The MTA certification is a starting point that gives all the interested candidates a huge boost for...
Technique
You must have an idea about JSON’s significance if you are a programmer or a software analyst....
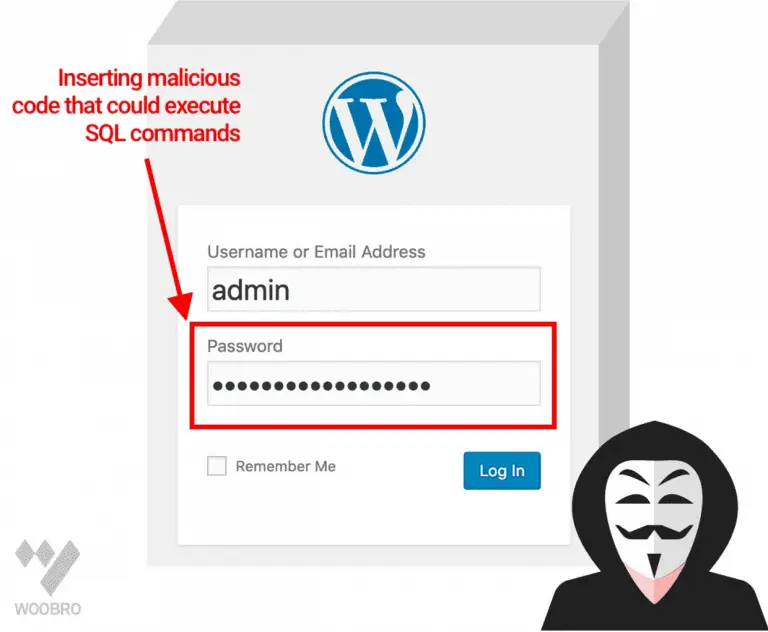
Nowadays, cyber-attacks are no longer rare. News of identity theft and hacking abound. And if you’re digitizing...
With more cyber threats today than ever before, there are too many companies with unoptimized defenses. On...
We cannot emphasize how vital cyber-security is, not only in the business world but also at an...
What does a student dream about? The answer is obvious: effective college results and the total absence...
Such as email publishing, wireless publishing, electronic ink, etc. Print on Demand is also part of the...
Farming may not seem very high tech to the average person, but as anyone in the business...
When people are frequently exposed to something, they learn how to adapt to it. This is why...
There are numerous things that can clarify you, for example, garments, shoes, or whatever else you wear....
Designing any hardware is a complicated process to complete, but not impossible. With anything, it all starts...
Public Wi-Fi is convenient but it also presents a danger. This is because public Wi-Fi isn’t necessarily...
Cyber-attacks are becoming more frequent and threatening than ever before. Part of the reason for the rapid...
There are gadgets we buy because everybody else is buying them, or because we have some money...
Summary: Many computer and smartphone manufacturers today claim that their devices don’t need an antivirus. This is...