BWASP
The BoB Web Application Security Project (BWASP) is an open-source, analysis tool to support for Web Vulnerability Manual Analysis hackers.
BWASP supports performing automated analysis and manual analysis.
The BWASP Project supports:
- Find Attack vector automatically. (e.g. SQL Injection, Cross-site Scripting)
- Detect website technology.
- Log4J vulnerability scan (Partially supports Java language)
- HTTP REST API
Install
git clone https://github.com/BWASP/BWASP.git
pip3 install -r requirements.txt
python3 start.py
Use
Automated analysis with Python
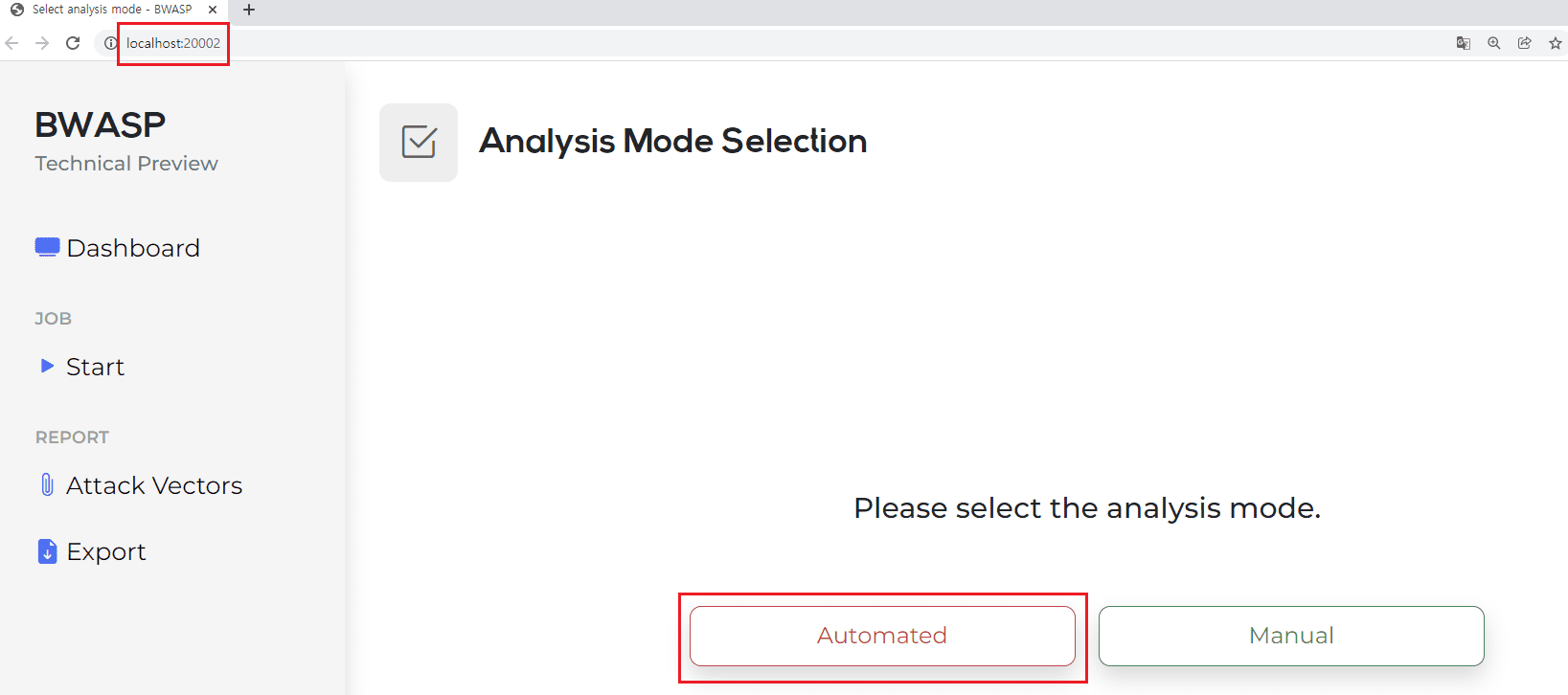
When accessing the URL (http://localhost:20002) for the first time as shown in Figure 1, you can see that there are two methods: Automated and Manual.
By clicking Automated, the automatic analysis function can be executed.
