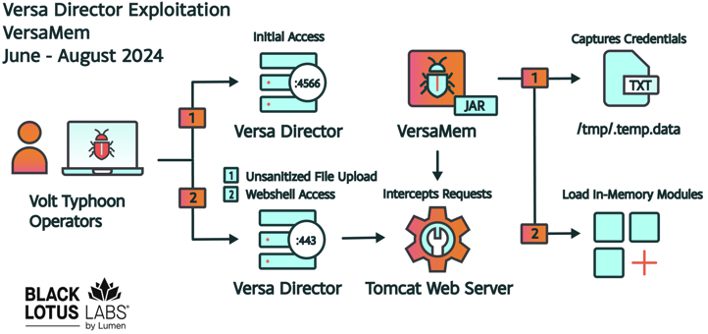
Overview of the Versa Director exploitation process and the VersaMem web shell functionality
Black Lotus Labs, a threat intelligence team within Lumen Technologies, has uncovered the active exploitation of a zero-day vulnerability in Versa Director servers, identified as CVE-2024-39717. This critical vulnerability, which affects all Versa Director versions prior to 22.1.4, has become a prime target for advanced persistent threat (APT) actors, particularly those linked to Chinese state-sponsored groups like Volt Typhoon and Bronze Silhouette.
Versa Director is a crucial component of Versa Networks’ software-defined wide area network (SD-WAN) architecture, widely used by internet service providers (ISPs) and managed service providers (MSPs) for managing network configurations and orchestrating SD-WAN functionalities. The discovery of CVE-2024-39717 has raised alarms across the cybersecurity landscape due to the potential for widespread exploitation.
This zero-day vulnerability allows attackers to gain initial administrative access via an exposed Versa management port, typically used for high-availability (HA) pairing of Director nodes. Once inside, attackers can deploy a custom-tailored web shell, known as “VersaMem,” to intercept credentials and execute additional malicious activities within the compromised environment.
The VersaMem web shell, uncovered by Black Lotus Labs, is a sophisticated tool specifically designed to exploit Versa Director servers. This Java-based web shell, first observed in the wild in June 2024, is modular and operates entirely in memory, making it difficult to detect and neutralize. This tool serves two primary functions:
- Credential Harvesting: VersaMem hooks into the Versa Director’s authentication process, capturing plaintext user credentials, encrypting them with AES, and storing them in a hidden file on the server. This allows the attackers to gain access to downstream networks as authenticated users, extending their reach beyond the initial compromise.
- Dynamic In-Memory Execution: The web shell leverages the Java Instrumentation API and Javassist to dynamically load and execute additional Java code in memory. This functionality enables attackers to inject malicious modules without leaving any trace on the disk, significantly evading traditional detection methods.
The initial deployment of VersaMem was detected in June 2024, when Black Lotus Labs identified suspicious traffic patterns associated with Versa Director servers at several U.S.-based ISPs and MSPs. The first confirmed exploitation occurred on June 12, 2024, targeting a U.S. ISP. Further analysis revealed that the attackers likely tested the web shell on non-U.S. targets before launching full-scale attacks on U.S. organizations.
Based on observed tactics, techniques, and procedures (TTPs), Black Lotus Labs attributes the exploitation of CVE-2024-39717 with moderate confidence to the Chinese state-sponsored APT groups Volt Typhoon and Bronze Silhouette. These groups are known for their focus on critical infrastructure and have a history of targeting network management systems to gain deeper access to their victims’ environments.
The ongoing exploitation of this vulnerability is of particular concern, as the attackers appear to be systematically targeting unpatched Versa Director systems. The potential impact of these attacks is significant, with the compromised systems providing attackers with a foothold into highly sensitive network management environments.
Organizations running Versa Director are strongly urged to upgrade to version 22.1.4 or later immediately. They should also review security advisories issued by Versa Networks and implement the recommended detection and mitigation measures.
Related Posts:
- Versa Networks Director GUI Flaw Under Active Attack, CISA Issues Urgent Patching Directive
- AVrecon RAT hidden in SOHO routers infected 70,000 devices in 20 countries in two years
- “TheMoon” Malware Returns: Thousands of Routers Compromised
- Unpatched Critical Flaw in VMware Cloud Director Appliances
- Chalubo Malware Wreaks Havoc: Half a Million Routers Permanently Disabled