bitcracker: open source password cracking tool for memory units encrypted with BitLocker
BitCracker
BitCracker is the first open source password cracking tool for memory units (Hard Disk, USB Pendrive, SD card, etc…) encrypted with BitLocker, an encryption feature available on Windows Vista, 7, 8.1 and 10 (Ultimate, Pro, Enterprise editions). BitCracker is a mono-GPU algorithm (implemented in CUDA and OpenCL ) which performs a dictionary attack against memory units encrypted with BitLocker. For all the authentication (encryption) methods offered by BitLocker (i.e. User Password, Smart Card, TPM, TPM+PIN, etc..) you can always use the BitCracker Recovery Password attack (-r option). As an additional feature, if your device has been encrypted with a User Password (BitLocker-To-Go feature) you can use the BitCracker User Password attack (-u option).
User Password Attack
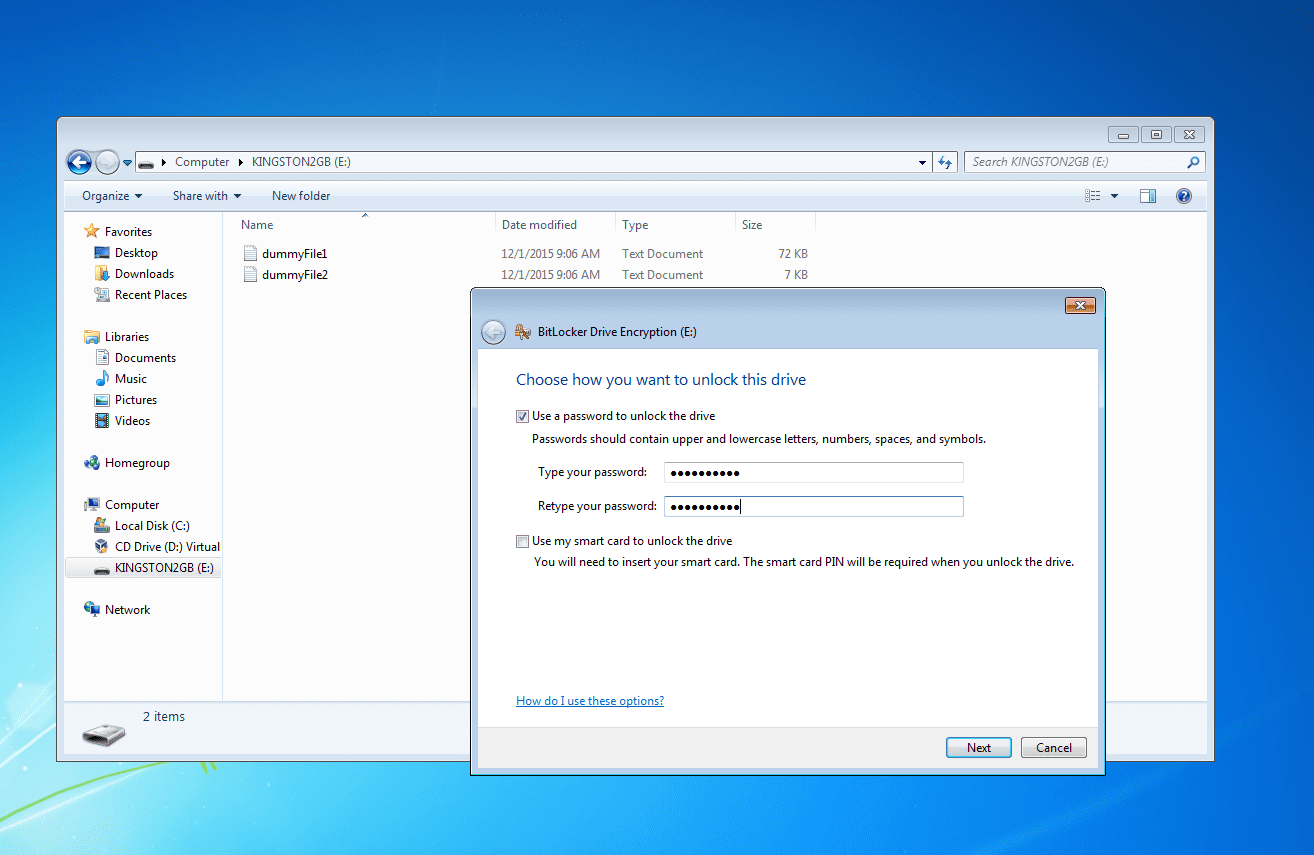
With this authentication method, the user can choose to encrypt a memory device by means of a password.
