Bleak
A Windows native DLL injection library that supports several methods of injection.
Injection Methods
- CreateThread
- HijackThread
- ManualMap
Optional Extensions
- EjectDll
- HideDllFromPeb
- RandomiseDllHeaders
- RandomiseDllName
Features
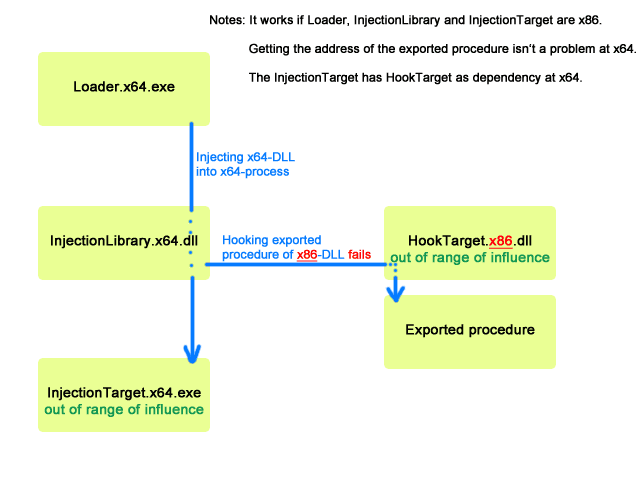
- WOW64 and x64 injection
Caveats
- Attempting to inject into a system-level process will require your program to be run in Administrator mode.
- Injecting a byte array (that represents a DLL) will result in a temporary DLL being written to disk in
%temp%, unless the method of injection is ManualMap, in which case nothing will be written to disk. - Injecting with the HideDllFromPeb flag will currently result in your DLL not being able to be ejected.
- ManualMap injection supports the initialization of exception handling, however, this is limited to structured exception handling. Vectored exception handlers are not set up in the remote process during injection and any exceptions being handled using this type of exception handling will not be caught.
- ManualMap injection relies on a PDB being present for ntdll.dll and, so, the first time this method is used, a PDB for ntdll.dll will be downloaded and cached in
%temp%. Note that anytime your system performs an update, a new version of this PDB may need to be downloaded and re-cached. This process may take a few seconds depending on your connection speed.
Download && Use
Copyright (c) 2018 Joshua de Wet