Source: XLab
The threat actors behind a series of distributed denial-of-service (DDoS) attacks targeting the distribution platforms of the Chinese game Black Myth: Wukong are back with a new and improved botnet.
In August 2024, a massive DDoS attack campaign disrupted Steam and Perfect World, the platforms responsible for distributing the highly anticipated game Black Myth: Wukong. The attacks, launched by a botnet calling itself AISURU, targeted hundreds of servers across 13 global regions.
Now, researchers at XLab have discovered that the threat actors behind AISURU have reemerged with a new botnet dubbed AIRASHI. This updated botnet boasts enhanced capabilities and a more sophisticated infrastructure designed to evade detection and takedown efforts.
AIRASHI demonstrates the relentless evolution of botnet capabilities. Utilizing a 0-day vulnerability in cnPilot routers, AIRASHI spreads its samples with efficiency. The vulnerabilities exploited by AIRASHI are as follows:
| VULNERABILITY |
|---|
| AMTK Camera cmd.cgi Remote Code Execution |
| Google Android ADB Debug Server – Remote Payload Execution |
| AVTECH IP Camera / NVR / DVR Devices |
| cve_2013_3307 |
| cve_2016_20016 |
| cve_2017_5259 |
| cve_2018_14558 |
| cve_2020_25499 |
| cve_2020_8515 |
| cve_2022_40005 |
| cve_2022_44149 |
| cve_2023_28771 |
| Gargoyle Route run_commands.sh Remote Code Execution |
| LILIN Digital Video Recorder Multiple Remote Code Execution |
| CVE-2022-3573 |
| cnPilot 0DAY |
| OptiLink ONT1GEW GPON 2.1.11_X101 |
| Shenzhen TVT Digital Technology Co. Ltd & OEM {DVR/NVR/IPC} API RCE |
The botnet employs sophisticated encryption protocols, including RC4 and ChaCha20, combined with HMAC-SHA256 for message integrity verification. Notably, XLab’s report highlighted the botnet’s use of nearly 60 Command and Control (C2) IPs distributed across 19 countries, complicating takedown efforts.
One detail from the report reveals AIRASHI’s mocking tone toward security researchers. CNC domain names like “xlabsecurity” and embedded strings such as “Come on, shake your body XLab, do the conga” demonstrate an unusual interaction with those attempting to dismantle it.
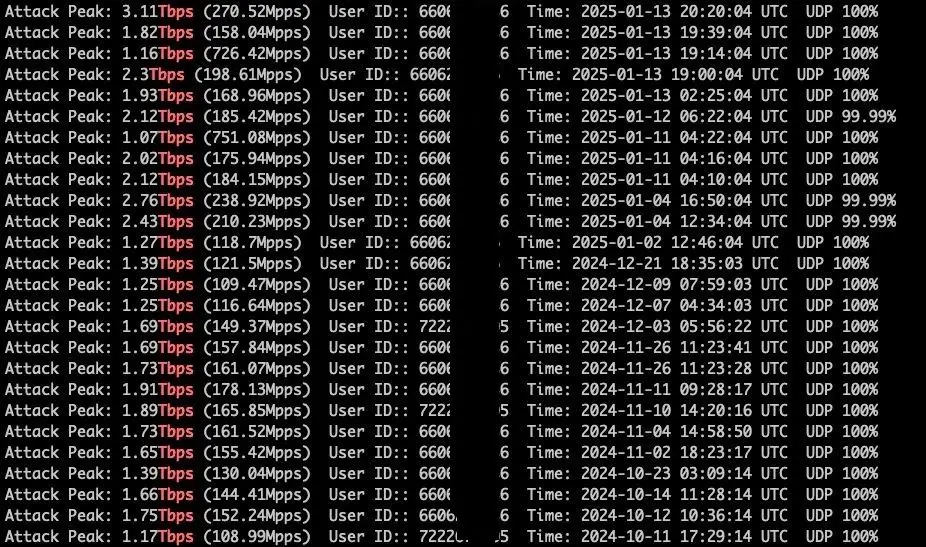
The AIRASHI botnet maintains a consistent attack capacity ranging from 1 to 3 Tbps, as validated through demonstrations shared on Telegram. The report underscores the botnet’s ability to execute “stable T-level DDoS attack capabilities,” targeting hundreds of global servers daily. Primary targets include sectors in China, the United States, Poland, and Russia, showcasing its broad, indiscriminate impact.
The AIRASHI botnet has been in constant development. From the streamlined AISURU variant known as “Kitty” to AIRASHI-DDoS and AIRASHI-Proxy, each iteration incorporates new functionalities. The introduction of proxy tools and reverse shell capabilities signals an intent to expand beyond traditional DDoS operations.
XLab researchers emphasize the sophistication of AIRASHI’s network protocols, noting that its communication process involves, Key negotiation, HMAC verification, and encrypted message exchanges via ChaCha20.
While AIRASHI remains an active threat, XLab has taken steps to equip defenders with tools to combat its spread. The report includes Snort rules to detect exploitation attempts, although details of the 0-day vulnerability remain undisclosed to prevent further abuse.
For a closer look at the report and detailed technical breakdowns, visit XLab’s blog.
Related Posts:
- “Gayfemboy” Botnet Leveraging 0-Day Exploit in Four-Faith Industrial Routers
- Kiteshield Packer Emerges as a Significant Threat in Linux Malware Landscape
- New Melofee Backdoor Variant Targets Linux Systems with Advanced Stealth Tactics
- The Zero-Detection PHP Backdoor Glutton Exposed
- Attacker use DDoS attack to hit three major Dutch banks
