CANalyzat0r: Security analysis toolkit for proprietary car protocols
CANalyzat0r
Why another CAN tool?
- Built from scratch with new ideas for analysis mechanisms
- Bundles features of many other tools in one place
- Modular and extensible: Read the docs and implement your own analysis mechanisms
- Comfortable analysis using a GUI
- Manage work in separate projects using a database
- Documentation: Read the docs if you need a manual or technical info.
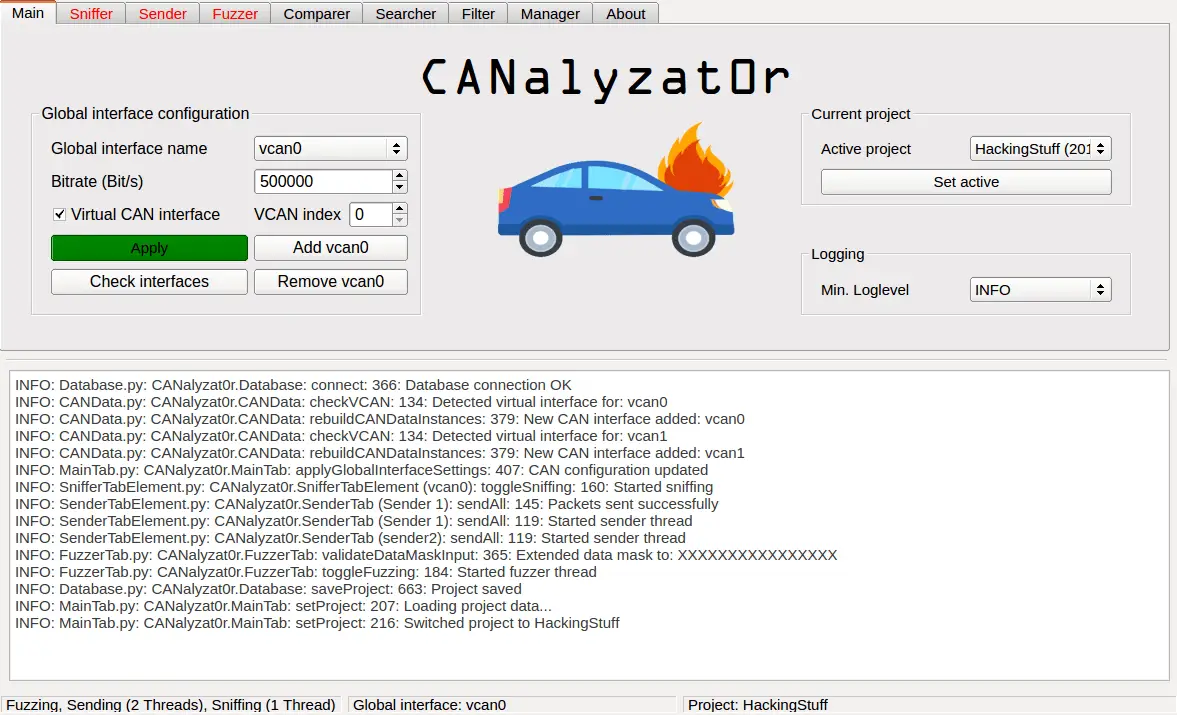
Features
- Manage interface configuration (automatic loading of kernel modules, manage physical and virtual SocketCAN devices)
- Multi interface support
- Manage your work in projects. You can also import and export them in the human readable/editable JSON format
- Logging of all actions
- Graphical sniffing
- Manage findings, dumps and known packets per project

- Easy copy and paste between tabs. Also, you can just paste your SocketCAN files into a table that allows pasting

- Threaded Sending, Fuzzing and Sniffing

- Add multiple analyzing threads on the GUI
- Ignore packets when sniffing – Automatically filter unique packets by ID or data and ID
- Compare dumps
- Allows setting up complex setups using only one window
- Clean organization in tabs for each analysis task
- Binary packet filtering with randomization
- Search for action specific packets using background noise filtering

- SQLite support
- Fuzz and change the values on the fly
This software project is a result of a Bachelor’s thesis created at SCHUTZWERK in collaboration with Aalen University by Philipp Schmied.
Please refer to the corresponding blog post for more information.









