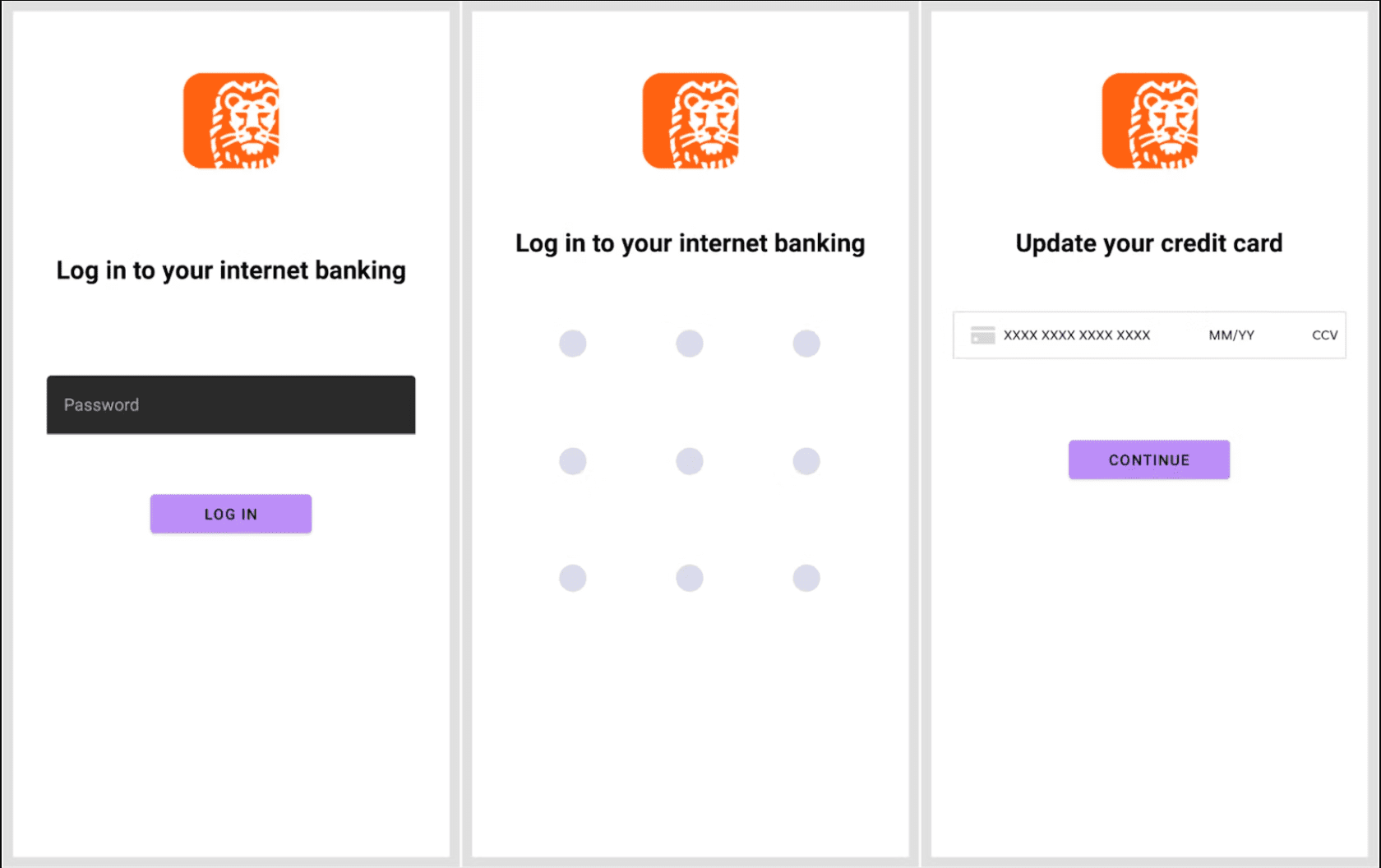
The image depicts a screenshot of customized overlays that our Malware Intelligence Team generated | Image: Intel 471
A new Android banking trojan dubbed “BlankBot” has emerged, posing a significant threat to mobile users. Discovered by Intel 471 Malware Intelligence researchers on July 24, 2024, this sophisticated malware includes screen recording, keylogging, and remote control capabilities.
