
Imagine browsing a seemingly legitimate e-commerce site, entering your payment details, and confidently completing a purchase, only to realize later that your sensitive information has fallen into the hands of cybercriminals. This alarming scenario is the reality for victims of a new WordPress plugin named PhishWP, uncovered by Daniel Kelley, a security researcher at SlashNext.
PhishWP is a sophisticated phishing tool disguised as a WordPress plugin, available on cybercrime forums. “It creates fake payment pages that look just like trusted services, such as Stripe,” Kelley explains. With its advanced capabilities, the plugin allows attackers to steal sensitive data like credit card numbers, personal details, and even browser metadata—all in real-time.
This malicious plugin empowers threat actors to either compromise existing WordPress sites or create fraudulent ones. Once installed, PhishWP can be configured to mimic a legitimate payment gateway. Unsuspecting users are lured into entering their payment information, including credit card details and 3D Secure (3DS) one-time passwords (OTPs).
The plugin’s integration with Telegram ensures that stolen data is transmitted to attackers instantly. Kelley highlights, “PhishWP even connects with Telegram, sending stolen data to attackers as soon as a victim hits ‘enter.’ This makes phishing attacks faster and more efficient.”
The plugin’s success lies in its arsenal of advanced features:
- Customizable Checkout Pages: Replicates payment processors like Stripe, creating highly convincing interfaces.
- 3DS Code Harvesting: Tricks victims into entering OTPs, bypassing authentication measures.
- Real-Time Data Transfer: Telegram integration ensures immediate exploitation of stolen data.
- Browser Profiling: Collects metadata like IP addresses and user agents for future fraudulent activities.
- Fake Confirmation Emails: Sends victims order confirmations, delaying suspicion.
- Multi-Language Support: Facilitates global phishing campaigns.
- Obfuscation Options: Offers stealth capabilities to evade detection
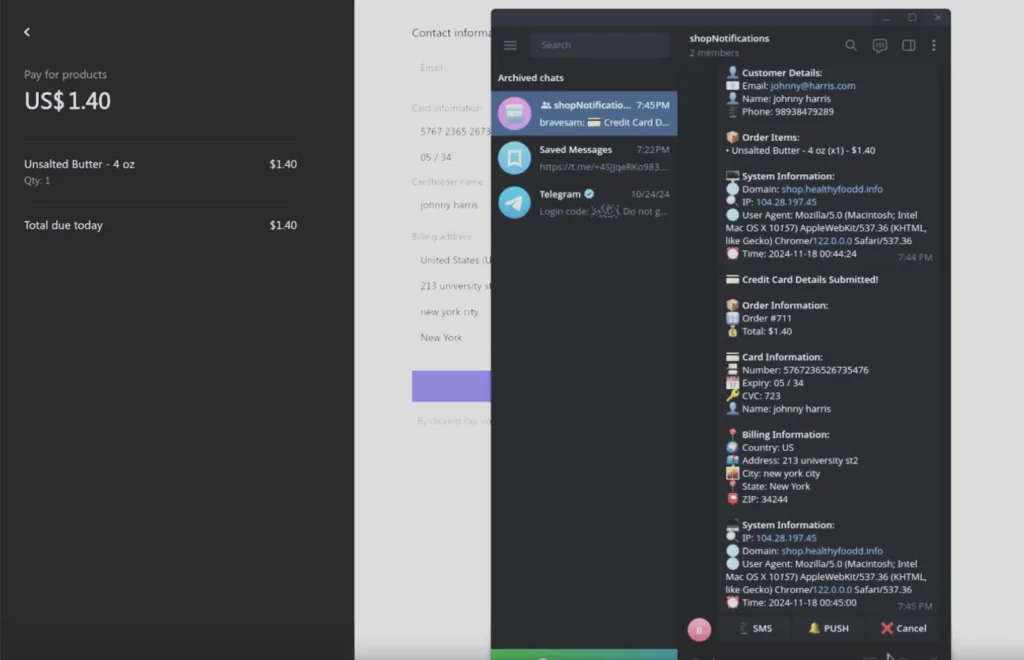
In one documented attack, an e-commerce website advertised discounted products to lure victims. Using PhishWP, attackers created a Stripe-like checkout interface. Victims willingly entered their payment details and OTPs, unaware that the data was being transmitted to the attacker’s Telegram account in real-time.
As Kelley notes, “The victim then receives a fake confirmation email, making them believe their purchase went through. Meanwhile, the attacker uses or sells the stolen info in secret online markets.”
Related Posts:
- Following Russian, Iran also issued a signal to ban Telegram
- Cards on the Dark Web: Payment Fraud Booms Back in 2023