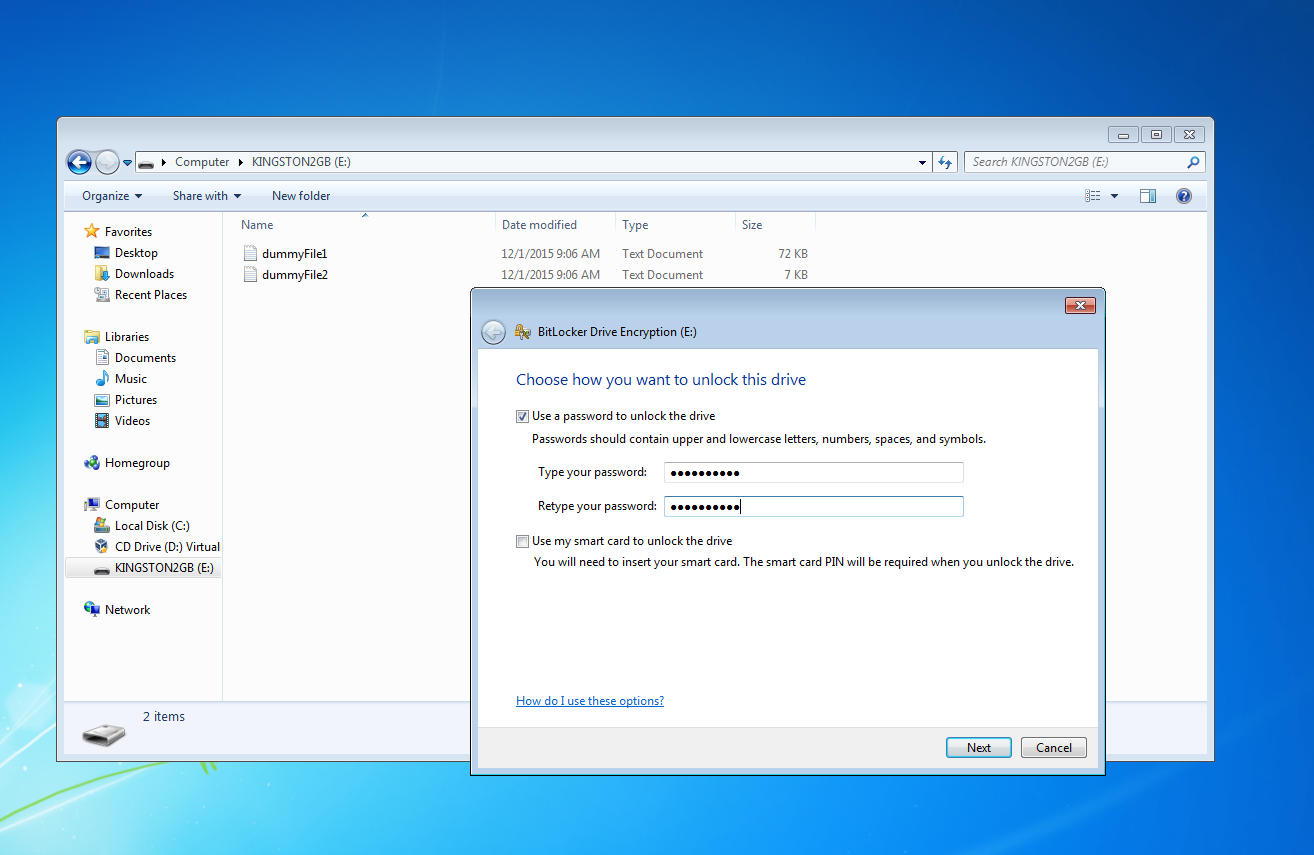
To find the password used during the encryption with BitCracker, you need to specify the -u option (see the How To section).
Recovery Password Attack
During the encryption of a memory device, (regardless the authentication method) BitLocker asks the user to store somewhere a Recovery Password that can be used to restore the access to the encrypted memory unit in the event that she/he can’t unlock the drive normally. Thus the Recovery Password is a kind of passe-partout for all the authentication methods and it consists of a 48-digit key like this:
236808-089419-192665-495704-618299-073414-538373-542366
To find the correct Recovery Password with BitCracker, you need to specify the -r option (see How To section). See Microsoft docs for further details.
Download
git clone https://github.com/e-ago/bitcracker.git
Usage
Use the build.sh script to build 3 executables:
- bitcracker_hash
- bitcracker_cuda
- bitcracker_opencl
Copyright (C) 2017 e-ago
Source: https://github.com/e-ago/





