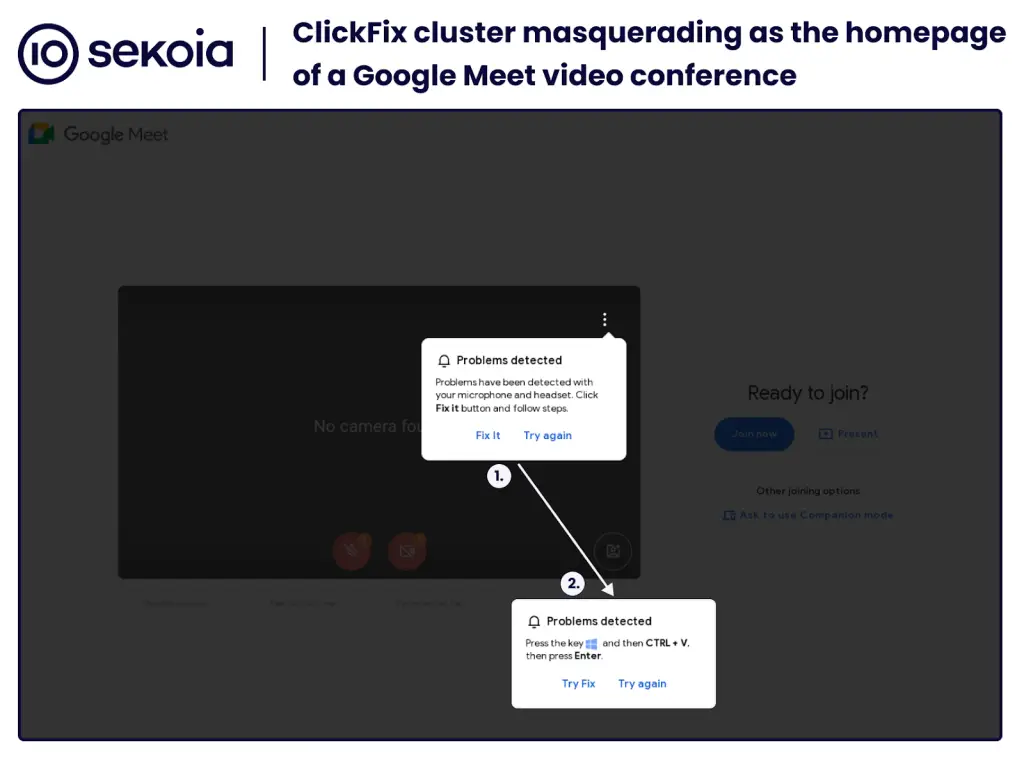
Once a user clicks on the “Try Fix” button, a series of malicious actions are initiated:
- For Windows users, the button copies a malicious command into the clipboard. This command fetches and executes malicious payloads such as the Stealc and Rhadamanthys infostealers. The report notes that the payloads are “protected by the HijackLoader crypter,” which makes them harder to detect by traditional antivirus tools
- For macOS users, the button downloads a malicious
.dmgfile that installs the AMOS Stealer, designed to exfiltrate sensitive information such as cryptocurrency keys and login credentials
The report from Sekoia identifies two key cybercrime groups behind the ClickFix tactic: Slavic Nation Empire (SNE) and Scamquerteo. These groups are highly organized and have ties to larger cryptocurrency scam teams such as Marko Polo and CryptoLove. The TDR team was able to attribute specific clusters of fake Google Meet pages to these groups.
The researchers discovered that Slavic Nation Empire (SNE) “uses a comprehensive kit for sophisticated scams targeting users of cryptocurrency assets, Web3 applications, decentralized finance, and NFTs“. These groups distribute malware through various channels, including phishing emails and compromised websites, and use automated tools like Telegram bots to track infections and manage their operations.
The ClickFix tactic is part of a broader trend in malware distribution, which increasingly relies on sophisticated social engineering techniques. “The ClickFix cluster… employs a decoy that could be particularly devastating in campaigns targeting organizations that use Google Workspace, especially Google Meet,” the report warns. As more organizations rely on online collaboration tools, these types of attacks could have widespread implications, especially in sectors handling sensitive data, such as finance and healthcare.
Related Posts:
- Beyond HTML: The Hidden Danger of Phishing in HTTP Response Headers
- Infostealers Overcome Chrome’s App-Bound Encryption, Threatening User Data Security
- India Post Customers Targeted in Massive Phishing Scam
- Beware of Fake Downloads: AsyncRAT Spreads via Popular Software Cracks
- Beware: Hackers Use Google Drawings & WhatsApp Links to Steal Data