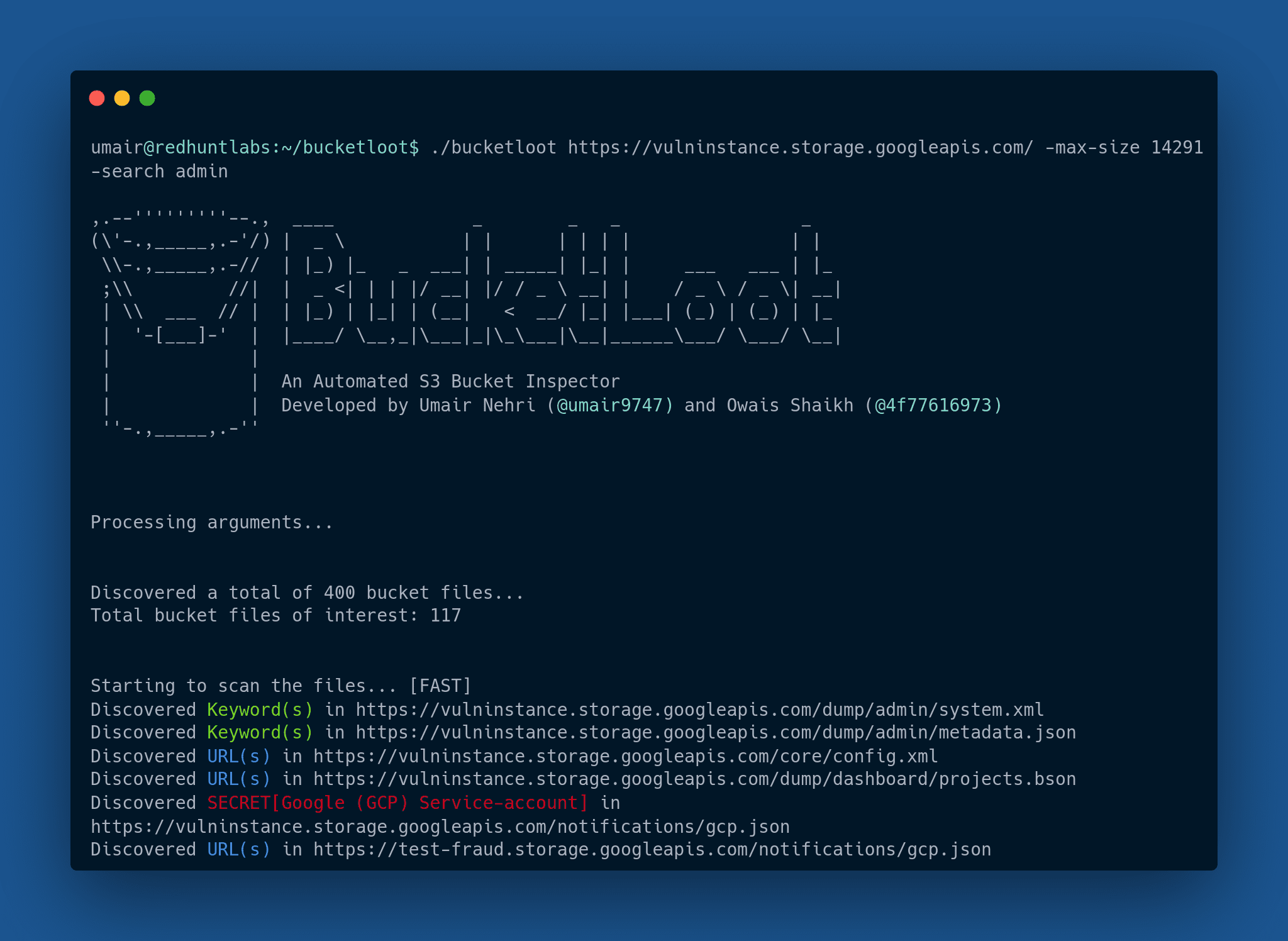
BucketLoot
BucketLoot is an automated S3-compatible Bucket inspector that can help users extract assets, flag secret exposures and even search for custom keywords as well as Regular Expressions from publicly-exposed storage buckets by scanning files that store data in plain text.
The tool can scan for buckets deployed on Amazon Web Services (AWS), Google Cloud Storage (GCS), DigitalOcean Spaces, and even custom domains/URLs which could be connected to these platforms. It returns the output in a JSON format, thus enabling users to parse it according to their liking or forward it to any other tool for further processing.
BucketLoot comes with a guest mode by default, which means a user doesn’t need to specify any API tokens / Access Keys initially in order to run the scan. The tool will scrape a maximum of 1000 files that are returned in the XML response and if the storage bucket contains more than 1000 entries which the user would like to run the scanner on, they can provide platform credentials to run a complete scan. If you’d like to know more about the tool, make sure to check out our blog.

Features
Secret Scanning
Scans for over 30+ unique RegEx signatures that can help in uncovering secret exposures from the misconfigured storage bucket. Users have the ability to modify or add their own signatures in the regexes.json file. If you believe you have any cool signatures which might be helpful for others too and could be flagged at scale, go ahead and make a PR!
Asset Extraction
Interested in stepping up your asset discovery game? BucketLoot extracts all the URLs/Subdomains and Domains that could be present in an exposed storage bucket, enabling you to have a chance of discovering hidden endpoints, thus giving you an edge over the other traditional recon tools.
Searching
The tool goes beyond just asset discovery and secret exposure scanning by letting users search for custom keywords and even Regular Expression queries which may help them find exactly what they are looking for.
Changelog v2.0
🐞 Bug fixes and performance improvements for running the scan at scale seamlessly
🔔 Webhook Notifications: Get notified whenever the tool discovers security exposures through webhooks on Discord and Slack using the -notify flag [Requires additional configuration, refer to the tool documentation for more details.]
🛠️ Dig mode: Want to quickly check for misconfigured object storage (bucket) instances in a bunch of non-s3 domains? Use -dig flag to quickly scrape the target domain’s response body, extract URLs and check them for misconfigured buckets.
🚨Sensitive File Checks: BucketLoot now by default also looks for sensitive file names and extensions thus increasing the scan capabilities and unlocking new attack surfaces.
⬆️ Improved Signatures: BucketLoot now supports 80+ unique and improved signatures for scanning secrets and 80+ signatures for sensitive file checks as well
Install & Use
Copyright (c) 2023 RedHunt Labs