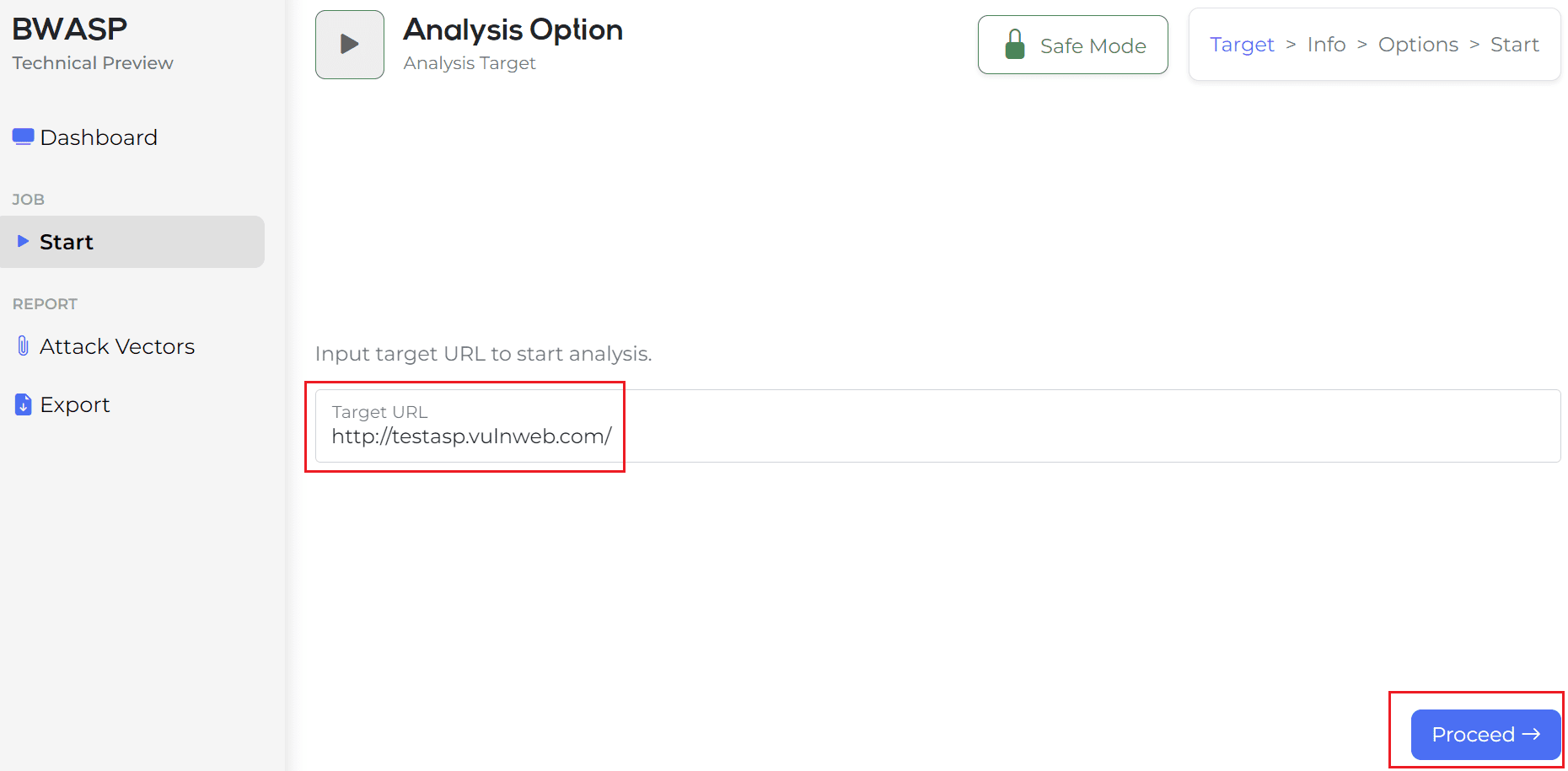
If you run the automatic analysis function in Figure 1, the target URL is testasp as shown in Figure 2, but enter the site you want to test and click the Process button.
