BlueTeam.Lab
This project contains a set of Terraform and Ansible scripts to create an orchestrated BlueTeam Lab. The goal of this project is to provide the red and blue teams with the ability to deploy an ad-hoc detection lab to test various attacks and forensic artifacts on the latest Windows environment and then to get a ‘SOC-like’ view into generated data.
NOTE: This lab is deliberately designed to be insecure. Please do not connect this system to any network you care about.
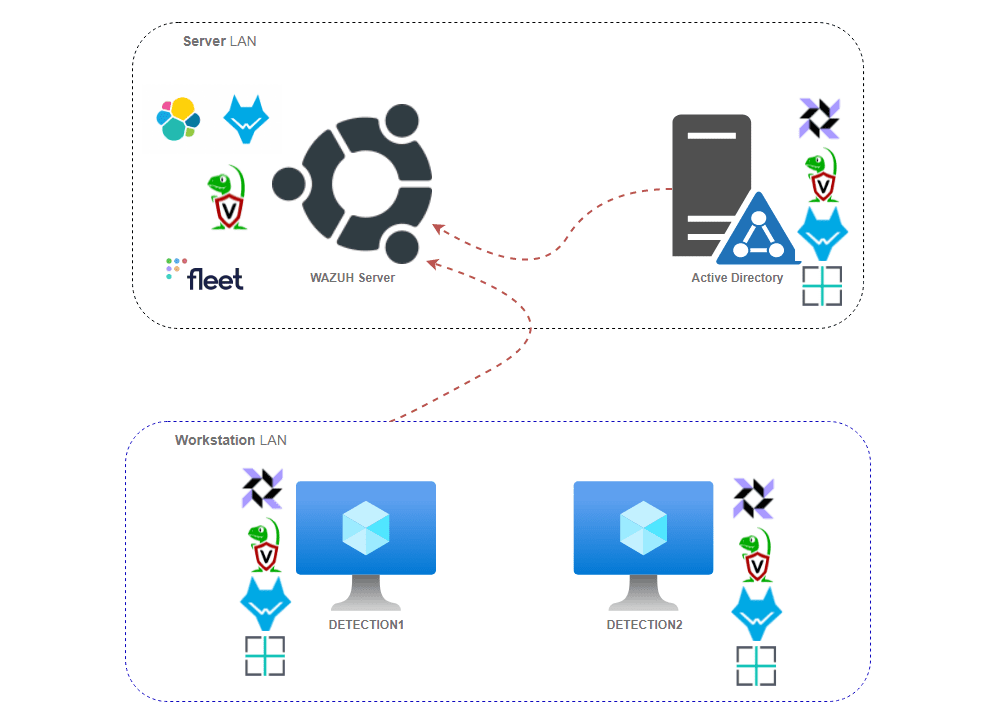
Lab Layout

Features
- Windows AD with two workstations connected to Windows domain in the default setup.
- Flexible domain configuration file allowing for easy changes to the underlying configuration.
- Auditing policies configured based on CIS Guide to increase event visibility across Windows infrastructure. Auditpol was used to configure additional settings and PowerShell Transcript Logs enabled.
- Sysmon64 deployed across infrastructure using the latest SwiftOnSecurity configuration for Windows devices.
- Wazuh Server configured and operational to collect logs from devices.
- Wazuh Agents configured across infrastructure and feeding data into the Wazuh server.
- Firewall configured to only allow your own IP to access the deployed systems.
- OSQuery and FleetDM were installed across the infrastructure, using configuration templates from Palantir.
- Velocidex Velociraptor Server configured and operational.
- Velocidex Velociraptor Agents configured across infrastructure and feeding data into the Velociraptor server.
- WinLogBeat configured to log data into Elastic instance.
- LokiToWinEventLog Loki Scanner configured to log data to Windows Event log every 3 hours and ship data to Elastic instance installed with Wazuh Server.
- Pe-SieveToWinEventLog Pe-Sieve Scanner configured to log data to Windows Event log every 3 hours and ship data to Elastic instance installed with Wazuh Server.
Install & Use
Copyright (C) 2022 op7ic