The notorious Black Basta ransomware group is back, employing sophisticated social engineering tactics and deploying advanced malware payloads in their latest campaign. According to a detailed analysis by Rapid7, the threat actors have refined their techniques, introducing novel methods for gaining access and delivering malware, including Zbot, DarkGate, and custom-developed tools.
Rapid7 first reported this social engineering campaign in May 2024, with updates in August documenting the use of Microsoft Teams for initial contact. The latest resurgence, observed in October, showcases further refinements. As noted in the report, “The procedures followed by the threat actors in the early stages of the social engineering attacks have been refined again, with new malware payloads, improved delivery, and increased defense evasion”.
The campaign begins with an email bombing of targeted users, signing them up for multiple mailing lists to overwhelm their inboxes. Operators then reach out through Microsoft Teams, impersonating IT support staff. Display names like “Help Desk” and “Technical Support” are used to lend legitimacy to their approach. Once a victim engages, the attackers push for the installation of remote management tools such as QuickAssist, AnyDesk, or TeamViewer.
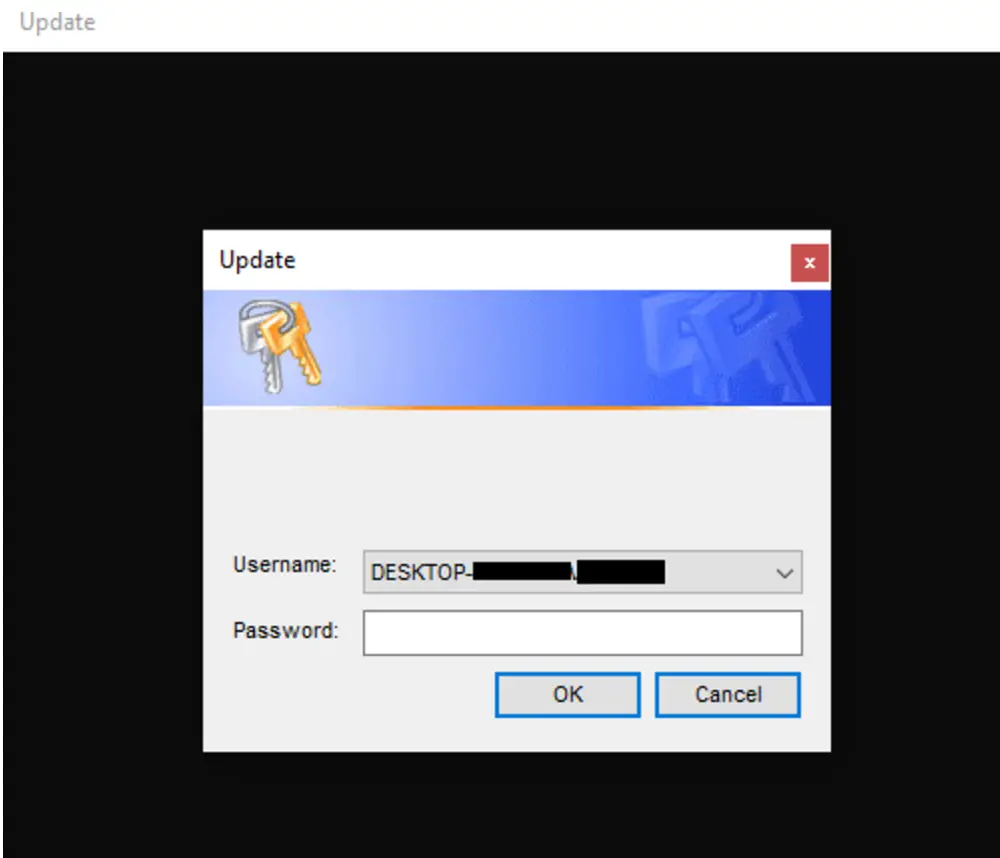
Upon gaining access, the operators deploy a suite of malware, starting with a custom credential harvester. This tool, updated from earlier iterations, collects system information and prompts users to enter their credentials, which are then saved to a file for later exploitation. As the report highlights, “The credential harvester is most commonly followed by the execution of a loader such as Zbot (a.k.a. Zloader) or DarkGate”.
- Zbot (Zloader): This malware establishes persistence through Windows registry modifications and uses sophisticated encryption to evade detection. It employs techniques like process hollowing to inject itself into legitimate processes such as
msedge.exe - DarkGate: Packed with a custom toolset, this malware is capable of keystroke logging, clipboard monitoring, and stealing credentials from applications like FileZilla. It also uses unique mutex-based persistence techniques and executes remote commands to maintain control
Operators use a variety of methods to deliver their malware, including compromised SharePoint instances, file-sharing websites, and even direct uploads via remote management tools. Notably, Rapid7 observed the use of stolen code-signing certificates to add a veneer of legitimacy to the payloads.
The attackers have also improved their evasion techniques. For example, they pack their malware with custom-built packers and employ obfuscation methods. A publicly available YARA rule helps detect the use of these packers, but the ongoing rapid iteration of payloads highlights the attackers’ commitment to staying ahead of detection measures.
Rapid7 warns, “Intrusions related to the campaign should be taken seriously — the intent goes beyond typical phishing activity.”
Related Posts:
- From Invoice to Infection: Darkgate’s Phishing Campaign Exposed
- New DarkGate Malware Campaign Exploits 0-day CVE-2024-21412 Flaw
- DarkGate Malware Resurfaces with New Campaign Tactics
- DarkGate and PikaBot: New Malware Threats Emerge from Advanced Phishing Campaign
- DarkGate Malware Makes a Comeback, Exploiting Excel and Samba Shares in Sophisticated Cyberattacks