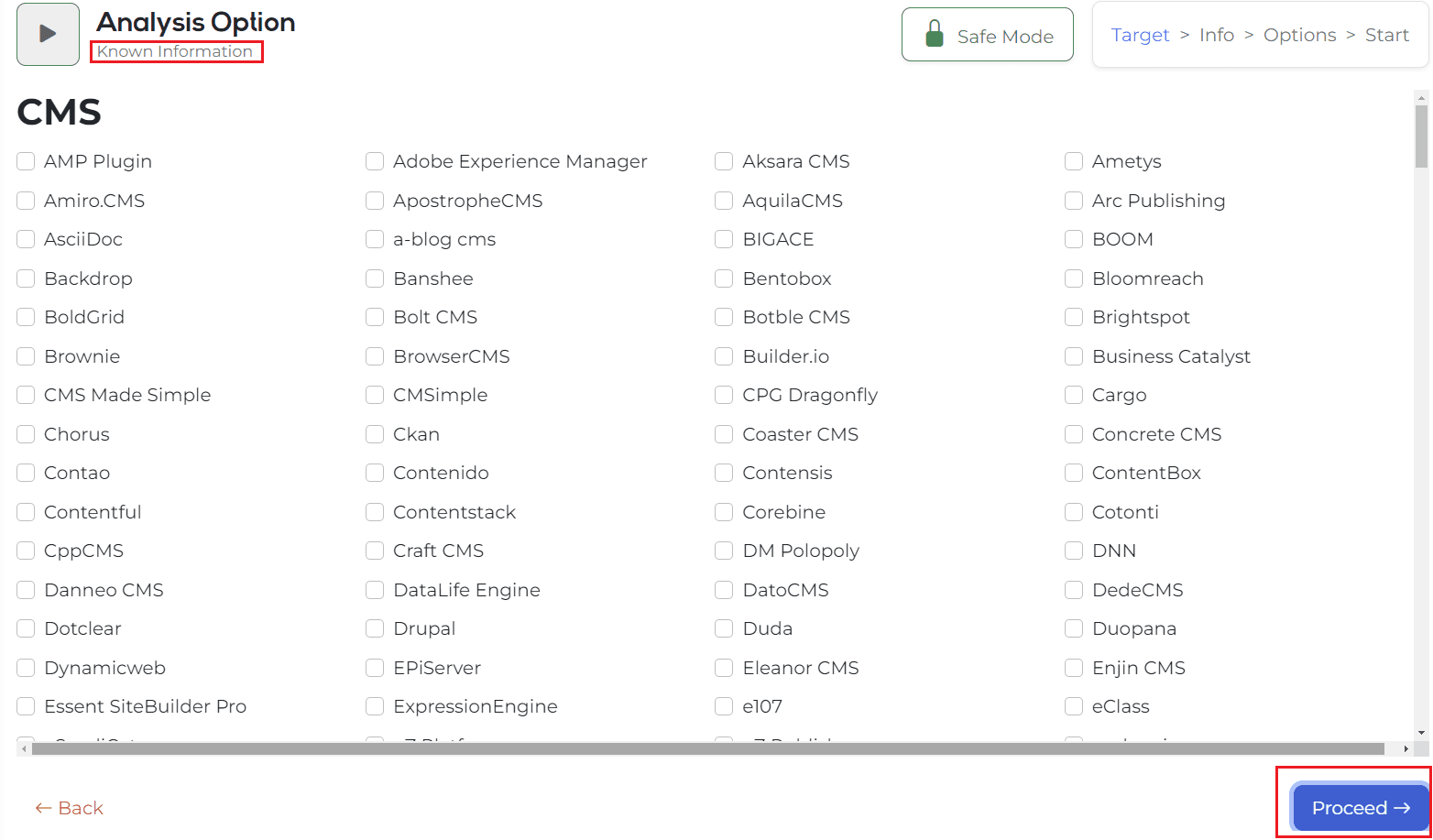
Then, it is switched to a screen where you can input the information you already know, and if you already know information, you can click on the corresponding environment and enter the version. (If you don’t know the information in the target URL, click the Process button immediately.)
