
The Insikt Group has uncovered a sophisticated cyber-espionage operation conducted by BlueAlpha, a state-sponsored threat actor with links to the Russian Federal Security Service (FSB). The campaign targets Ukrainian entities using a combination of HTML smuggling and Cloudflare’s tunneling service to stage and deploy GammaDrop malware.
A key finding in the report is BlueAlpha’s use of Cloudflare Tunnels to conceal GammaDrop staging infrastructure. According to Insikt Group, “Cloudflare Tunnels have been gaining momentum as a defense evasion technique due to their ease of setup and the fact that they have no cost to the user in most cases.” By using these tunnels, BlueAlpha successfully obfuscates their activities, complicating detection and mitigation efforts by traditional security systems.
BlueAlpha relies on spearphishing campaigns to deliver malware to their targets. Their method includes HTML smuggling, where attachments deliver Visual Basic Script (VBScript)-based malware through encoded JavaScript. The smuggled payloads lead to GammaDrop and GammaLoad infections.
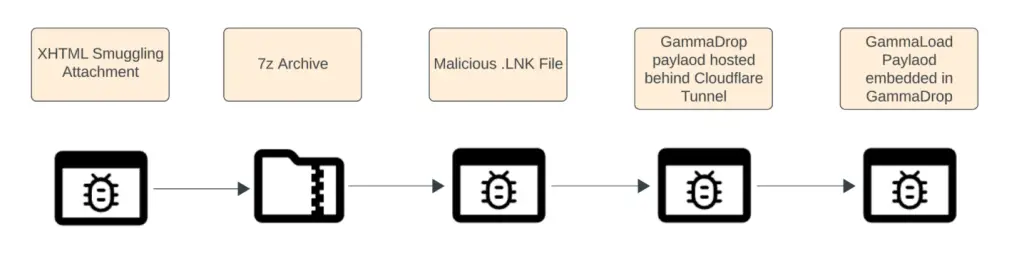
Insikt Group detailed this approach, noting that “the JavaScript embedded within the XHTML attachment will first check that the operating system of the platform opening the file is Windows. If successful, it will decode the archive smuggled in the XHTML attachment and download it.”
- GammaDrop: Used to stage and persist GammaLoad payloads, GammaDrop hides malicious activities by executing embedded scripts and manipulating the system environment. The report states, “GammaDrop samples have been obfuscated with extensive amounts of junk code, random variable names, and string concatenation and encoding.”
- GammaLoad: A custom backdoor, GammaLoad communicates with command-and-control (C2) servers via plain-text HTTP, enabling the deployment of additional malware in the Gamma family. Notably, BlueAlpha employs DNS over HTTPS (DoH) to resolve C2 domains, enhancing the malware’s resilience to DNS-based blocking.
To further obscure their activities, BlueAlpha uses DNS fast-fluxing for their GammaLoad C2 infrastructure. This tactic complicates tracking by rapidly changing IP addresses associated with a single domain. Insikt Group observed that “GammaLoad makes use of DoH providers such as Google and Cloudflare to resolve C2 infrastructure when traditional DNS fails.”
Organizations are urged to adopt several countermeasures to combat threats from actors like BlueAlpha:
- Secure Email Gateways: Configure gateways to inspect and block HTML smuggling attempts, particularly those containing JavaScript with suspicious
onerrororonmousemoveevents. - Restrict Execution of mshta.exe: Implement endpoint controls to block the execution of untrusted
.lnkfiles and monitor mshta.exe activity for unusual downloads. - Monitor Cloudflare Subdomains: Flag traffic to TryCloudflare subdomains, which are increasingly abused for malicious purposes.
- DNS and DoH Logging: Enable traffic logging and review connections to detect unauthorized DoH usage.
The use of legitimate services like Cloudflare by state-sponsored threat actors underscores the importance of robust detection and prevention measures. As BlueAlpha continues to refine its techniques, organizations must stay informed of evolving threats. The Insikt Group’s report emphasizes, “Preparedness against these tactics will be crucial for Ukrainian organizations as BlueAlpha’s campaign persists.”
For more detailed insights and indicators of compromise (IoCs), visit Insikt Group’s official report.
Related Posts:
- Threat Actors Exploit GitHub to Spread Malware, Targeting Multiple Operating Systems
- Mozilla is testing DNS over HTTPs in Firefox (DoH)
- Cloudflare to push the new public DNS service, 1.1.1.1