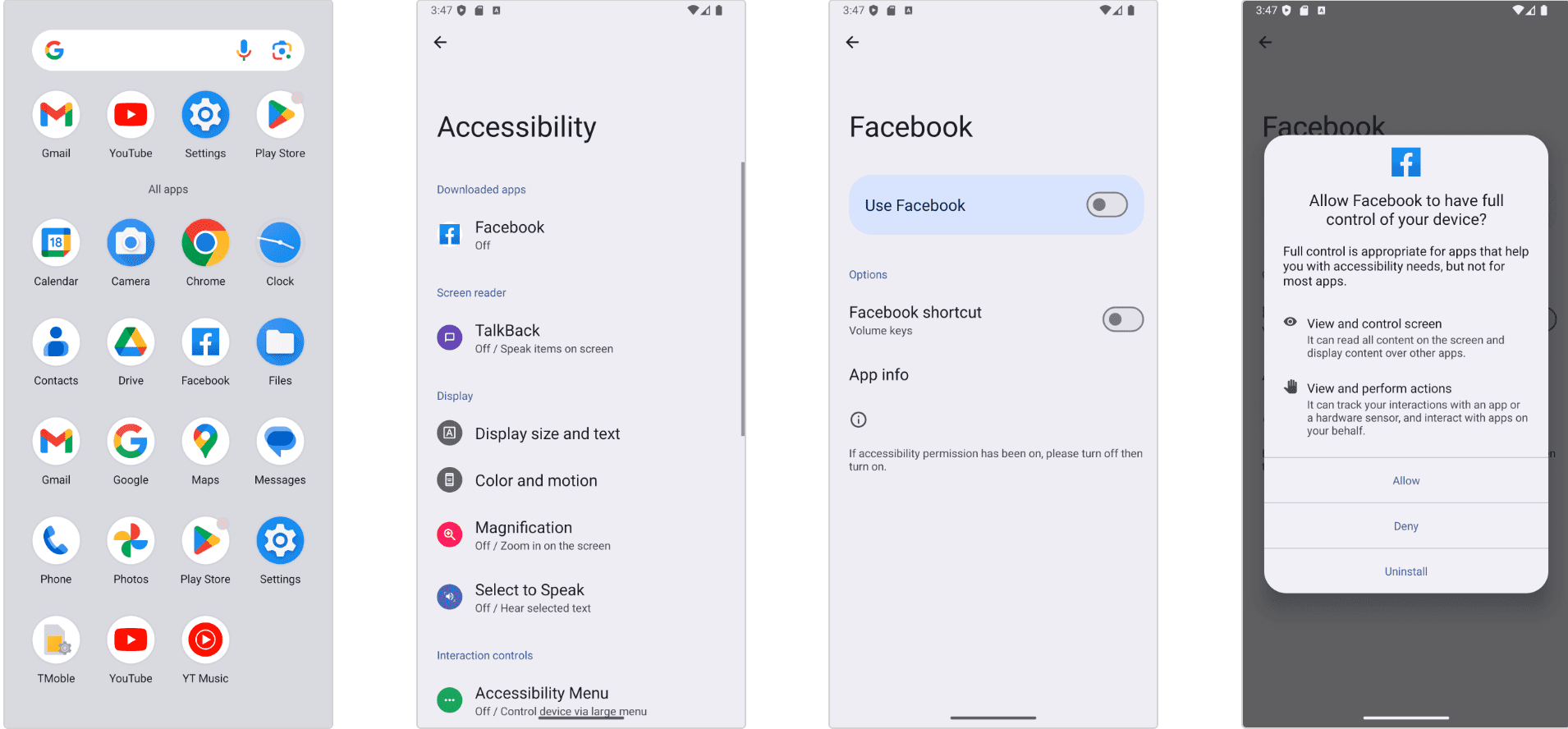
Screenshots showing how a HookBot-infected app establishes control of the victim’s device
Netcraft’s latest research details HookBot, a sophisticated Android-based banking Trojan that’s steadily advancing its footprint in the cybercrime world. First identified in 2023, HookBot has rapidly evolved, targeting Android users globally with overlay attacks, keylogging, and SMS interception to steal sensitive information such as banking credentials, passwords, and two-factor authentication (2FA) codes.
The journey of HookBot begins when a victim installs a malicious app, often downloaded from unofficial sources but sometimes able to bypass Google Play’s security checks. Once installed, the app establishes a connection to a command-and-control (C2) server, enabling it to receive updates and commands. Netcraft explains, “The malware then proceeds to extract user data using various attack techniques, such as apps overlays and surveillance techniques,” allowing it to monitor interactions and capture data with stealth.
One of HookBot’s most effective tactics is the overlay attack. By stacking malicious content on top of legitimate app screens, the malware can trick users into entering sensitive information on what appears to be a trusted interface. Netcraft observed multiple examples, including overlays mimicking popular brands such as Facebook, PayPal, and even specific banks like Bank of Queensland. “In some cases, the overlay screens are convincing, using brand logos and assets and mimicking the legitimate app interface,” the report notes.