BlankBot, primarily targeting Turkish users but potentially adaptable for global campaigns, operates by impersonating utility applications and bypassing security measures to gain complete control of infected devices. The malware exploits accessibility services to log sensitive information, including SMS messages, bank credentials, and payment card data.
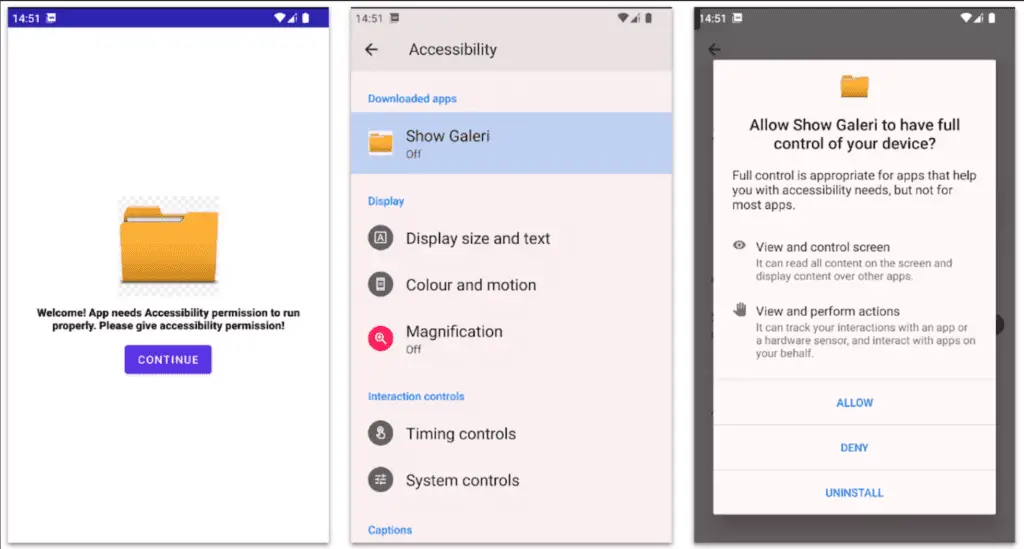
Upon installation, the malicious app conceals its icon and prompts users to grant accessibility permissions. It deceives users with a black screen, indicating an update, while automatically securing all necessary permissions in the background. For devices running Android 13 or newer, BlankBot employs a session-based package installer to bypass security features, retrieving and installing APK files from the application’s assets directory.
BlankBot’s communication begins with a “GET” request where HTTP headers convey information about the infected device, such as battery level, screen size, model, manufacturer, and OS version. Subsequent communications occur via a WebSocket connection on port 8080.
Key Capabilities of BlankBot
- Screen Recording: Utilizing Android’s MediaProjection and MediaRecorder APIs, BlankBot captures and saves screen activity as MP4 files. Though this feature appears to be in development, it can also capture and transmit screen images encoded in Base64 format.
- Keylogging: By exploiting accessibility services, BlankBot intercepts and steals confidential information, including text, notifications, and user inputs. Uniquely, it uses a custom virtual keyboard via the InputMethodService class to log key presses.
- Custom Injections: The malware can create customizable overlays to solicit banking credentials, personal information, and payment card data. External libraries like CompactCreditInput and Pattern Locker View are utilized to implement these injection templates.
BlankBot communicates with its command-and-control (C2) server via WebSocket to exfiltrate data and receive commands. It can start and stop screen recording, bypass FLAG_SECURE security measures using a hidden virtual network (HVNC) module, and perform on-device fraud (ODF) through remote control gestures. Additionally, BlankBot can create overlays, collect contacts, SMS messages, and a list of installed applications.
To evade detection, BlankBot verifies if the infected device is legitimate, maintaining persistence by preventing access to settings or antivirus applications through accessibility services. Recent samples exhibit partial obfuscation and junk code to hinder reverse-engineering efforts, complicating analysis for security researchers.
Cybersecurity experts urge Android users to exercise caution when downloading applications and to keep their devices updated with the latest security patches.