Recently, Kaspersky analysed the DDoS attack in the second quarter of 2018. The report was detailed and lengthy. For the convenience of reading, this article has compiled some contents.
Overview
In the second quarter of 2018, cybercriminals continued the trend of looking for exotic vulnerabilities in UDP transport protocols. Soon other complex attack amplification methods will appear one after another. Another technical discovery worth noting is the potential to create botnets using the UPnP protocol, but fortunately, they are still scarce in the wild.
Reduced Windows botnet activity: In particular, Yoyo activities have experienced many declines, and Nitol, Drive, and skills have also declined. At the same time, Xor’s attacks on Linux have increased significantly, while another infamous Linux botnet, the Darkai campaign, has decreased slightly. The most popular type of attack is SYN flooding.
2017 – 2018 DDoS attack changes
In the first half of 2018, compared with the second half of 2017, the average and maximum attack power dropped significantly. This can be explained by the seasonal slowdown usually observed at the beginning of the year. However, a comparison of the H1 indicators in 2017 and 2018 shows that since last year, the attack power has increased considerably.
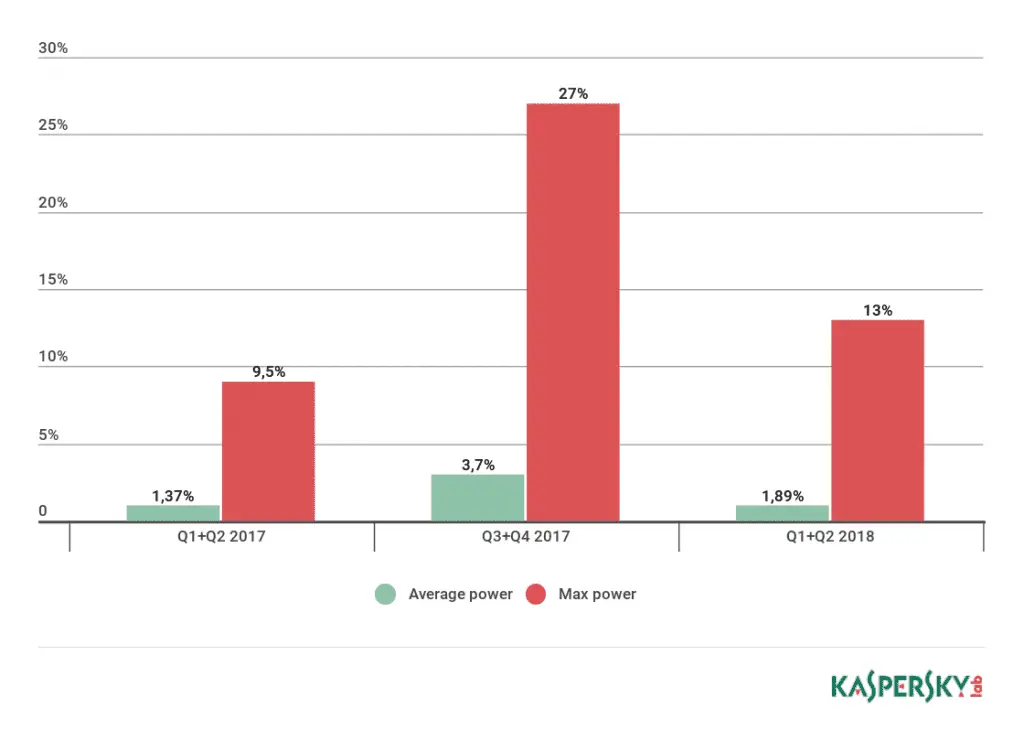
One way to increase attack power is by third-party amplification. Hackers continue to look for ways to amplify DDoS attacks through new (or forgotten old) vulnerabilities in widely popular software. This time, the KDP team detected and repelled hundreds of Gbit/s capacity attacks that exploited a weakness in the CHARGEN protocol— a straightforward old protocol that emerged as an RFC 864 in 1983.
CHARGEN is used for testing and measurement and can listen to TCP and UDP sockets. In UDP mode, the CHARGEN server responds to any request with a packet with a string length of 0 to 512 random ASCII characters. The attacker uses this mechanism to send a request to the vulnerable CHARGEN server, where the victim’s address replaces the outgoing address. US-CERT estimates that the amplification factor is 358.8 times, but this number is somewhat arbitrary because the response is randomly generated.
Although the times and content limit the protocol, many open CHARGEN servers can found on the Internet. They are primarily printers and replication devices, where default enables the software.
