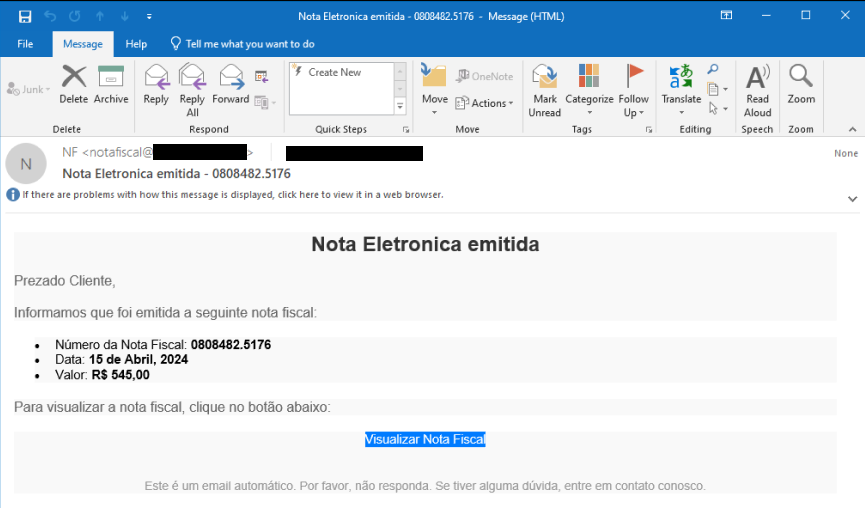
An example unsolicited email distributing CarnavalHeist.
A new banking Trojan named “CarnavalHeist” is targeting Brazilian users, exploiting the country’s festive spirit to steal financial data. Discovered by Cisco Talos, this malware campaign has been active since February 2024, using sophisticated tactics to evade detection and drain bank accounts.
Cisco Talos assesses with high confidence that CarnavalHeist is of Brazilian origin. This conclusion is drawn from the extensive use of Portuguese throughout the malware‘s infection chain and infrastructure, as well as the targeting of prominent Brazilian financial institutions. The command and control (C2) infrastructure exclusively uses the BrazilSouth availability zone on Microsoft Azure, further underscoring its Brazilian roots.

The initial infection vector for CarnavalHeist involves financially themed spam emails containing fake invoices. These unsolicited emails lure users into clicking malicious URLs, which are shortened using the IS.GD URL shortener service. Once clicked, the URL redirects users to a server hosting a fake web page where they are prompted to download what appears to be an invoice.
The fake web pages often reference “Nota Fiscal Eletrônica,” the Portuguese term for an electronic invoice, adding a layer of authenticity to the deception.

Once the user attempts to download the supposed invoice, the attack proceeds with downloading a LNK file via WebDAV. This LNK file, upon execution, initiates the next stage of the infection chain by executing malicious scripts and commands. The LNK file’s metadata reveals common techniques used by threat actors to conceal malicious activities.
Execution Flow:
- A fake “NotaFiscal.pdf” file is created in the user’s Downloads directory, displaying a “View Unavailable” message to deceive the user.
- Simultaneously, a minimized
cmd.exeprocess runs the malicious component.
In addition to LNK files, some variants of CarnavalHeist use MSI installers to execute the initial payload. Earlier variants relied on less sophisticated Python scripts, while newer versions employ the pythonmemorymodule package for more obfuscated and refined execution.
Cisco Talos’ analysis revealed significant clues about the actors behind CarnavalHeist. Examination of the malware samples exposed a user account “bert1m” and a GitHub account “marianaxx0492494,” which hosted parts of the malware.
Further investigation into WHOIS information for domains used in the campaign provided the full name, email address, and CPF (Cadastro de Pessoa Física) of the individuals registering the domains. This CPF, a national ID in Brazil, linked the individuals to specific criminal records and businesses in Maranhão, Brazil.
The CarnavalHeist banking trojan represents a significant threat to Brazilian financial institutions and users. By leveraging sophisticated overlay attacks and exploiting financial-themed lures, the malware aims to steal sensitive information and conduct financial fraud.