A recent investigation by eSentire’s Threat Response Unit (TRU) has unveiled a sophisticated attack campaign utilizing counterfeit KMSPico activators to deliver the notorious Vidar Stealer malware. This discovery serves as a stark reminder of the risks associated with downloading software from unverified sources.
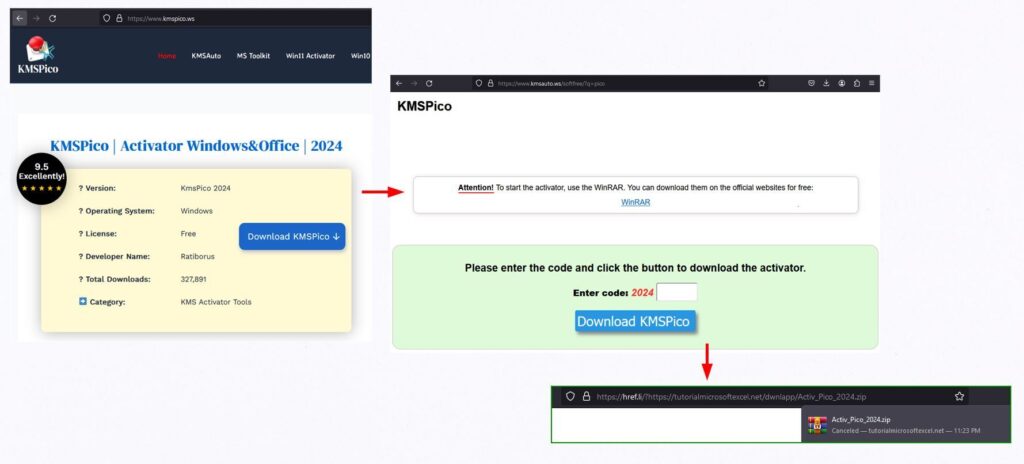
The attack chain begins when unsuspecting users search for KMSPico, a tool falsely advertised as a universal Windows activator. The top search result often leads to a malicious website that employs Cloudflare Turnstile and requires human input to download a ZIP archive. This tactic helps evade detection by automated web crawlers.
The downloaded archive contains Java dependencies and a malicious executable. Upon execution, it disables Windows Defender’s behavior monitoring and deploys an AutoIt script containing an encrypted Vidar Stealer payload. The script then injects this payload into its own process, effectively bypassing security measures.
Vidar Stealer is a formidable information-stealing malware capable of exfiltrating sensitive data such as passwords, credit card information, and cryptocurrency wallets. It utilizes Telegram as a Dead Drop Resolver (DDR) to obfuscate its command and control (C2) infrastructure, making it more difficult to detect and disrupt.
This incident serves as a stark reminder of the persistent threat posed by malicious actors and the critical importance of maintaining a proactive security posture. By remaining vigilant and implementing robust security practices, individuals and organizations can mitigate the risk of falling victim to such attacks.