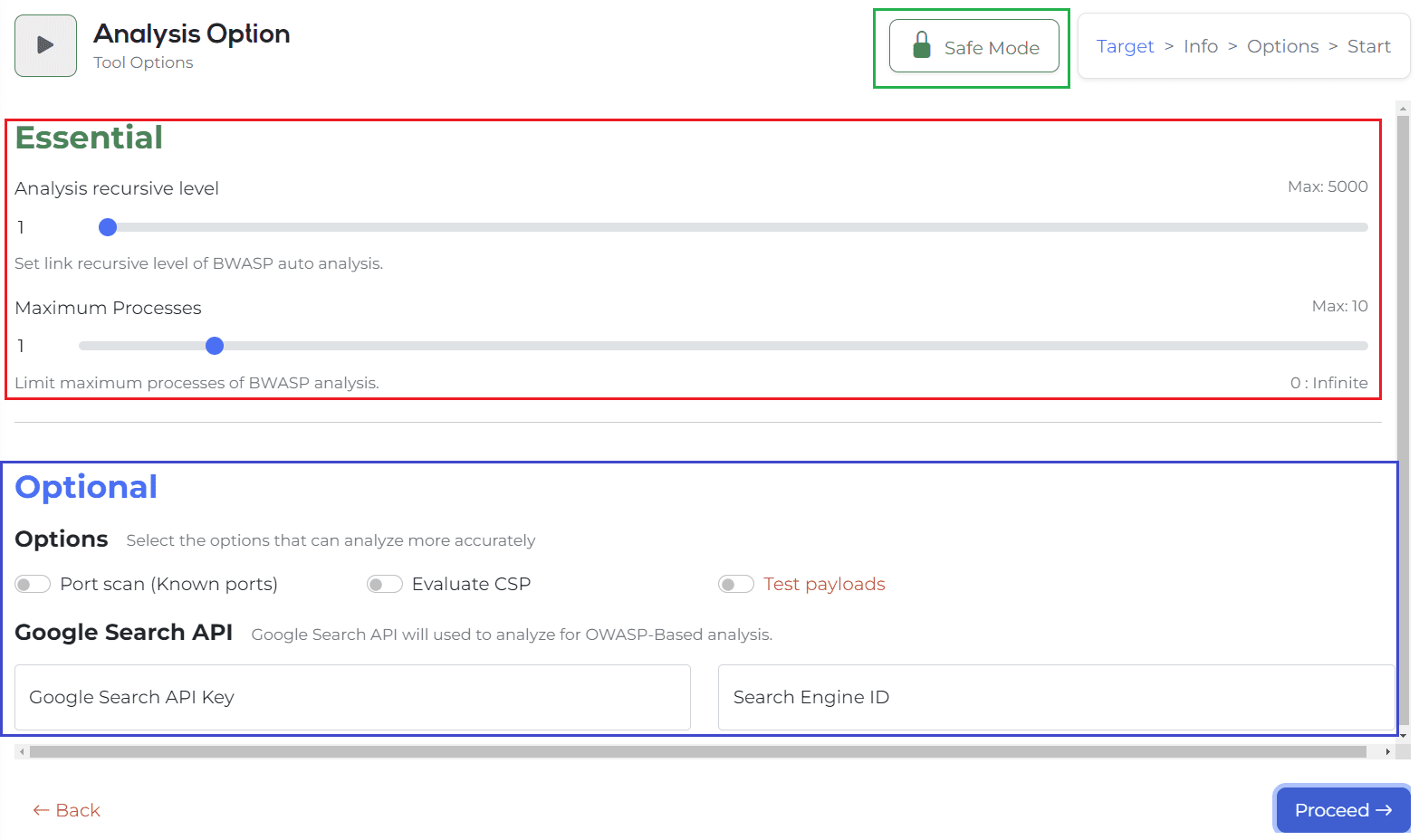
[Essential]
Analysis recursive level is an option to specify a crawling search level. Up to 5000 can be set. You can also directly modify the numerical value shown on the left.
Maxim Processes is an option to determine the number of multi-processes. The speed of analysis can be increased by designating this number. 1 to 10 are the basic parts that can be designated, and if 0 is designated, the number of multi-processes can be turned indefinitely.
[Optional]
Attack option -> Test payloads
The test payload is an option to proceed with the attack. Currently, only attacks in the form of checking only SQL injection errors are implemented. It is possible to check and proceed only when ‘Unlock’ is performed through the [Disable Risk Lock] button. (This tool aims to minimize availability infringement, reduce server load, and analyze, so the attack option is basically locked.)
- According to the current attack option, the results are registered in the DB and the pages that detect errors are divided, but the exposure in the guidelines is still under development, so we will update it as soon as it is corrected!
Port scan, CSP is basically there, and there is a Google Search API input column.
This is a function that helps you discover indexing information and admin pages through Google Search, and you can proceed only with Google Search API Key and Engine ID values.
