caronte
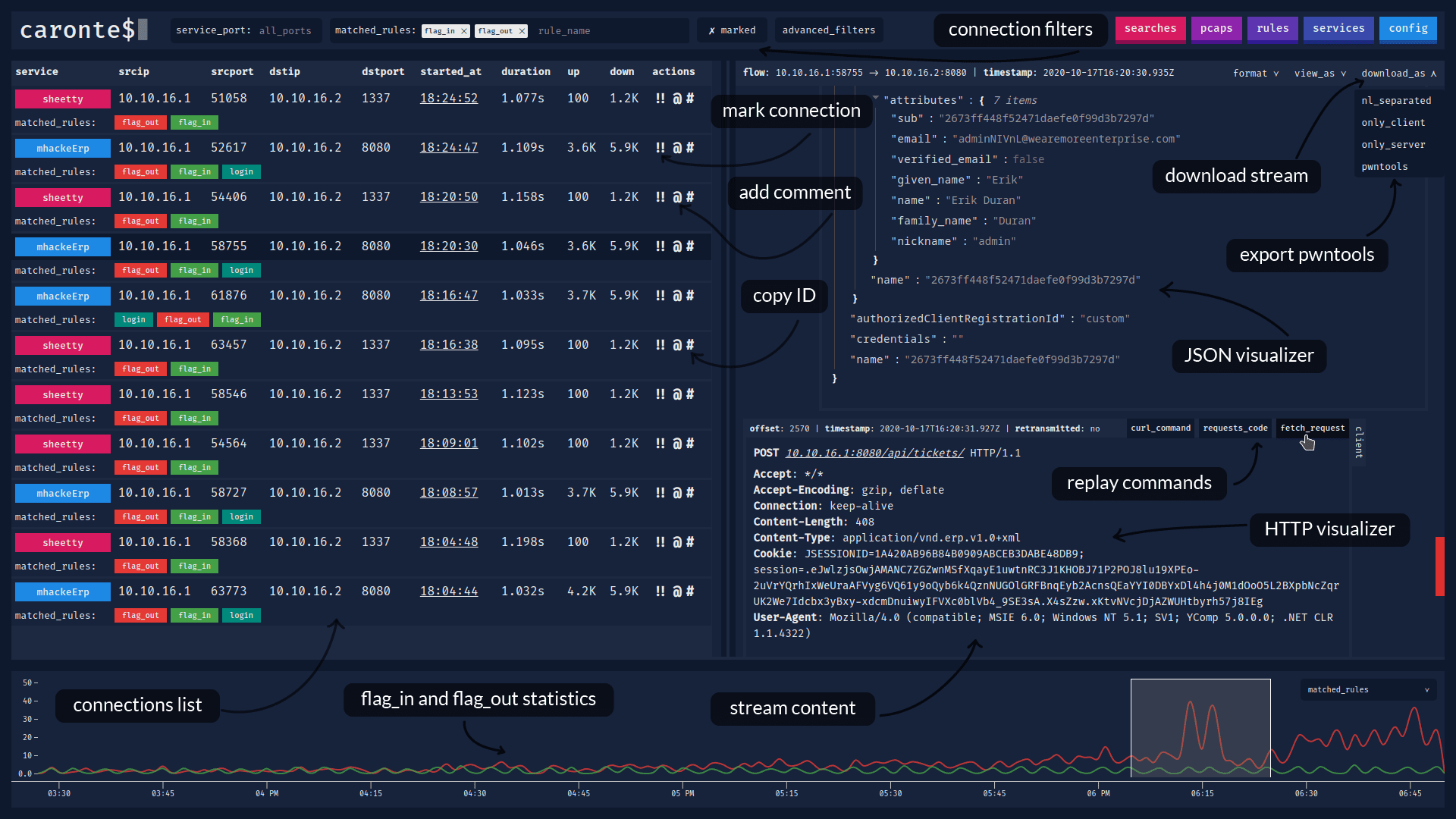
Caronte is a tool to analyze the network flow during the capture of the flag events of type attack/defence. It reassembles TCP packets captured in pcap files to rebuild TCP connections and analyzes each connection to find user-defined patterns. The patterns can be defined as regex or using protocol-specific rules. The connection flows are saved into a database and can be visualized with the web application. REST API is also provided.
Features
- immediate installation with docker-compose
- no configuration file, settings can be changed via GUI or API
- pcaps to be analyzed can be loaded via
curl, either locally or remotely, or via the GUI- it is also possible to download the pcaps from the GUI and see all the analysis statistics for each pcap
- rules can be created to identify connections that contain certain strings
- pattern matching is done through regular expressions (regex)
- regex in UTF-8 and Unicode format are also supported
- connections can be labeled by type of service, identified by the port number
- each service can be assigned a different color
- ability to filter connections by addresses, ports, dimensions, time, duration, matched rules
- a timeline shows statistics with different metrics sampled per minute
- some of these metrics are connections_per_service, client_bytes_per_service, server_bytes_per_service, duration_per service, matched_rules
- with the matched_rules metric, it can be possible to see the relationship between flag_in and flag_out
- the timeline contains a sliding window which can be used to search for connections in a certain time interval
- some of these metrics are connections_per_service, client_bytes_per_service, server_bytes_per_service, duration_per service, matched_rules
- advanced search by term negated term, exact phrase, regex, negated regex
- the performed searches are saved to be instantly repeated the following times
- the detected HTTP connections are automatically reconstructed
- HTTP requests can be replicated through
curl,fetchandpython requests - compressed HTTP responses (gzip/deflate) are automatically decompressed
- HTTP requests can be replicated through
- ability to export and view the content of connections in various formats, including hex and base64
- JSON content is displayed in a JSON tree viewer, HTML code can be rendered in a separate window
- occurrences of matched rules are highlighted in the connection content view
- supports both IPv4 and IPv6 addresses
- if more addresses are assigned to the vulnerable machine to be defended, a CIDR address can be used
Changelog v1.21
- Replace Travis CI with Github Actions
- Docker image in now published on Github Registry
- Add CHANGELOG.md
- Update Dockerfile to separate Go build and npm build stages
- Update backend and frontend dependencies
- Added a control to not wrap regex around slashes if the user add a pattern that already has slashes
Install & Use
Copyright (C) 2020 eciavatta