Image: Coinspect
A recent report by Coinspect has revealed critical vulnerabilities in popular browser wallets, raising significant concerns about the security of cryptocurrency holdings. The report warns that attackers could exploit these weaknesses to “drain your funds—no phishing, no social engineering, no approval required, you don’t even have to click ‘Connect Wallet’“.
Coinspect’s findings indicate that simply visiting a malicious website could be enough to silently expose a user’s recovery phrase, giving attackers the ability to steal funds at will. The attackers could even choose to wait until a wallet accumulates a substantial balance, making it harder for users to trace the breach.
The affected wallets include Stellar Freighter, Frontier Wallet, and Coin98. Coinspect expresses concern that other wallets may also be vulnerable, especially newer ones that “enter the ecosystem without relying on well-tested, open-source codebases“.
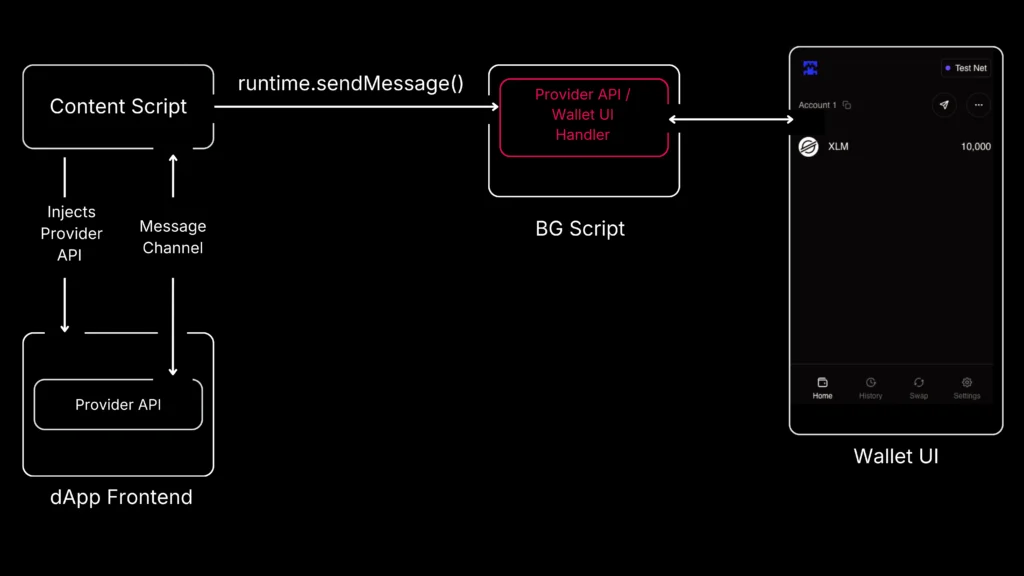
Modern browser wallets connect to decentralized applications (dApps) by injecting JavaScript code into webpages. This code facilitates a communication pipeline between the wallet and the dApp using a Provider API, message-passing via Content Scripts, and internal Background Scripts that hold the keys and process logic.
The system is supposed to be gated by user approval—but Coinspect’s findings show that attackers can exploit flaws in wallet message handling to bypass these protections entirely.
Freighter, Stellar’s official wallet, suffered from a severe architectural oversight. Due to a shared message handler, it could not distinguish between legitimate UI interactions and malicious messages from websites.
“An attacker site could send malicious messages mimicking legitimate requests… triggering the function intended to display the recovery phrase.”
This gave attackers direct access to the secret seed phrase, which they could extract without any visual feedback or wallet unlock. The vulnerability was reported via HackerOne and fixed in version 5.3.1 (CVE-2023-40580).
Frontier’s wallet had better separation of message ports, but its Provider API inadvertently exposed internal wallet state, including the encrypted secret recovery phrase.
“A malicious site could steal the secret recovery phrase even when the wallet was locked and without requiring any user approval.”
Though encrypted, the phrase could be brute-forced offline or weaponized in targeted phishing attacks. Worse still, the attacker also received the wallet’s address—allowing them to monitor it for value before launching the attack. The issue was patched on November 22, 2024.
Coin98’s vulnerability was especially dangerous. By injecting a specially crafted message (isDev:true) into the wallet’s content script, attackers could bypass user prompts entirely.
“Attackers could force the wallet to sign and broadcast transactions to the blockchain, draining funds to an address under their control.”
This turned malicious websites into full-fledged crypto drainers, no user interaction needed. The issue was reported via HackenProof and fixed in mid-2023.
These bugs highlight how design flaws—not phishing—can create massive security gaps in browser-based crypto wallets. Here’s what makes them uniquely dangerous:
- No interaction required: Users didn’t even need to click “Connect Wallet.”
- No phishing or malware needed: Merely visiting a website was enough.
- Attackers could delay exploitation: They could watch and wait for wallets to become valuable before draining funds.
- Crypto-drainer integration: These exploits are likely to be adopted into off-the-shelf drainer kits, posing risks to future wallet projects.
Coinspect warns that it is “only a matter of time before attackers begin integrating wallet exploits into drainer kits“.
Related Posts:
- Solana Drainer Source Code Leak Reveals MS Drainer Connection, Underscores Growing Threat to Crypto Users
- Fake WalletConnect App on Google Play Drains $70K in Crypto
- $20 Million Drained and Returned: Government Wallet Under Scrutiny
- NFC Nightmare: New NGate Trojan Drains Bank Accounts via ATMs