-> To sum up, if there is no corresponding value among the options above, click the Process button to move on.
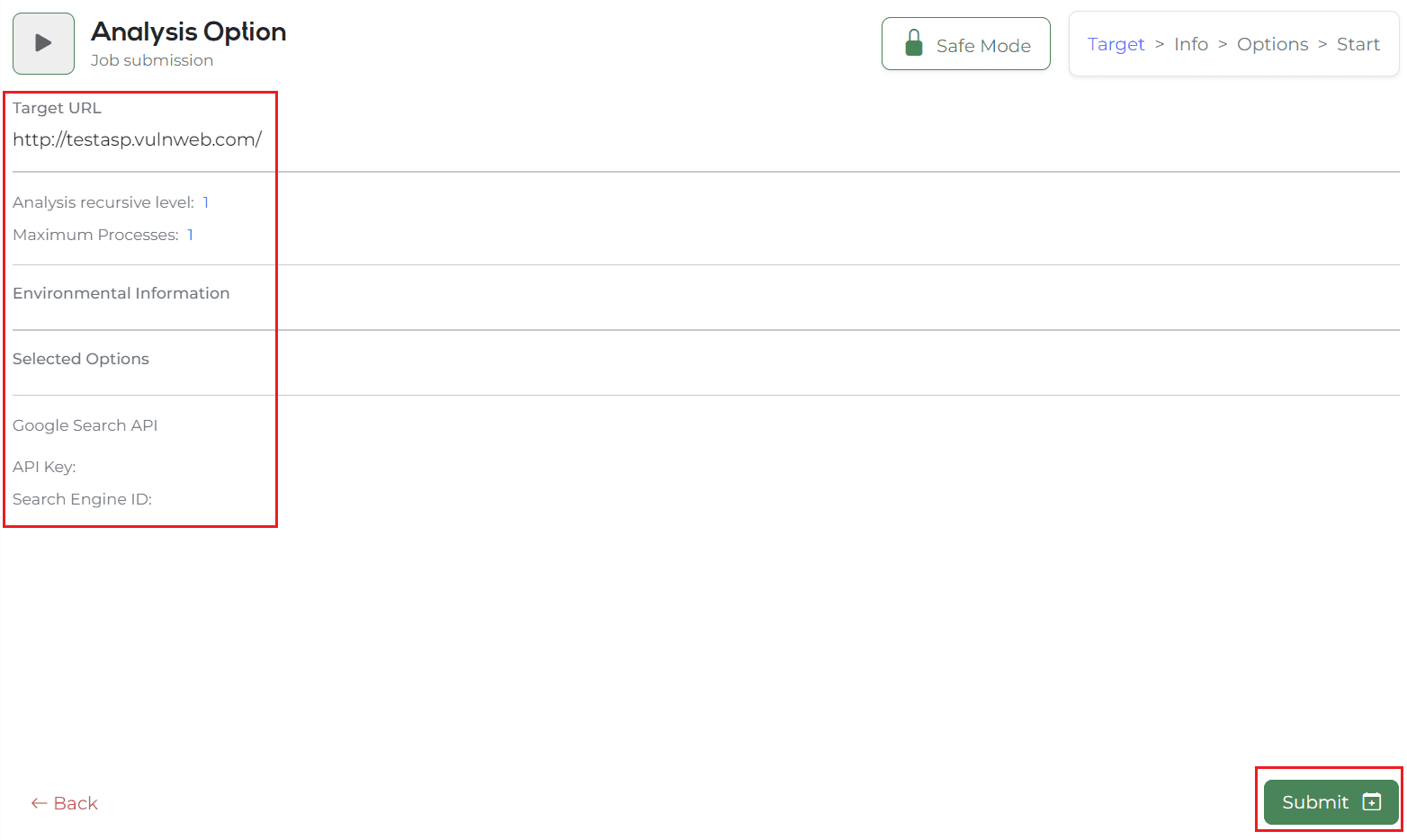
If you move on, you will be turned into a page where you can check the final entered information. The summary of the information here is as follows.
- Target URL.
- Crawling search level.
- Number of multi-processes.
- Contents of entering web environment information that you already know.
- Contents for selected options such as port scan, CSP, Test payloads, etc.
- Google Search API Key and Engine ID values
After finally checking the above values, the automatic analysis function is performed immediately by clicking the Submit button!