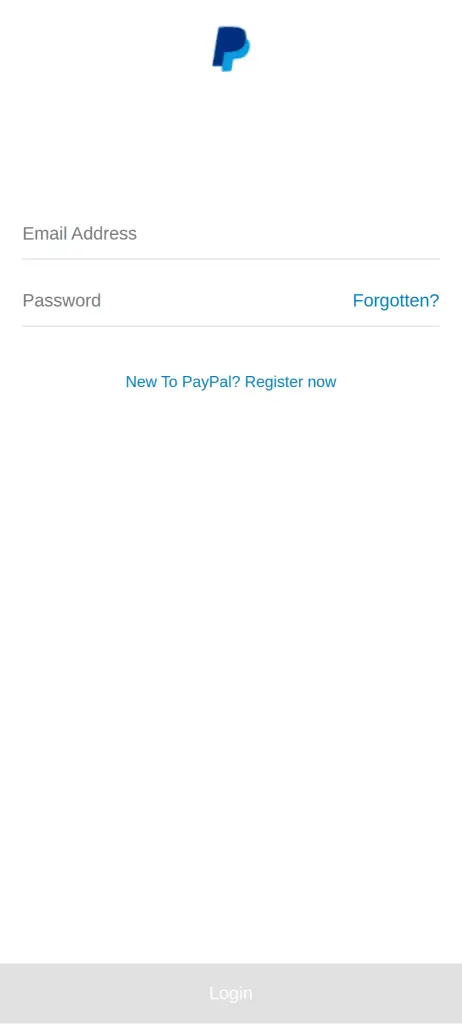
HookBot goes beyond overlays, employing additional features to capture data stealthily. These include keystroke logging, screen capture, and intercepting SMS messages, particularly those containing 2FA codes. The malware can even manipulate the device’s accessibility permissions to automate malicious tasks, such as sending WhatsApp messages, allowing it to spread like a worm from one device to another.
Netcraft’s analysis also uncovered the commercial ecosystem behind HookBot. Distributed through Telegram, HookBot is sold in various price models, catering to different budget levels for cybercriminals. Netcraft highlighted that “Telegram accounts and channels being used to distribute the trojan, offering would-be buyers different purchase options to suit their budget and the scale of their campaigns.”
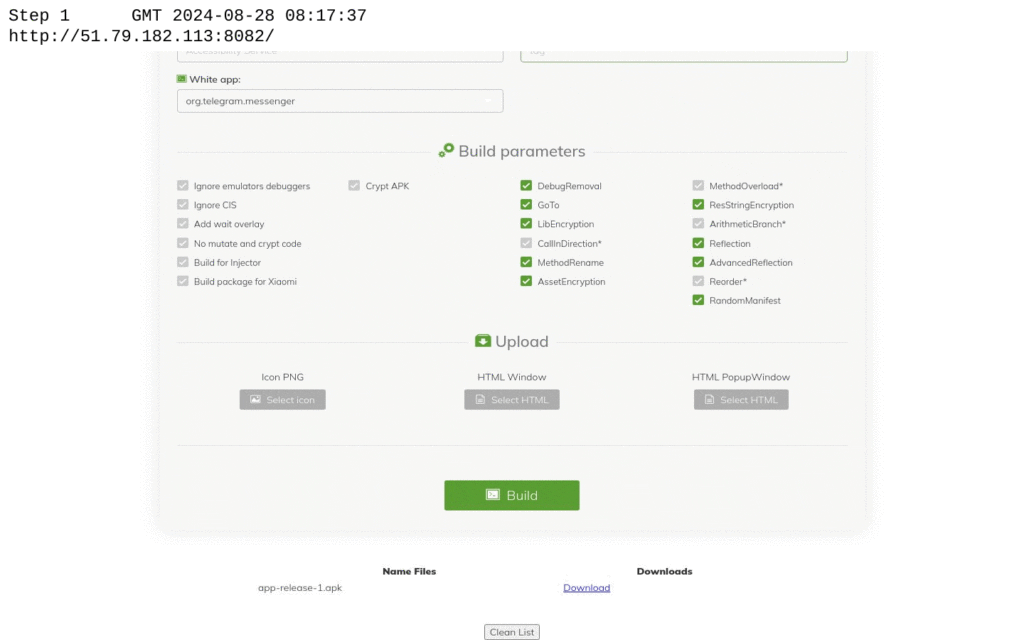
A significant enabler of HookBot’s reach is its builder tool, a user-friendly interface allowing even low-skill threat actors to create new malware samples. The builder provides options to obfuscate malicious behaviors, making detection challenging. Netcraft observed that HookBot’s code uses the Obfuscapk tool, which helps to avoid detection by creating unique app appearances for each instance. “By implementing a combination of these obfuscator tools, the malware developer/distributor can provide their apps with a unique appearance,” the report stated.
Despite increased awareness and disruption efforts, HookBot’s adaptability and accessibility ensure its continued spread. Netcraft’s conclusion is sobering: “There’s an appetite among threat actors for HookBot’s capabilities and the outcomes it can achieve,” and with a supply chain accessible to low-skill actors, the spread of HookBot is likely to accelerate.