Category: Web Exploitation
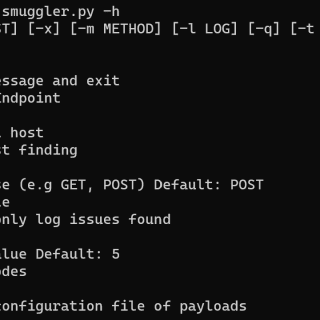
Smuggler An HTTP Request Smuggling / Desync testing tool written in Python 3. IMPORTANT This tool does not guarantee any false positives or false negatives. Just because a mutation may report OK does not...
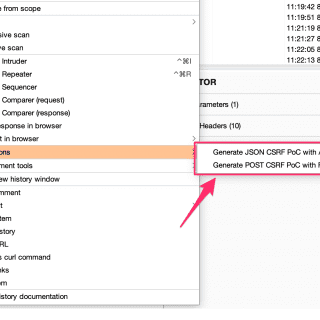
LazyCSRF LazyCSRF is a more useful CSRF PoC generator that runs on Burp Suite. Motivation Burp Suite is an intercepting HTTP Proxy, and it is the defacto tool for performing web application security testing....
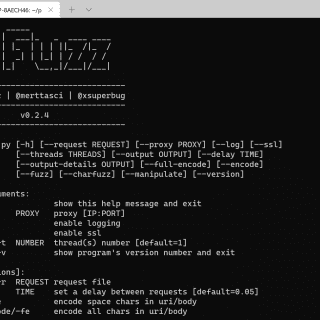
What is pFuzz pFuzz is a tool developed in the python language to have advanced fuzzing capability in web application research. Since the application has a modular structure, it has the ability to quickly...
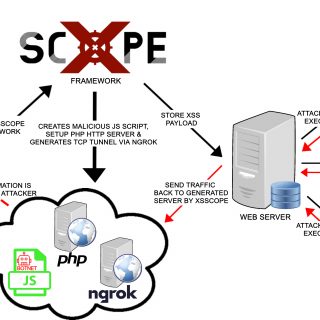
XSScope Go beyond the alert XSScope is one of the most advanced GUI Frameworks for XSS Client-side attacks. It can perform different XSS attacks and HTML Injections in real-time. Features Perform XSS botnet attack(s)....
RAT: Reinforcement-Learning-Driven and Adaptive Testing for Vulnerability Discovery in Web Application Firewalls Abstract Due to the increasing sophistication of web attacks, Web Application Firewalls (WAFs) have to be tested and updated regularly to resist...
MySQL Fake Server A fake MySQL Server used for penetration, which is implemented by native python3 with out any other dependency package. Use MySQL Client Arbitrary File Reading Exploit MySQL JDBC Client’s Java Deserialization...
WAF-A-MoLE A guided mutation-based fuzzer for ML-based Web Application Firewalls, inspired by AFL and based on the FuzzingBook by Andreas Zeller et al. Given an input SQL injection query, it tries to produce a semantic invariant query that is able...
interactsh Interactsh is an Open-Source Solution for Out of band Data Extraction, A tool designed to detect bugs that cause external interactions, For example – Blind SQLi, Blind CMDi, SSRF, etc. Features DNS/HTTP/SMTP Interaction support...
Mole A framework for identifying and exploiting out-of-band application vulnerabilities. Installation & Setup Mole Install Python >= 3.6 git clone https://github.com/ztgrace/mole.git virtualenv -p /usr/bin/python3 venv source venv/bin/activate ./venv/bin/pip3 install -r requirements.txt git submodule update...
Vulmap – Web vulnerability scanning and verification tools Vulmap is a vulnerability scanning tool that can scan for vulnerabilities in Web containers, Web servers, Web middleware, and CMS and other Web programs, and has...
N1QLMap N1QLMap is an N1QL exploitation tool. Currently works with the Couchbase database. The tool supports data extraction and performing SSRF attacks via CURL. More information can be found here. Download git clone https://github.com/FSecureLABS/N1QLMap.git Demo...
RmiTaste RmiTaste allows security professionals to detect, enumerate, interact, and attack RMI services by calling remote methods with gadgets from ysoserial. It also allows calling remote methods with specific parameters. Disclaimer RmiTaste was written...
XXExploiter It generates the XML payloads, and automatically starts a server to serve the needed DTD’s or to do data exfiltration. Some notes: If you choose to use OOB or CDATA mode, XXExploiter will...
weblogicScaner weblogic Vulnerability Scanning Tool. If there is an unrecorded and open POC vulnerability, please submit the issue. Some bug fixes were made, some POC did not take effect or configuration errors. I checked...
Vailyn Vailyn is a multi-phased vulnerability analysis and exploitation tool for path traversal/directory climbing vulnerabilities. It is built to make it as performant as possible and to offer a wide arsenal of filter evasion...