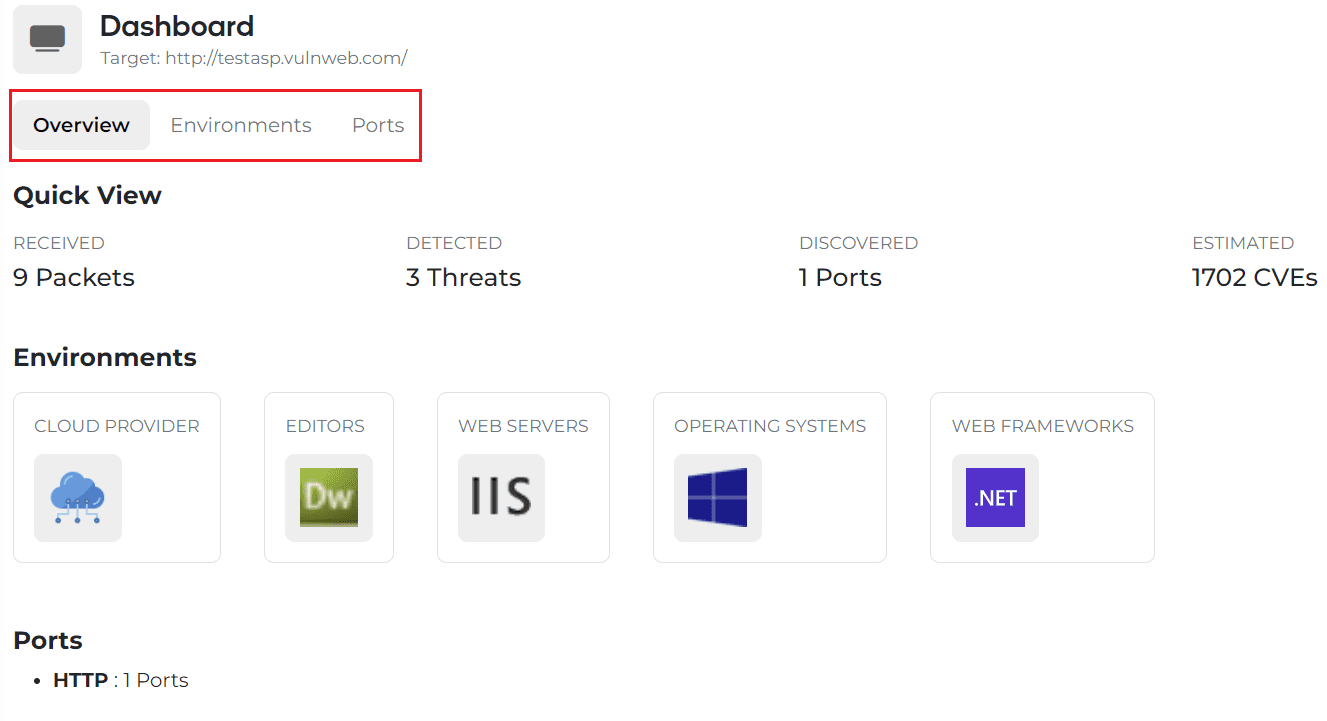
When you press the Submit button in Figure 5, a real-time notification is an output, and if you wait a little bit, it automatically switches to the Dashboard screen. Thereafter, web environment information, port information, and the number of CVEs to be imported in real-time can be determined.
Here, you can check the URL information entered in Figure 6 again, and if you want to proceed with the analysis again with other information, you can return to Figure 2 by clicking the Start button on the left side and proceed with the analysis.
