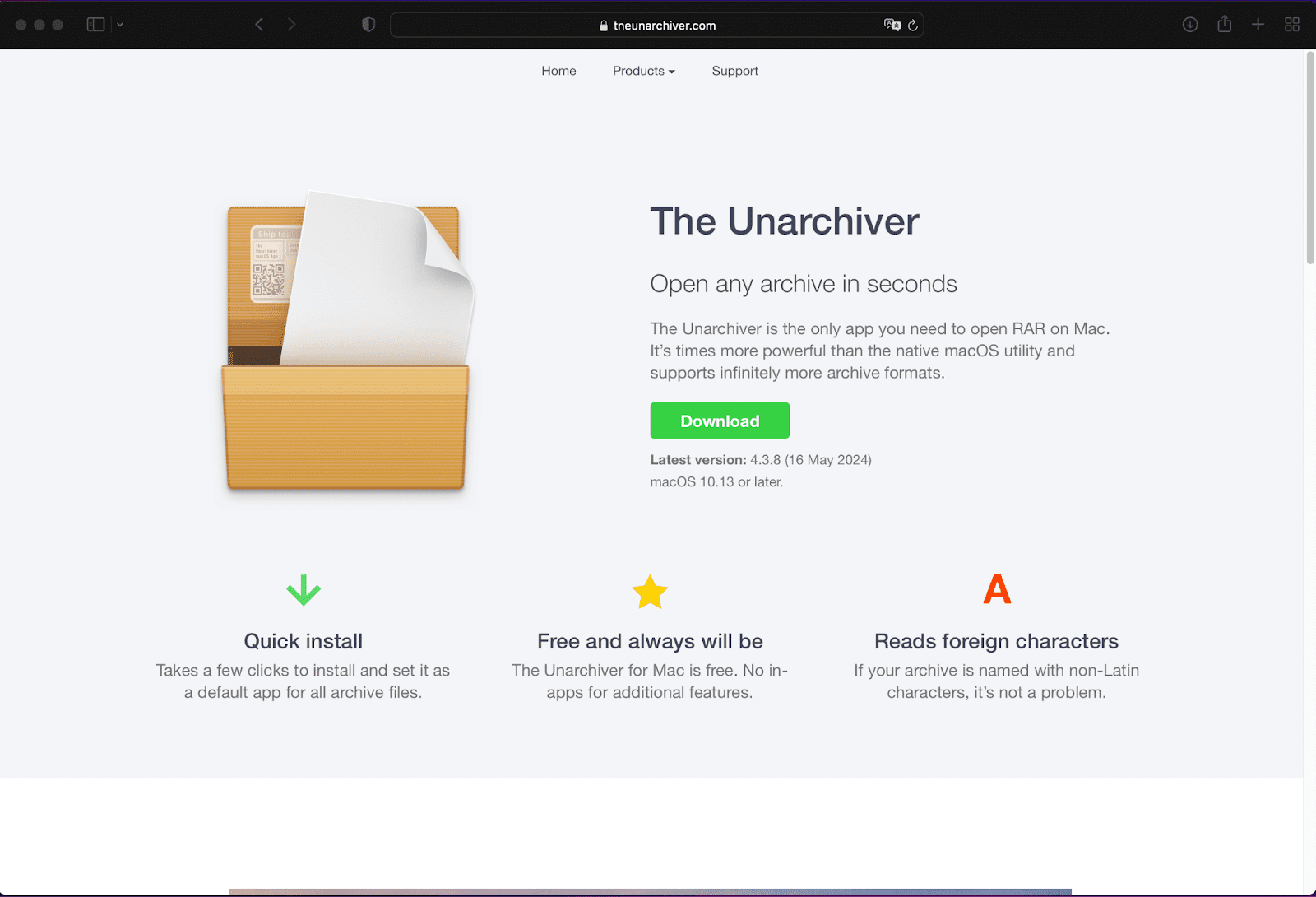
A spoofed website impersonating The Unarchiver app
Security researchers at Hunt.io have uncovered a sophisticated macOS malware campaign that masquerades as the popular file archiving tool “The Unarchiver.” This malicious imposter, named “CryptoTrade,” tricks users into downloading and installing what appears to be a legitimate app, only to steal sensitive data like passwords, documents, and even cryptocurrency wallet information.
The malware campaign utilizes a convincing phishing website that mimics the official The Unarchiver site, complete with a fake download button. Once downloaded, the malicious disk image, which goes undetected by most antivirus software, installs the CryptoTrade binary.
Operating within a controlled environment, Hunt.io researchers utilized the hdiutil command to mount the disk image safely. Preliminary checks using Patrick Wardle’s “WhatsYourSign” tool revealed that the disk image was not signed, an immediate red flag.
Exploring the mounted file system, researchers identified key directories and files such as the “Contents” folder, the “_CodeSignature” directory, the “MacOS” folder containing the executable binary, and the “Info.plist” configuration file. Notably, the executable binary was named “CryptoTrade,” which deviated from the expected naming convention for The Unarchiver software.
The CryptoTrade file, despite its suspicious naming, was not flagged as malicious by VirusTotal. Further analysis using the WhatsYourSign tool indicated that the file employed an ad-hoc signature. The universal binary, capable of running on both Intel and ARM architectures, was compiled on macOS 14.5 (May 13, 2024), as evidenced by the “BuildMachineOSBuild” key in the Info.plist file.
A detailed examination of the binary using the otool command revealed multiple references to the Swift programming language, confirming that CryptoTrade was written in Swift. This led to the discovery of shared libraries and a text file, indicating that the binary included code potentially used for capturing user passwords.
The malware’s reach extends far beyond simple file extraction. It’s been engineered to extract passwords from the keychain, plunder browsing history and cookies from web browsers, siphon documents from various locations, and even abscond with valuable cryptocurrency wallet data.
Adding to the concern, analysis of the malware’s code has revealed comments written in Russian, raising suspicions of a potential connection to cybercriminal groups operating in Russian-speaking regions.
Related Posts:
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System
- Facebook emphasized the surge in malware masquerading as ChatGPT
- ‘Trojanized’ npm Package Targets Cryptocurrency Wallets, Steals USDT
- APT29’s Espionage Campaign Exploits WinRAR Flaw, Targets Embassies
- Sneaky Android Adware Masquerades as Popular Games to Bombard You With Ads