C2-Hunter: extract Command and Control (C2) traffic from malwares in real-time
C2-Hunter
-
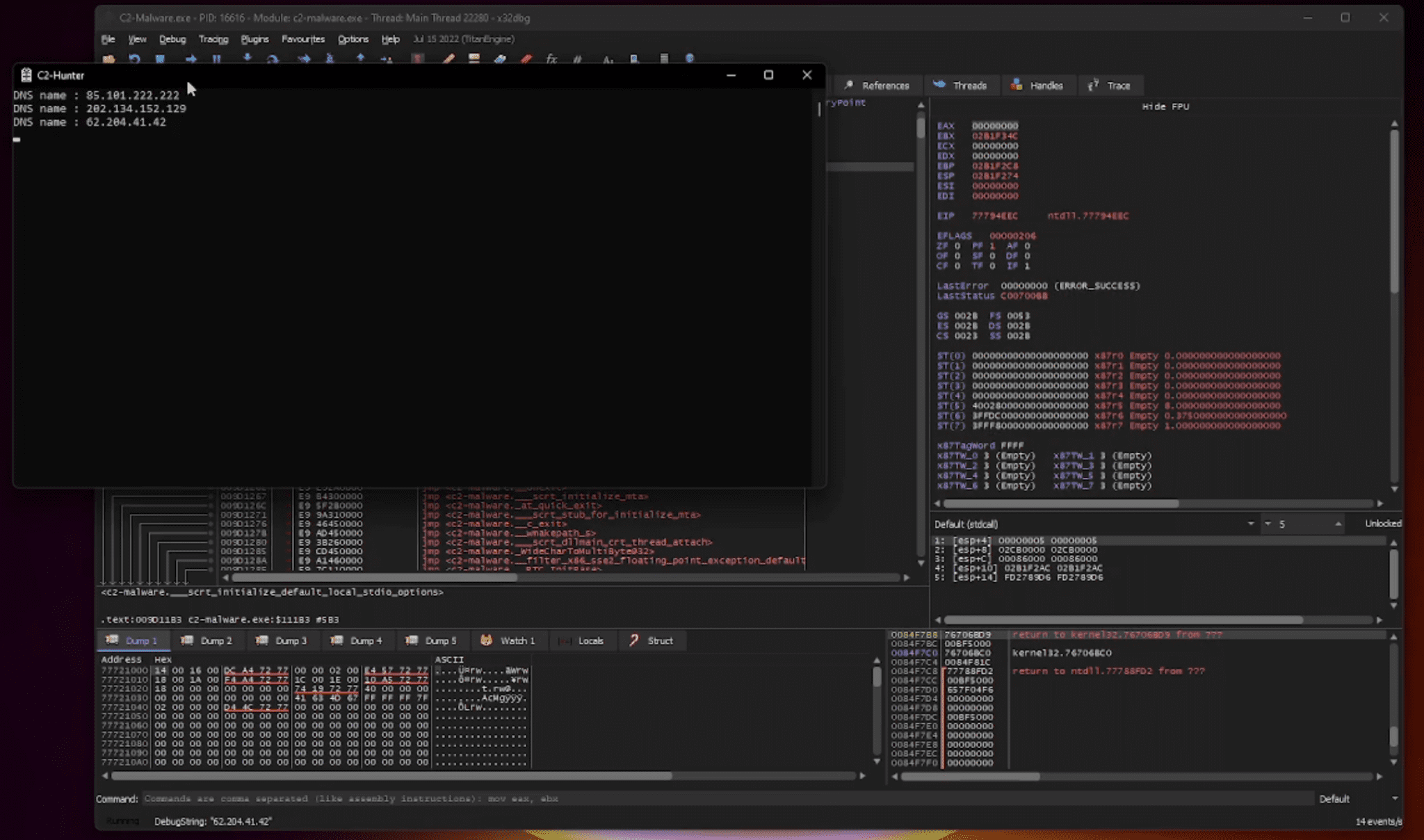
C2-Hunter is a program designed for malware analysts to extract Command and Control (C2) traffic from malwares in real time. The program uses a unique approach by hooking into win32 connections APIs.
-
With C2-Hunter, malware analysts can now intercept and analyze communication in real time, gaining valuable insights into the inner workings of cyber threats. Its ability to track C2 elements of malware makes it an essential tool for any cyber security team.

Features
- Real-time extraction of C2 traffic
- Bypasses malware time delays to speed up the extraction process (SOON)
Requirements
- Windows Operating System
- Administrator Privileges





