Most people tend to think of corruption and financial crimes as victimless wrongdoings that occur at no...
Technique
COVID-19 urged many businesses to go remote or create novel online solutions to continue their work online....
Almost all businesses now use the cloud to achieve their objectives. Storage, computing, services- clouds are an...
You come to realize that information has leaked from one of your social media accounts. That’s because...
While cybercriminals and hacker gangs like REvil and Maze are becoming everyday concerns, you are far from...
When you are starting a business it is not an easy task especially if you are someone...
With a good audio file converter, you can convert various music albums, podcasts, and other items into...
How to prove the value of marketing research? There are, of course, apparent metrics like KPI and...
Ransomware isn’t new; but, unfortunately, this particular type of cyber crime has been accelerating in the recent...
Dark Sky was one of the most popular Application Programming Interface (API) related to weather services available...
There are quite a few types of bill of materials in manufacturing, and each is very important...
Hackers only need about 15 minutes before they can break into an email account. When customers hand...
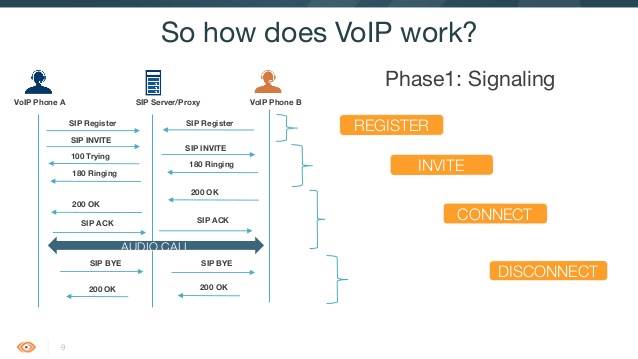
Companies choose VoIP to make their phone calls for a number of reasons. The low cost is...
Technology has been credited with helping many businesses succeed. One way that technology has had a significant...
In this modern age, there’s nothing more terrifying than having all your work altered or entirely wiped...