Ransomware is malicious software that encrypts your access to your system or data. The attacker then demands...
Technique
Pictures are very important for sharing information. But turning the text in these pictures into editable words...
Happy New Year! Say goodbye to the old and welcome the new, 2024 has already begun! Your...
Growing your business requires getting new leads and transforming them into loyal customers. This is a challenge...
Businesses move in a digital environment where online visibility, effective communication, and interaction with potential customers have...
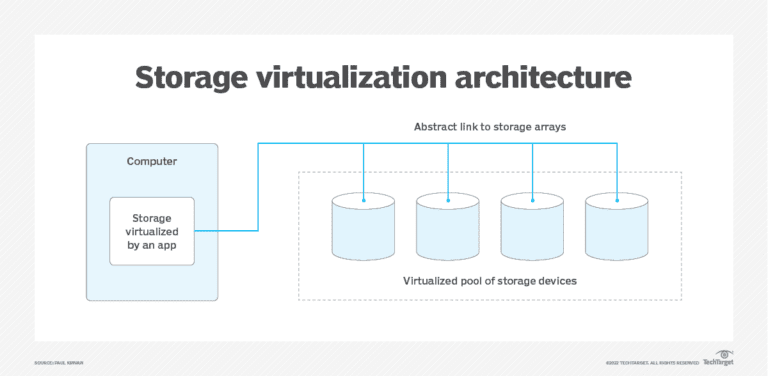
Storage virtualization is revolutionizing how businesses used to manage and store their ever-growing data. Put simply, it...
In the dynamic realm of eCommerce, Magento stands as a titan, offering robust functionalities that cater to...
Data security is of critical importance in today’s ever-changing digital landscape, for both individuals and businesses. Taking...
Marketing is a lively and tough field in business. It needs new ideas and imagination to get...
In the world of business, scalability is a key factor for success. As your business grows, so...
Security Service Edge (SSE) is popular with remote companies and businesses that have added multiple cloud-based components...
Everyone worries about the prospect of moving. There are so many things that could go wrong, after...
CapCut is a super cool app for editing your videos. It’s not just for your phone; you...
The financial landscape is undergoing a significant transformation, fueled by advancements in technology and a shift towards...
Java Collections Framework is a set of interfaces and classes that provide a standardized way to store,...