As mentioned in the KDP and other providers (Radware, Nexusguard) report, the use of CHARGEN in UDP attacks may indicate that attacks using more available protocols (e.g., DNS or NTP) are waning because of the UDP flooding. The program is getting better and better. But because of the difficulty of this kind of attack, cybercriminals are reluctant to give up; instead, they hope that modern security systems can’t resist outdated methods. While searches for non-standard vulnerabilities will undoubtedly continue, the CHARGEN-type amplification attacks are unlikely to be popular in the world because of the lack of additional resources for vulnerable servers.
If cybercriminals become methodologically complex, they will open up new horizons when it comes to goals. DDoS attacks against home users are simple but not profitable, while attacks on companies are profitable but complex. Now, DDoS planners have found a way to make the most of the two worlds of the online gaming industry and streaming media. Take the increasingly popular e-sports competition as an example. In this kind of game, the winner will win thousands of dollars, sometimes even hundreds of thousands of dollars. The biggest races are usually held at special venues with specially designed screens and stands, but those who qualify for the competition are generally involved at home. In this case, a well-planned DDoS attack can quickly get the team out of the game early. The game server may also be the target of the attack, and the threat of damage may prompt the organiser to pay the ransom. According to Kaspersky Lab customer data, DDoS attacks e-sports gamers and websites to deny access and will become more common in the future.
Similarly, cybercriminals are trying to monetise the market for video game streaming channels. Streaming media professionals showed live broadcasts of favourite games, and viewers donated a small amount of money to support them. Of course, the more viewers there are, the more money the streaming media gets per play; the top players can earn hundreds or thousands of dollars, which is their job. The competition in this market segment is fierce, and DDoS attacks enable it to interfere with live broadcasts, leading users to find alternatives. Like e-sports athletes, home broadband is almost impossible to withstand DDoS attacks. They rely on their internet provider. The only solution currently available is probably to build a dedicated platform that provides better protection.
Quarter results
- The stormy period of the DDoS attack was the beginning of the quarter, especially in mid-April. In contrast, late May and early June were quite calm.
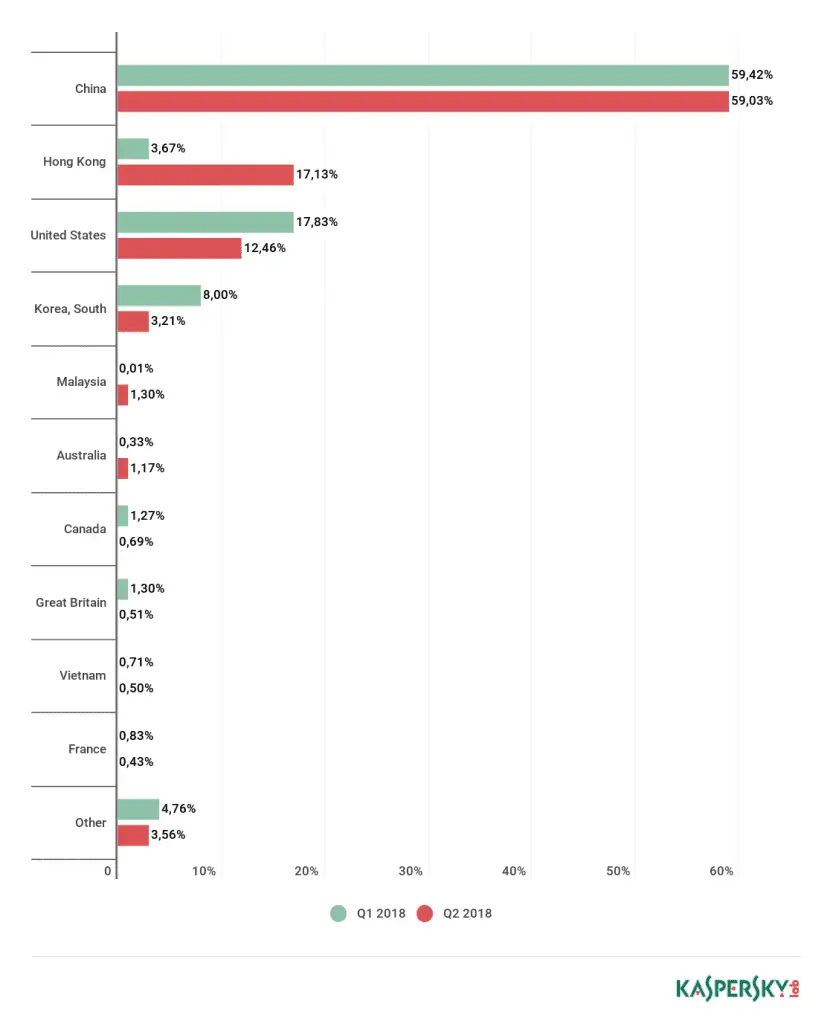
- China maintained the highest number of attacks (59.03%), followed by Hong Kong (17.13%). China also has the highest number of DDoS targets.
