BlueMap: An Interactive Exploitation Toolkit for Azure

BlueMap
The BlueMap is an interactive tool for identifying IAM misconfigurations, information gathering, abuse of managed identities, detection of user permissions, and much more. All are in interactive mode without ANY third-party dependencies (such as AzModule or Azure Powershell), so the tool leaves a minimum footprint on your customer’s network.
BlueMap helps penetration testers and red teamers to perform Azure auditing, discovery & enumeration, and exploitation in interactive mode that saves complex opsec and overhead that usually exists in Azure penetration testing engagements.
Features
- Automatic generation tokens via Az Module (only if installed on the target machine) and token parser
- Support automatic exploitation for Reading Vaults Secrets, Misconfigured Service Principal, Elevate Access, and utilities to support attack paths for Reader/Global Reader, Contributor, and Global Admin.
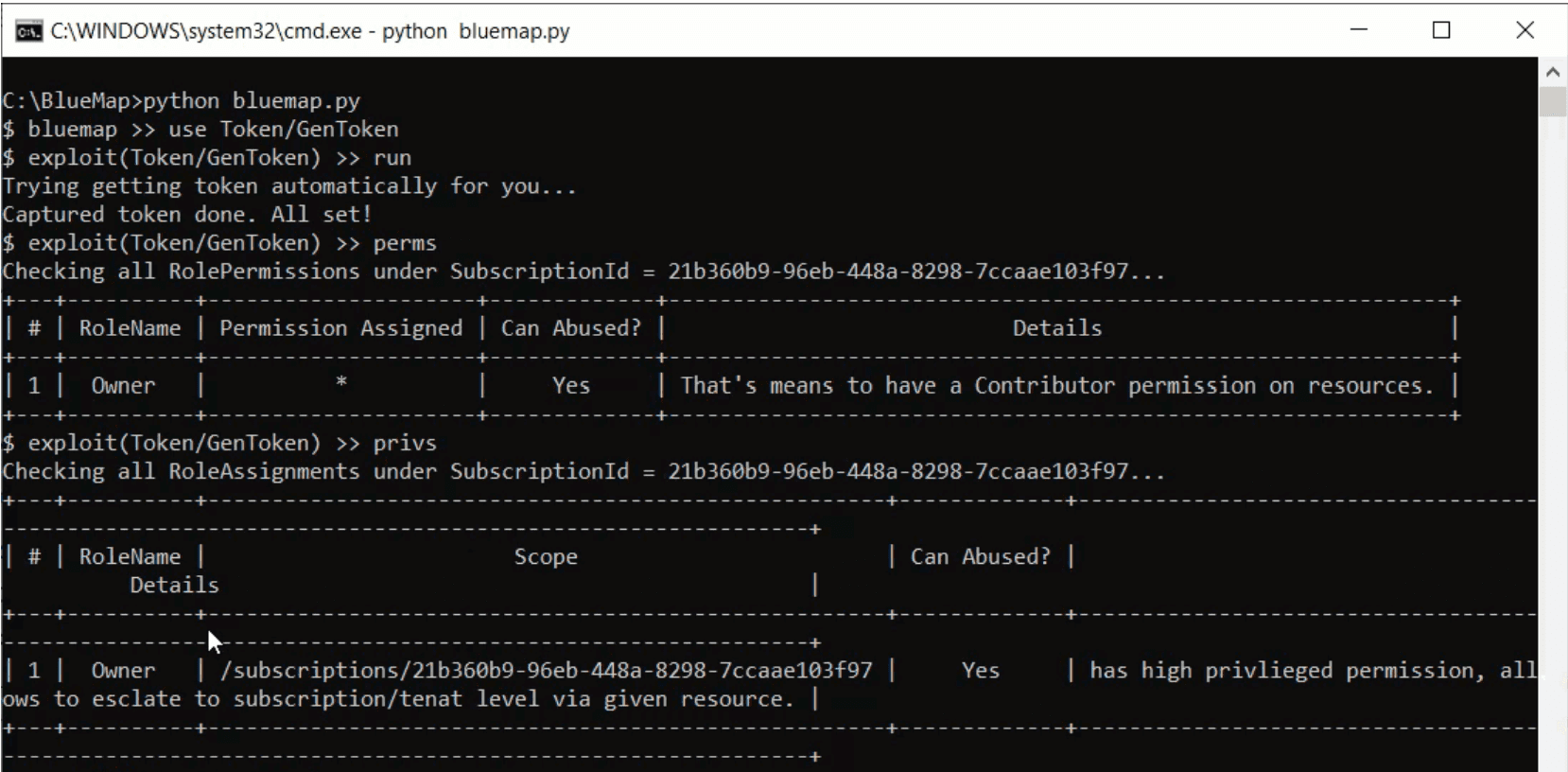
- Built-in interactive mode for most of the exploits (aka “models” or “techniques”)
- Integrated Permissions and Privileges analysis aims the detection of shadow admins and shadow permissions during the engagement
- Minimal footprint on the network as there are no third-party dependencies of PowerShell modules (except the Automatic generation tokens feature)
- Support data gathering capabilities in different modules via Runbook, App Service Deployments, ARM templates, Users, and more.
BlueMap uses two diffrent interfaces:
- Non-Interactive
- Interactive Mode
The Non-Interactive mode is used for token manipulation and user context evaluation (i.e. whoami commands), and it also refers to the auto-exploit method. Therefore no user interaction is required, and the exploitation is done behind the scenes. However, the interactive way is mainly for running different exploits. In contrast, some exploits execute automatically, while others may ask for future details about the target (i.e. which resource the exploit should run?).
List of the available exploits:
| TYPE | Level | EXPLOIT | MODE |
|---|---|---|---|
| Information Gathering | Reader,Global Reader | Reader/ListAllUsers | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ExposedAppServiceApps | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListAllAzureContainerRegistry | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListAutomationAccounts | Non-Interactive |
| Discovery | Reader,Global Reader | Reader/DumpAllRunBooks | Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListAllRunBooks | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListAllVaults | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListAppServiceSites | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListVirtualMachines | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListAllStorageAccounts | Non-Interactive |
| Discovery | Reader,Global Reader | Reader/ARMTemplatesDisclosure | Non-Interactive |
| Information Gathering | Reader,Global Reader | Reader/ListServicePrincipal | Non-Interactive |
| Discovery | Reader,Global Reader | Reader/abuseServicePrincipals | Interactive |
| Information Gathering | Contributor | Contributor/ListACRCredentials | Non-Interactive |
| Discovery | Contributor | Contributor/ReadVaultSecret | Interactive |
| RCE | Contributor | Contributor/RunCommandVM | Interactive |
| Lateral Movement | Contributor | Contributor/VMExtensionResetPwd | Interactive |
| RCE | Contributor | Contributor/VMExtensionExecution | Interactive |
| Information Gathering | Contributor | Contributor/VMDiskExport | Interactive |
| Discovery | Contributor | Contributor/DumpWebAppPublishProfile | Non-Interactive |
| Lateral Movement | GlobalAdministrator | GlobalAdministrator/elevateAccess | Interactive |
Intrusive Actions
While most BlueMap has no third-party dependencies, some exploits might be noisy in the network as they perform actions such as opening/reading/modifying local files. Also, the auto-generation token method (Token/GenToken) uses an underlying Az Model, which may lead to flagging the tool.
List of the available intrusive commands:
| TYPE | Level | EXPLOIT | MODE |
|---|---|---|---|
| Discovery | Reader,Global Reader | Reader/DumpAllRunBooks | Interactive |
Install & Use
Copyright (c) 2022 Maor Tal