At the I/O conference a few days ago, Google’s Duplex Voice AI was very impressive in its...
Vulnerability
As an early software-defined network protocol, OpenFlow exposed a security flaw that was long-established, ubiquitous, and difficult...
The United States Computer Emergency Response Team (CERT) announced on May 9 that systems such as Windows, macOS, Linux, FreeBSD,...
Recently FireEye revealed that there are multiple loopholes in the Logitech Harmony Hub smart home control system, and...
On May 1st, Avanan researchers discovered a 0-day vulnerability called baseStriker in Office 365. An attacker can...
On May 9th, Adobe officially released the May security update, which fixed several security vulnerabilities including Adobe...
Security researchers have proven Rowhammer flaws in DRAM chips can be used to attack Android smartphones. Rowhammer is...
According to BleepingComputer, a researcher from Argentina discovered a flaw (CVE-2018-9995) that allowed him to log in...
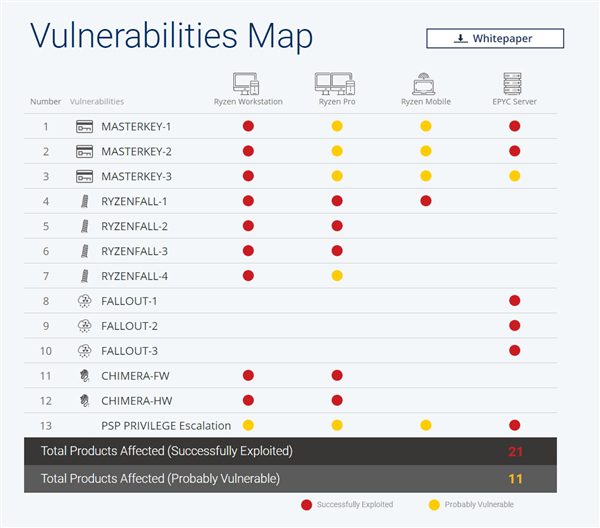
In mid-March of this year, CTS-Labs, an unrecognized security agency, suddenly blew up and claimed that there...
According to ITnews reported that researchers found and reported in the Intel processor 8 new Spectre-style hardware...
Microsoft informed users on May 2 that an update to the Windows host computing service Shim library...
A Dutch cybersecurity company found that the in-vehicle infotainment (IVI) system that deploys some models of the...
According to recent news from ZDNet, security researchers found that they can remotely access more than one...
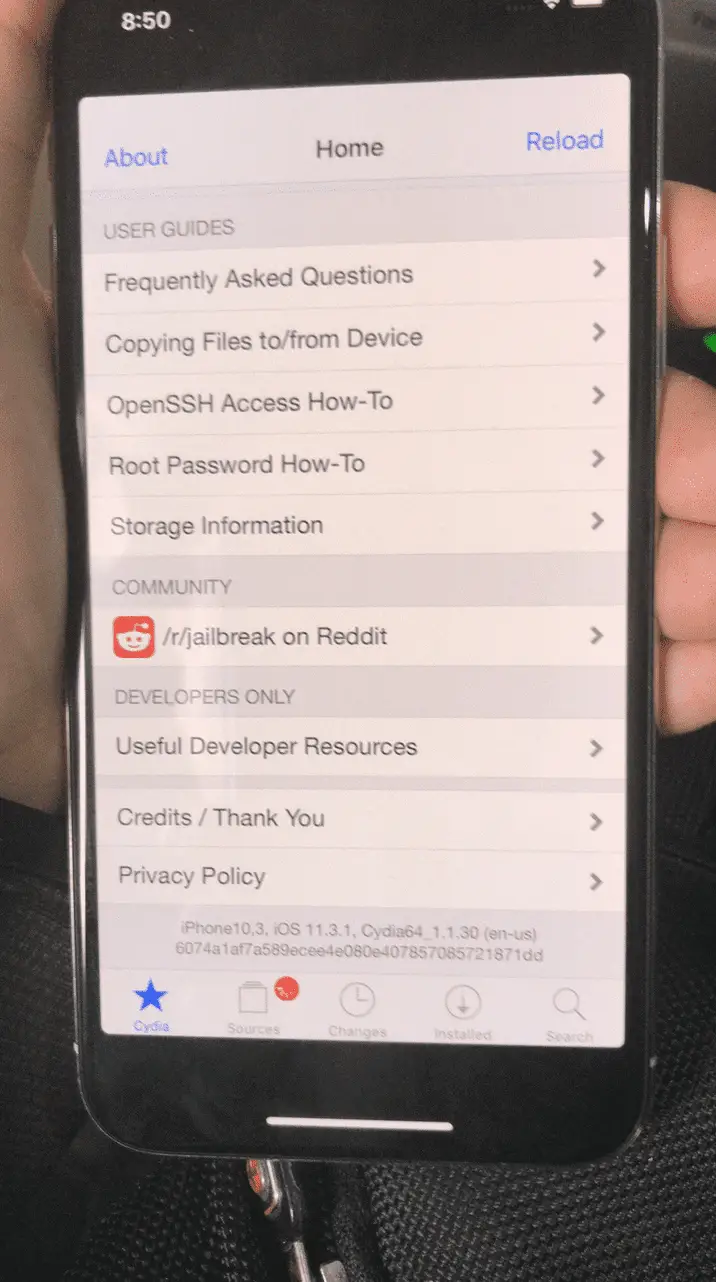
Tencent’s Keenlab team has repeatedly demonstrated successful jailbreaks on Apple latest firmware. This time, Keenlab broke through again and successfully...
Hackers started on April 17 and targeted Oracle WebLogic Server’s computers. At the time, Oracle released a quarterly...