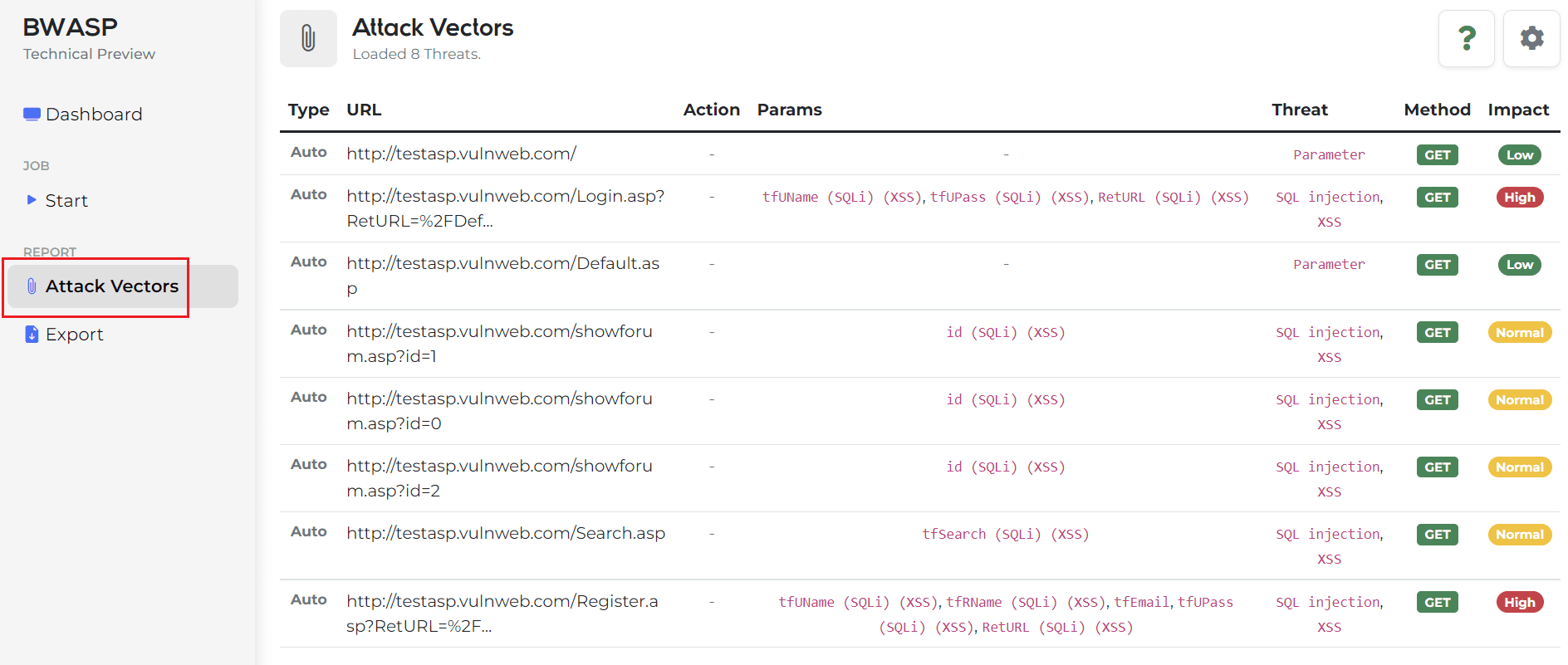
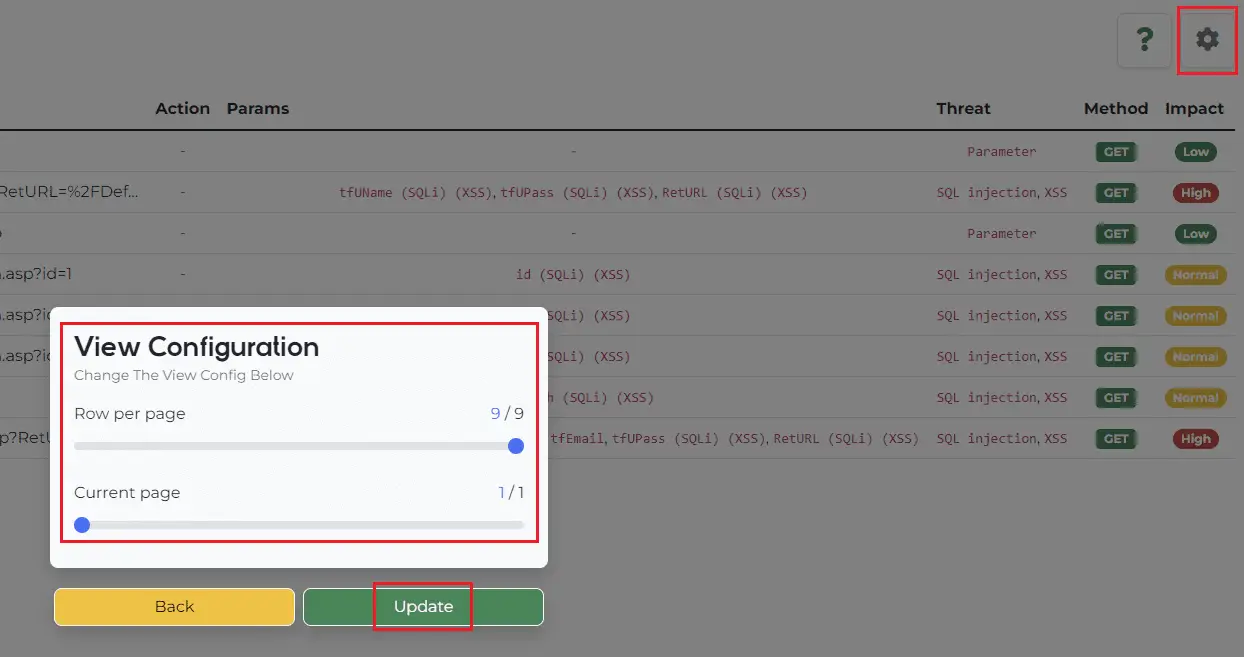
If you want to see the Attack Vector in real-time in the middle of the process, click Attack Vector on the left side of Figure 7 to check the Attack Vector as shown in Figure 7. The added real-time data can be viewed continuously by UPDATE through the right setting icon in Figure 7.