- The proportion of SYN attacks rose sharply to 80.2%; the second was 10.6% of UDP attacks.
- The attack share of Linux botnets has increased significantly to 94.47% of all single-family attacks.
Details
China’s share has barely changed (59.03%, compared with 59.42% in the first quarter). However, since the beginning of supervision, Hong Kong has risen to the top three for the first time, rising from fourth to second place: its share has increased nearly fivefold, from 3.67% to 17.13%, crowding out the United States (12.46%) and South Korea ( 3.21%), the share prices of these two countries fell by about 5%. Also, Malaysia is surprising; its ranking has rapidly risen to fifth place, currently accounting for 1.30% of the total number of DDoS attacks. Australia (1.17%) and Vietnam (0.50%) also ranked in the top ten, while Japan, Germany and Russia withdrew from the list. The United Kingdom (0.50%) and Canada (0.69%) entered the eighth and seventh respectively.
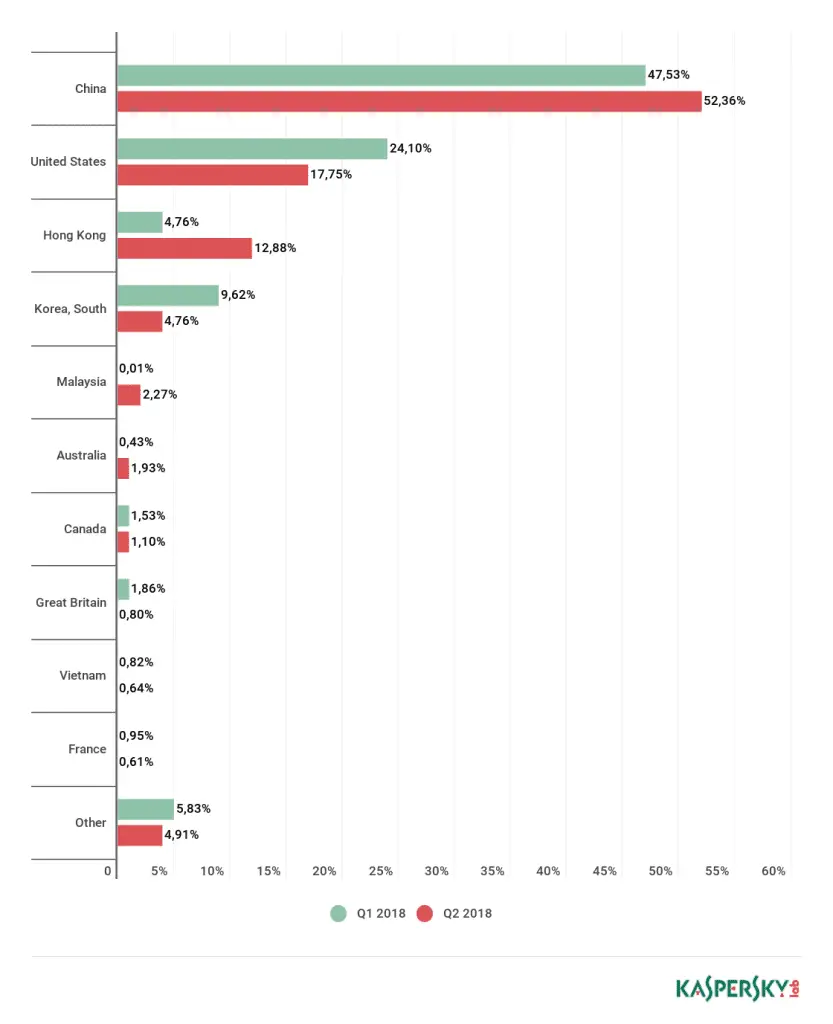
The territorial distribution of DDos targets is roughly the same as the distribution of attacks: China has the most significant share (52.36%), an increase of 5 percentage points from the previous quarter. The second place is the United States (17.5%) and the third place in Hong Kong (12.88%), replacing South Korea (4.76%). The UK dropped from the 4th to the 8th and now only accounts for 0.8% of the target.

Conclusion
The duration of the total attack has not changed much since the last quarter, but the proportion of medium-term attacks has increased while the percentage of shorter attacks has decreased. The intensity of the attack is also growing. The most effective target of cybercriminals seems to be cryptocurrency, but we will soon see DDS attacks against e-sports and streaming media becoming more common for small redemptions. Therefore, the market needs personal defence against DDoS attacks.
Source, Image: securelist