And by clicking on each analyzed information record, detailed information can be checked modally.
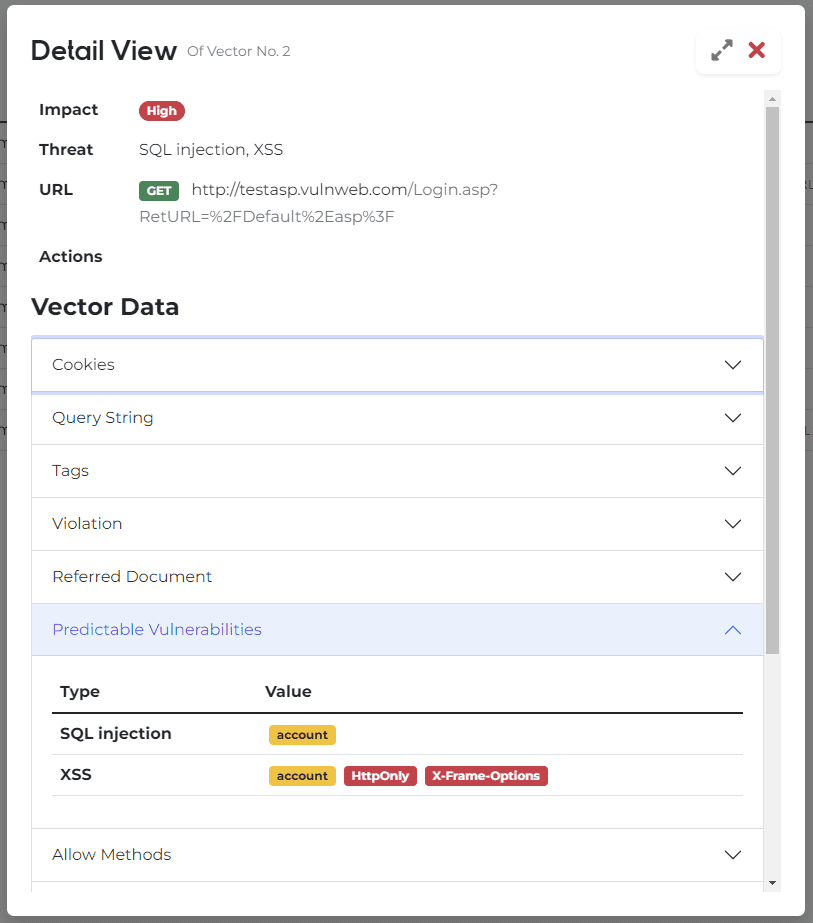
In Modal, you can check the following information.
- Basic information such as impact level seen in records and predicted vulnerability items.
- Cookies
- Query Strings
- Input Tag
- Main Information and Communication-based Guide
- Cheat Sheet that you can refer to according to the vulnerability items.
In the case of the design, it is currently updated and can be checked more neatly than [Figure 9].

This screen that appears when you click the icon (saw wheel) is [Figure 9].
The paging function is currently implemented as above, and the basic paging function in the lower right is still being implemented.
The attack vector information added may be updated and viewed through the above function.